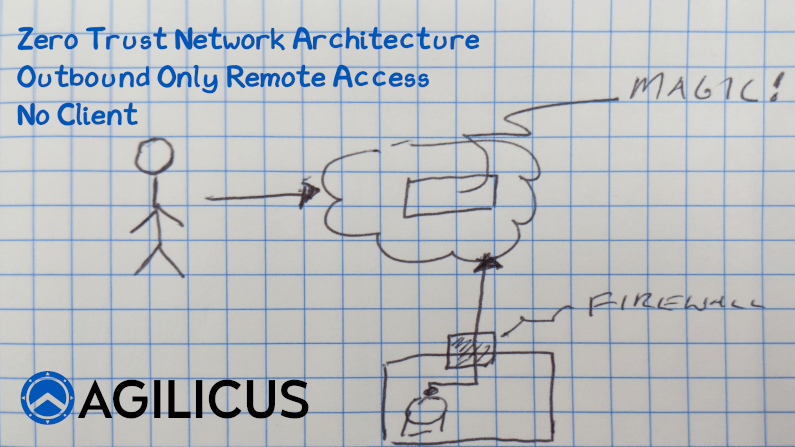
Zero Trust Network Access. The principle of managing security between a user and a resource, rather than a user and a perimeter. By Identifying the user, providing Authorisation in the network, and then remote access to individual resources, we increase security and simplify at the same time. But, did you know you can do this with 0 inbound connections open? Nothing. No ports open to see on a pentest, on nmap, on Shodan. How? In this video I explain. In a nutshell, the resource makes a permanent outbound connection to the cloud. The user makes an outbound connection to the same cloud. Identity is confirmed, Authorisation is confirmed. The connections are stitched together. Simple and secure, no reconfiguration of firewalls. No client VPN software.
Recent Articles
-
Apache Tomcat: Stealthy Risk Vector
-
Many Headed Hydra Medusa Meets Critical Infrastructure
-
It’s Been 0-Days Since The Last Municipal Cyber Security Attack
-
CN APT Use VPN CVE for ICS in OT: Acronym Much?
-
CityWorks CVE Breaches IIS
-
Come see us at the 2025 Texas Water Conference in the Innovation Lounge