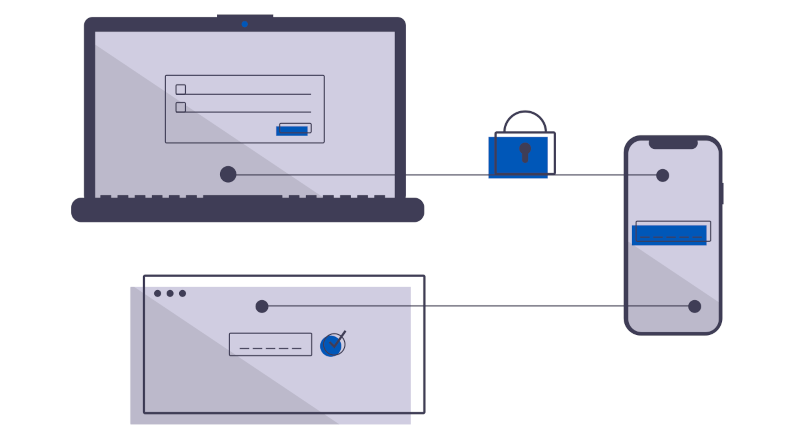
Your cyber insurance is up for review. If you can get all applications authenticated with multi-factor, you can afford it. But, you have only managed to get the new ones done, leaving the miscellaneous. Let’s talk about how an authenticating proxy can get the rest done, with no work, no fuss. Become compliant right quick.
Recent Articles
-
Krooked Kriminals Krack Krispy Kreme
-
Advice Avalanche: Practical Steps for Wastewater Treatment Plants
-
CityNews The Mike Farwell Show Interview
-
SolarWinds Gives Federal Agencies Labour Day Present
-
Operate Your Plant Virtually with Agilicus AnyX
-
10 Billion Reasons Shared Passwords Are Bad: RockYou2024