Overview
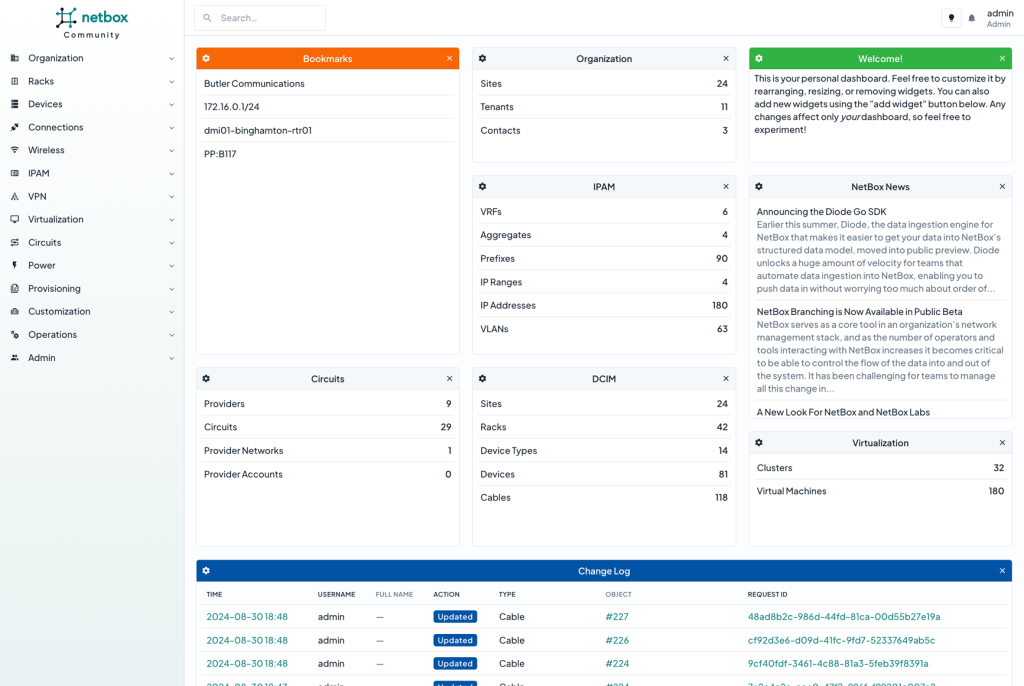
“NetBox is the leading solution for modeling and documenting modern networks.”. It can be simply run via e.g. a container or other methods.
In this example we show how to setup NetBox to be access by, and signed into by, Agilicus AnyX, providing secure remote access with single sign on.
Netbox setup
For this example, we are using the docker-compose environment https://github.com/netbox-community/netbox-docker of the community netbox-docker.
We modify the env/netbox.env file to add these lines:
CSRF_TRUSTED_ORIGINS="https://netbox.__MYDOMAIN__ http://localhost"
REMOTE_AUTH_ENABLED=True
REMOTE_AUTH_BACKEND='netbox.authentication.RemoteUserBackend'
REMOTE_AUTH_AUTO_CREATE_USER=True
REMOTE_AUTH_AUTO_CREATE_GROUPS=True
REMOTE_AUTH_GROUP_SYNC_ENABLED=True
REMOTE_AUTH_HEADER=HTTP_X_GATEWAY_USER_EMAIL
REMOTE_AUTH_GROUP_HEADER=HTTP_X_GATEWAY_PRIMARY_ROLE
REMOTE_AUTH_DEFAULT_GROUPS=adminThese headers for REMOTE_AUTH_* are documented here: https://netboxlabs.com/docs/netbox/en/stable/configuration/remote-authentication.
The CSRF_TRUSTED_ORIGINS allows the Agilicus external name to be allowed to sign in.
Once we have done this, we run docker compose up, and, NetBox is now running.
From here, assuming we already have a connector installed, we can create an application following the below steps. All except the last step are done through the ‘Resources/Applications/New’ stepper. The last step (enabling User Context headers), navigate to Resources/Applications/Overview, and select your new application, then select the Proxy header.
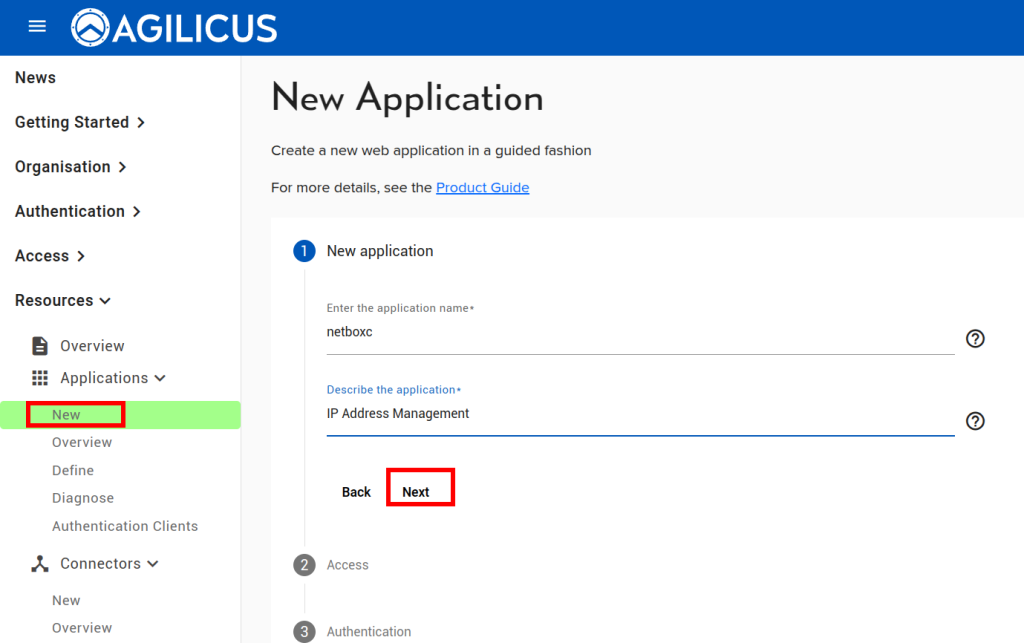
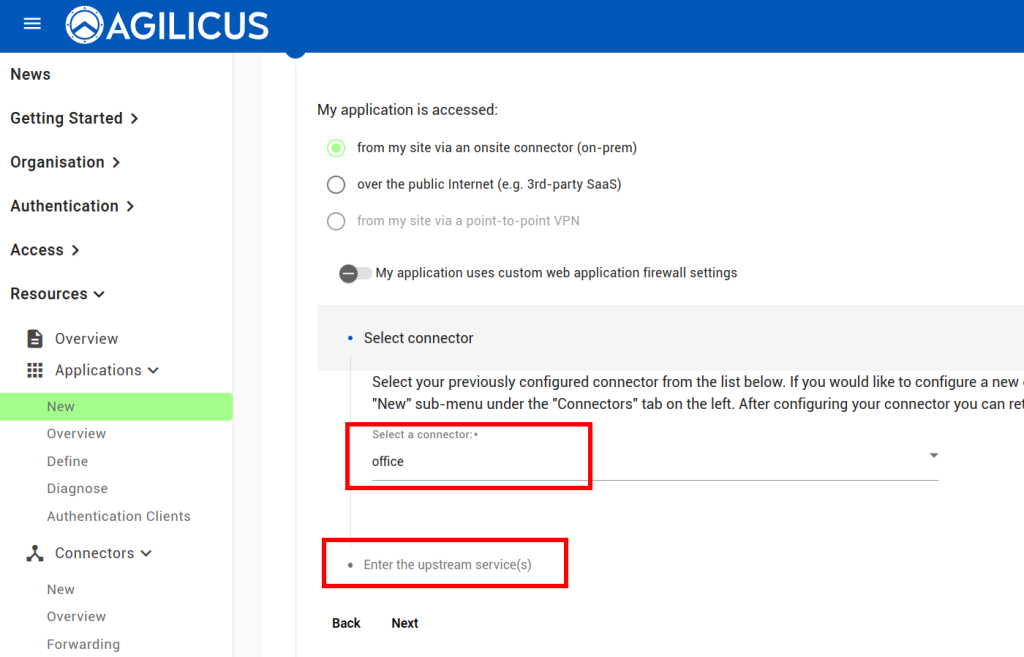
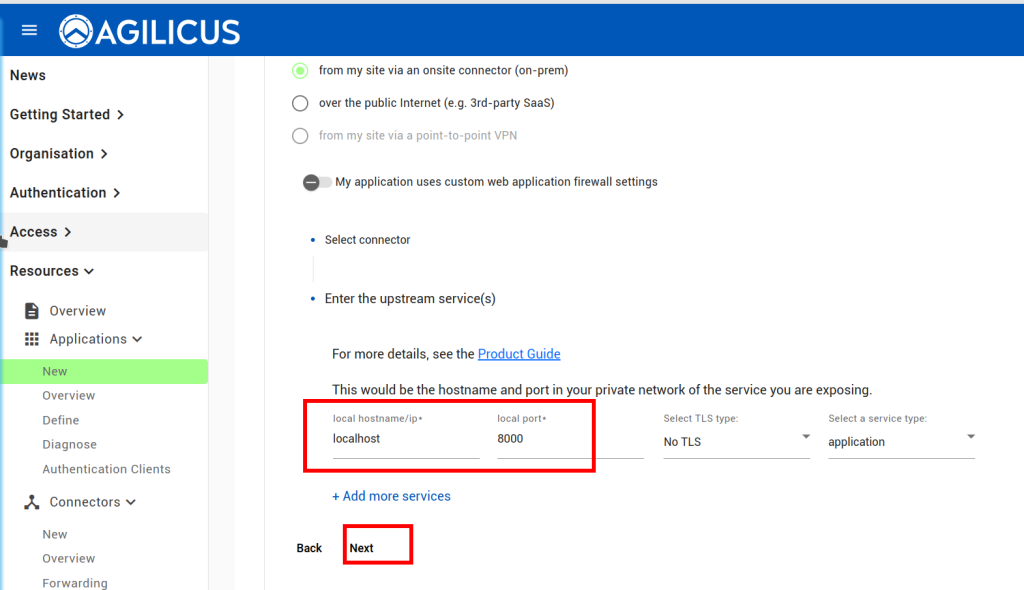
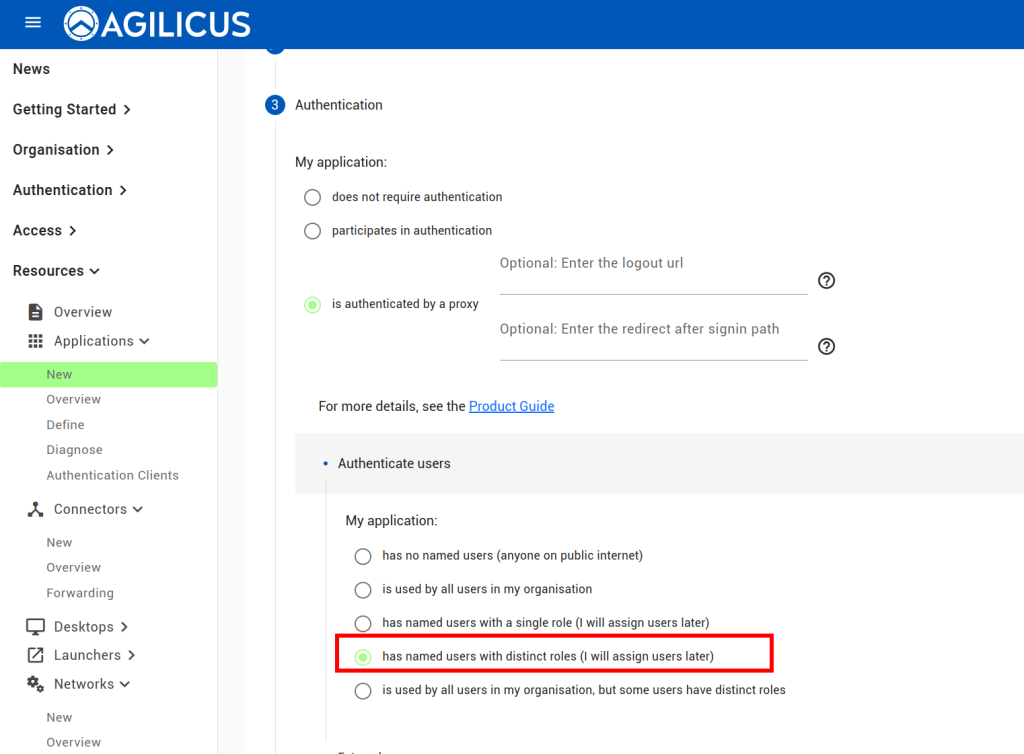
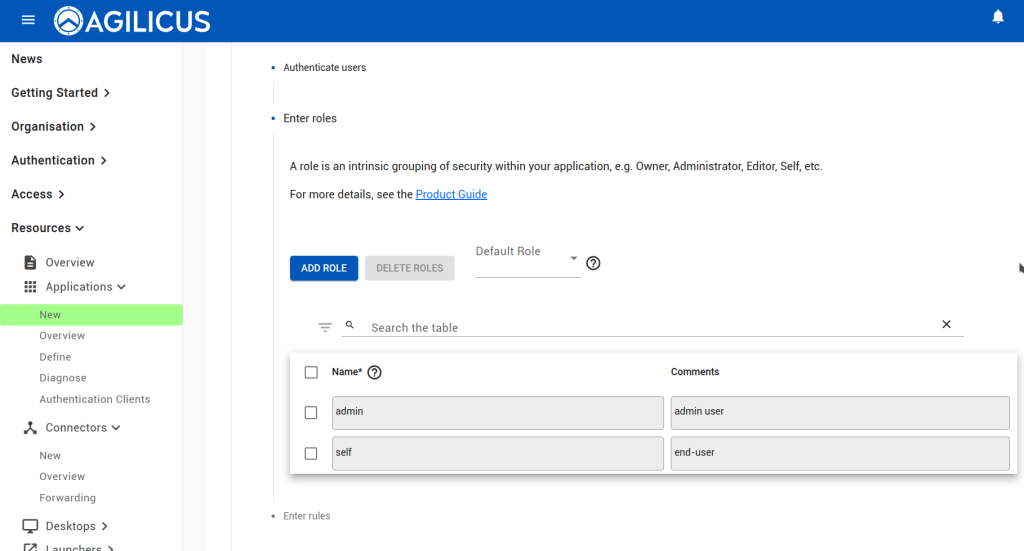
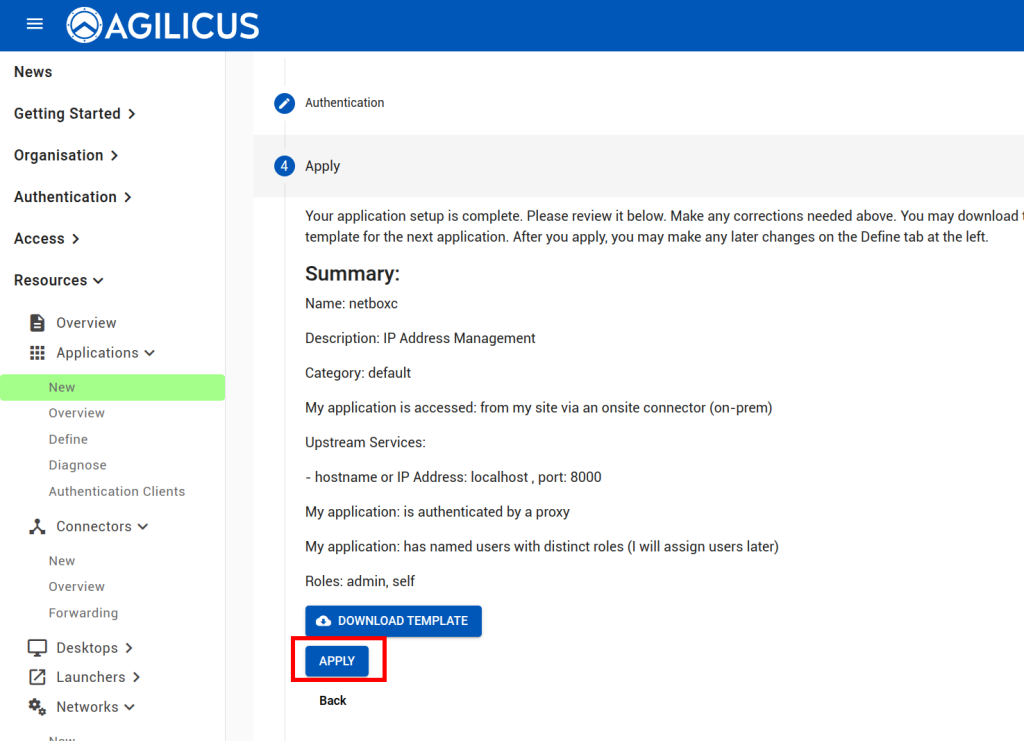
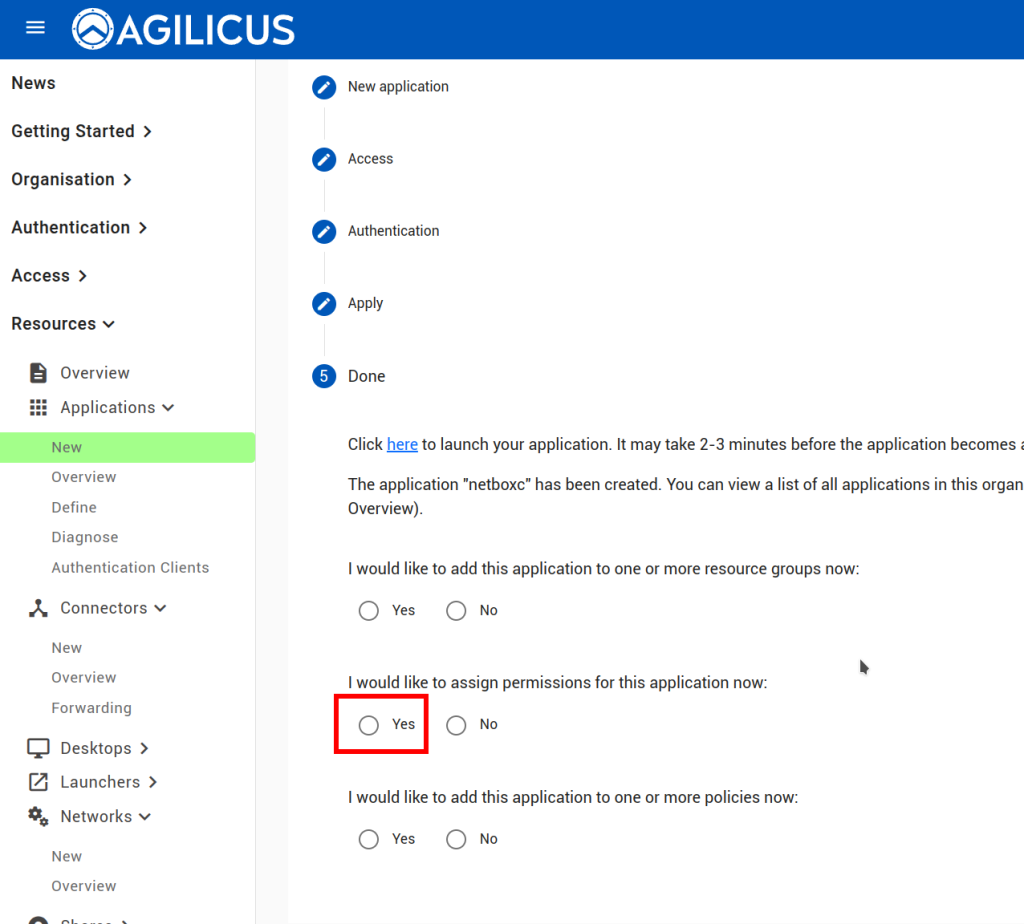
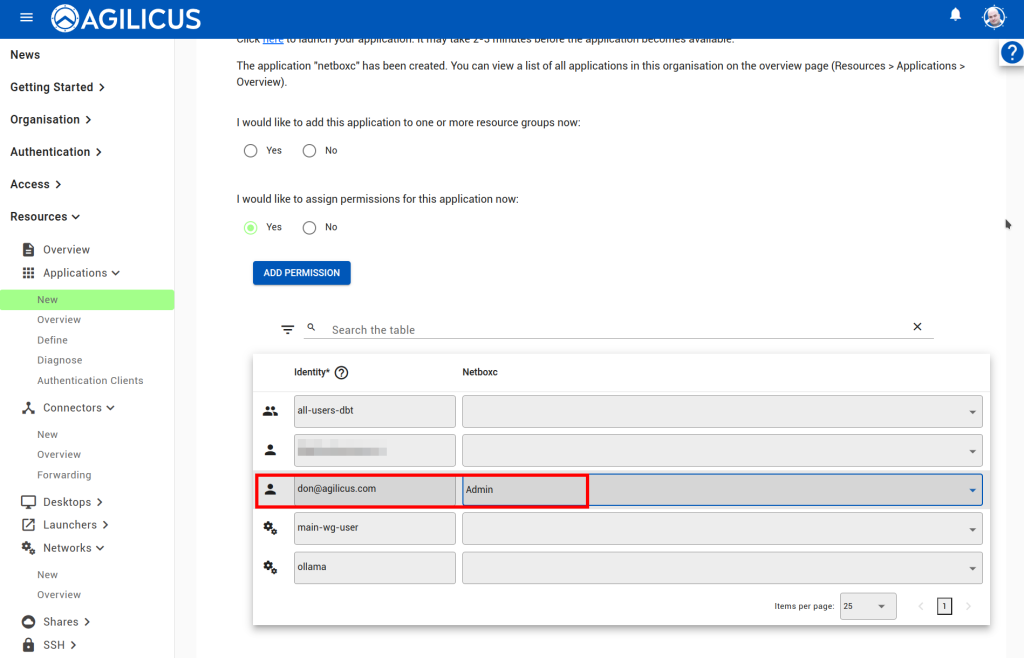
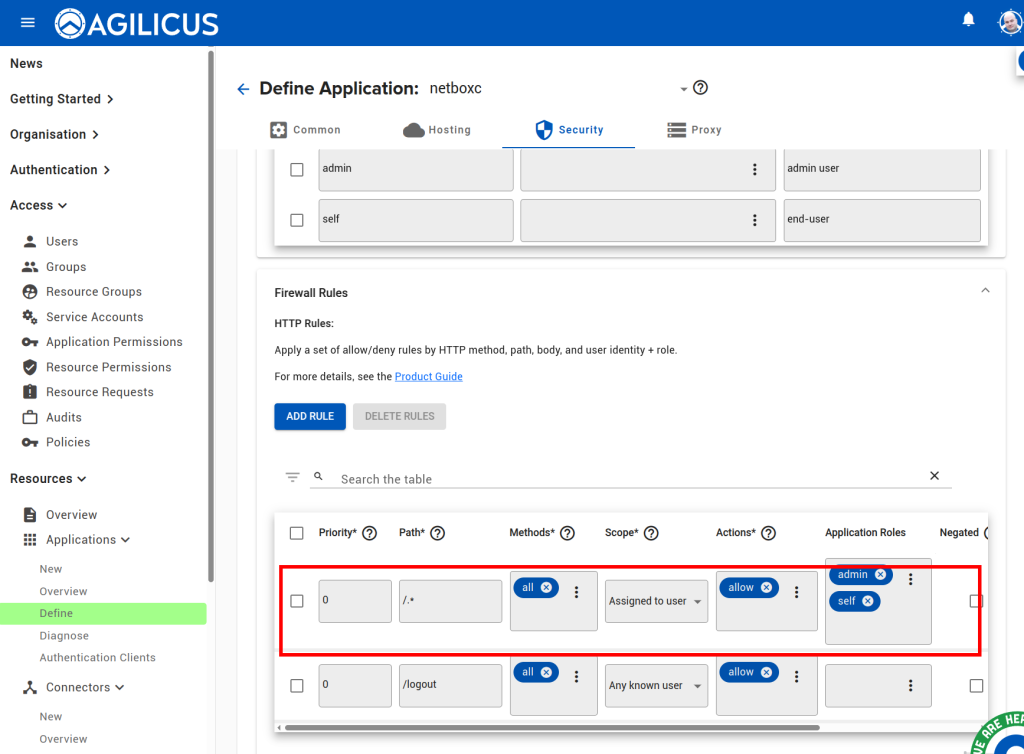
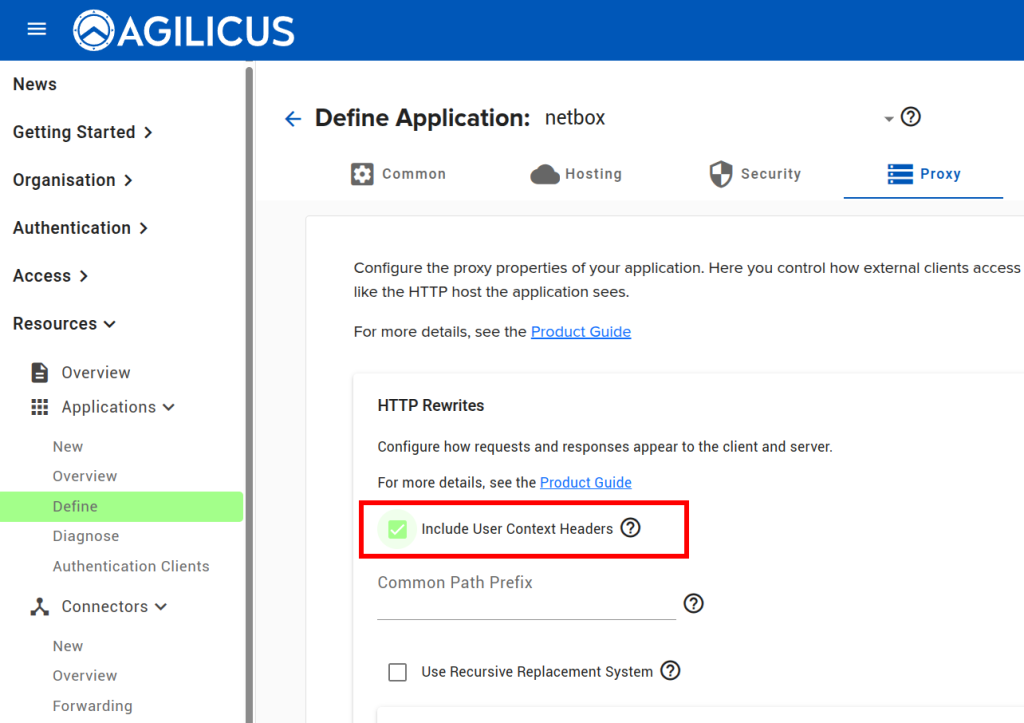
At this stage, you should be able to navigate to https://netbox.__MYDOMAIN__ (or, https://profile.__MYDOMAIN__ and see the icon). You should be auto-logged in as a user in the admin group. You can later add users to Agilicus AnyX permissions with ‘self’ or ‘admin’ to give control of what they can do in netbox. Add additional groups if desired.
NOTE: since we chose the ‘multiple roles’ option in the stepper, we must manually configure the firewall rule, allowing each of the roles full HTTP access, and then allowing NetBox to decide what sub-permissions to do based on group.