Firewall Rules
Identity is “who” a user is.
Authentication is how a user “proves” their Identity
Authorisation is “what” a user is allowed to do. In the AnyX platform this is implemented via a set of firewall rules. For web applications, these have many options (method, path, body, who, etc).
The firewall rules are access via “Resources/Applications/Overview”, and then selecting the individual application, and navigating to the “Security” tab.
HTTP Rules
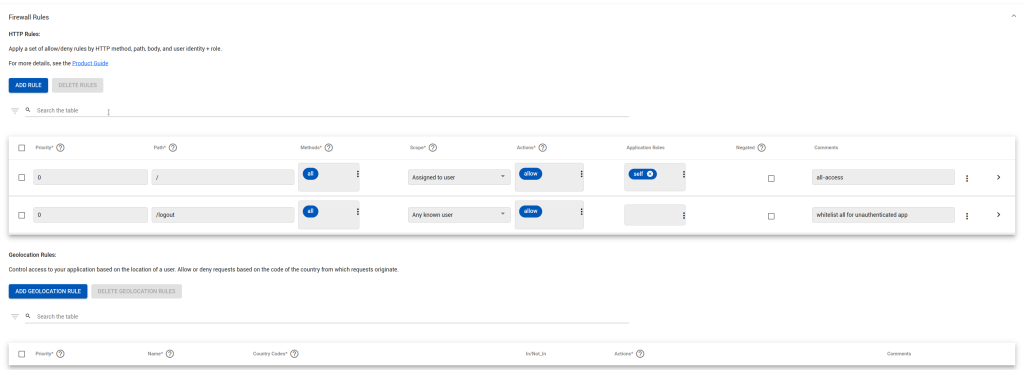
For web applications, HTTP rules allow matching on a set of conditions, and then performing a set of actions.
The conditions include:
- Priority. Rules are evaluated in order until a match occurs
- HTTP Path (the part after the host name in e.g. https://hostname/path).
- Method (e.g. GET, PUT, POST, DELETE, HEAD, …)
- Scope. One of “Assigned to User”, “Anyone”, “Any Known User”, “Any App User” (see Scopes below)
Methods are as defined in the HTTP standard (GET, PUT, POST, …). For most applications GET/HEAD will mean ‘read’, PUT will mean ‘create’, POST will mean ‘update’, and DELETE will mean remove a record.
Actions are Allow, Deny (and None, which can be used to disable a rule temporarily, or for debugging with logging).
Application Roles are defined per application, but often include ‘Self’ (my own records), ‘Owner’ (all, admin), ‘Editor’ (can change but not create/delete), ‘Viewer’ (can read).
Negated (the rule is inverted in sense, so whatever does *NOT* match).
Scopes
The scopes control what ‘type’ of user is matched by this rule. The scopes are:
- Assigned to User. The user must have a valid role within this application, and, that role is assigned (see Access/Application Permissions in admin)
- Anyone. Literally anyone on the Internet, regardless of who they are (e.g. Anonymous)
- Any Known User. Any user who exists in your org as a valid user.
- Any App User. Any user who was authenticated by this application (see Authentication/Application Identity. Note this is a rare case).
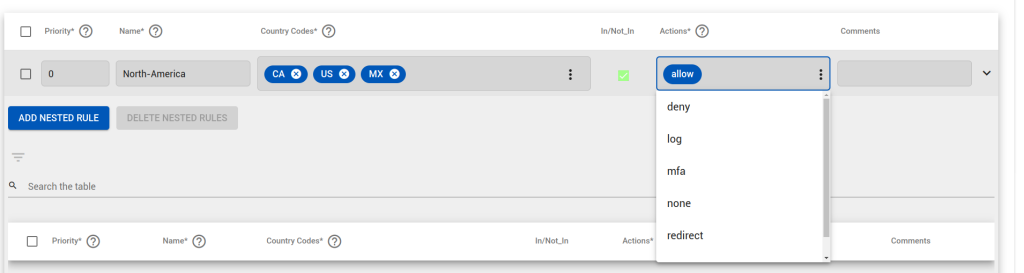
GeoIP Firewall
In some cases you may want to include only, or exclude only, specific countries from using a resource. You may do this by selecting the ISO 3166 country code for each locale, and then selecting IN/NOT_IN and action. The most common action (ALLOW, DENY) would fall-through to the other authorisation rules (ALLOW), or block entirely (DENY) regardless of user.