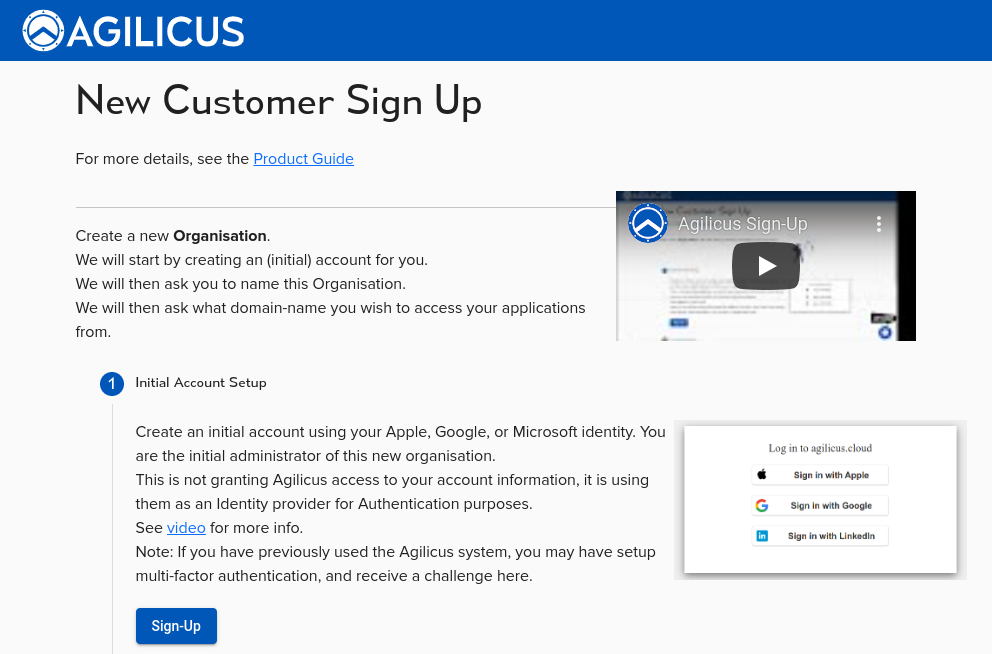
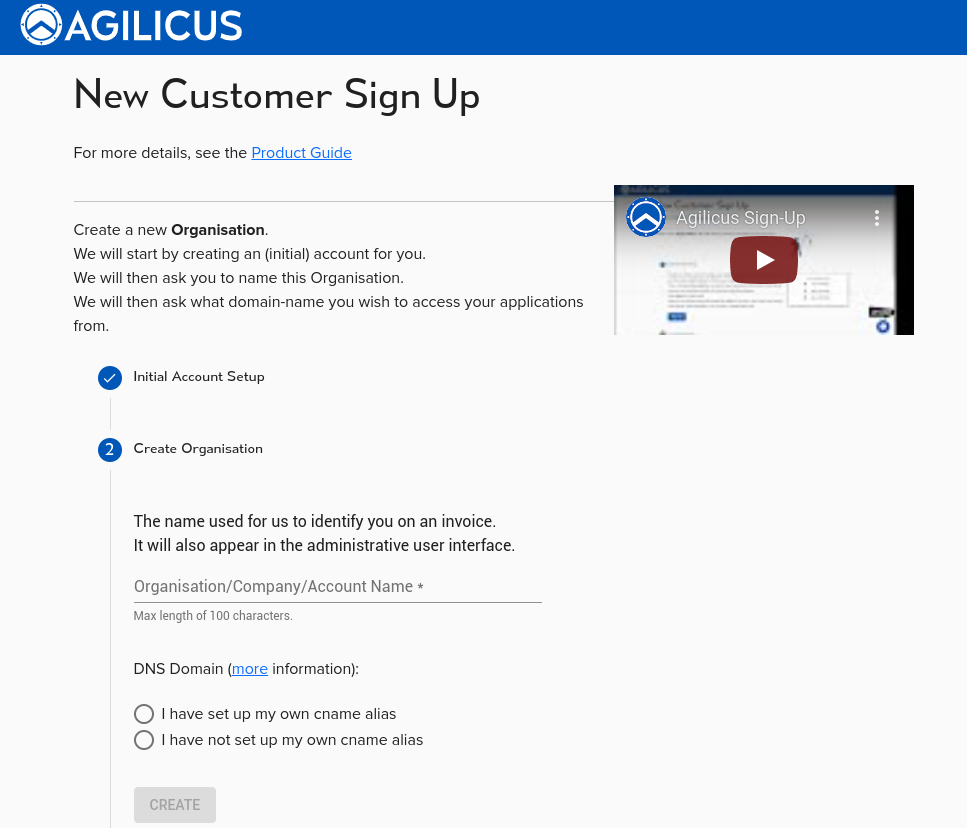
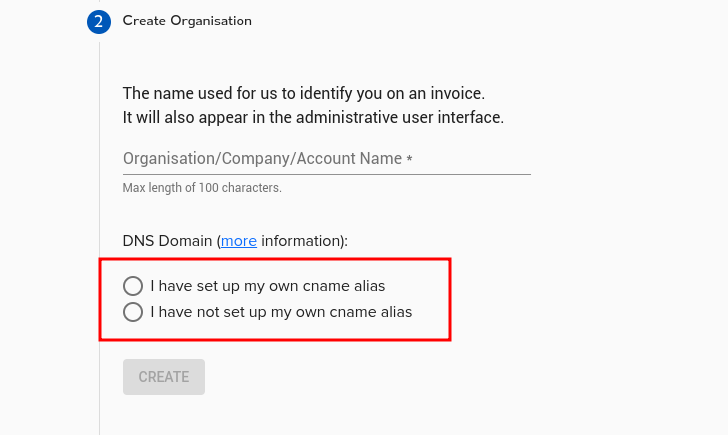
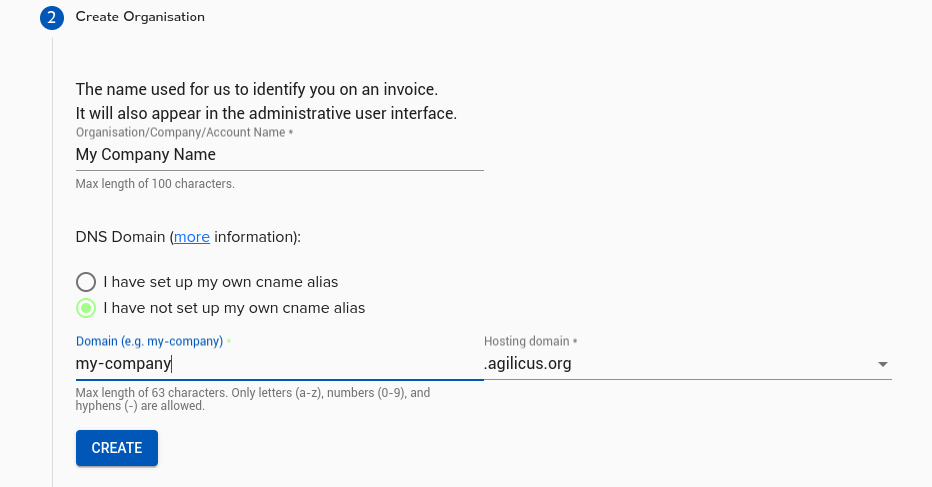
Time Synchronisation
Time Synchronisation
Accurate globally synced time is critical to the proper operation of many modern cryptographic tools. It affects certificte allocation/revocation, sign-in audit logs, etc.
The Agilicus system requires that your individual endpoints (browsers, Agent Connectors) have proper network time at all times. Typically this means enabling NTP.
During sign-in or installation you may see a warning indicating that your time is not accurate. Enable your time-sync service for your operating system to continue.
Linux
On systemd-derived Linux distributions, NTP is provided y the time-sync target. This in turn might use ntpd or chrony:
systemctl status time-sync.target
● time-sync.target - System Time Synchronized
Loaded: loaded (/lib/systemd/system/time-sync.target; static)
Active: active since Tue 2022-04-12 16:01:41 EDT; 1 month 19 days ago
Docs: man:systemd.special(7)You can check that your NTP is synced using one of these commands:
chronyc tracking
Reference ID : CF22301F (backoffice-1.incentre.net)
Stratum : 4
Ref time (UTC) : Wed Jun 01 14:11:18 2022
System time : 0.000066093 seconds fast of NTP time
Last offset : -0.000524711 seconds
RMS offset : 0.000274038 seconds
Frequency : 18.516 ppm slow
Residual freq : -0.004 ppm
Skew : 0.036 ppm
Root delay : 0.066371940 seconds
Root dispersion : 0.002734751 seconds
Update interval : 1035.0 seconds
Leap status : Normal$ ntpq -p
remote refid st t when poll reach delay offset jitter
==============================================================================
+muug.ca 132.163.97.1 2 u 377 1024 377 40.083 -2.270 3.861
-nowhere.zeromea 10.0.11.202 2 u 1066 1024 377 20.776 -13.097 11.333
*zero.gotroot.ca 30.114.5.31 2 u 979 1024 377 68.439 -3.066 2.814
+time.cloudflare 10.106.8.139 3 u 555 1024 377 36.048 -2.940 2.268Windows
Microsoft Windows uses the Windows Time Service, which in turn uses the Network Time Protocol (NTP) on UDP port 123.
You can force a one-time sync with:
w32tm /resyncSee Microsoft “Windows Time service tools and settings” for more information.
You can check your current NTP peers (your upstream time servers) with the below command:
C:\WINDOWS\system32>w32tm /query /peers
#Peers: 1
Peer: time.windows.com,0x9
State: Active
Time Remaining: 32683.0895075s
Mode: 3 (Client)
Stratum: 3 (secondary reference - syncd by (S)NTP)
PeerPoll Interval: 10 (1024s)
HostPoll Interval: 10 (1024s)
C:\WINDOWS\system32>w32tm /query /status
Leap Indicator: 0(no warning)
Stratum: 4 (secondary reference - syncd by (S)NTP)
Precision: -23 (119.209ns per tick)
Root Delay: 0.0464631s
Root Dispersion: 7.7952278s
ReferenceId: 0xA83DD74A (source IP: 168.61.215.74)
Last Successful Sync Time: 2022-06-01 10:09:57
Source: time.windows.com,0x9
Poll Interval: 10 (1024s)Embedded Devices
Embedded devices running e.g. Ubiquity EdgeMax, pfSense, OpenWRT, etc, all have their own NTP-enable. See their documentation or web/cli interface for more information.