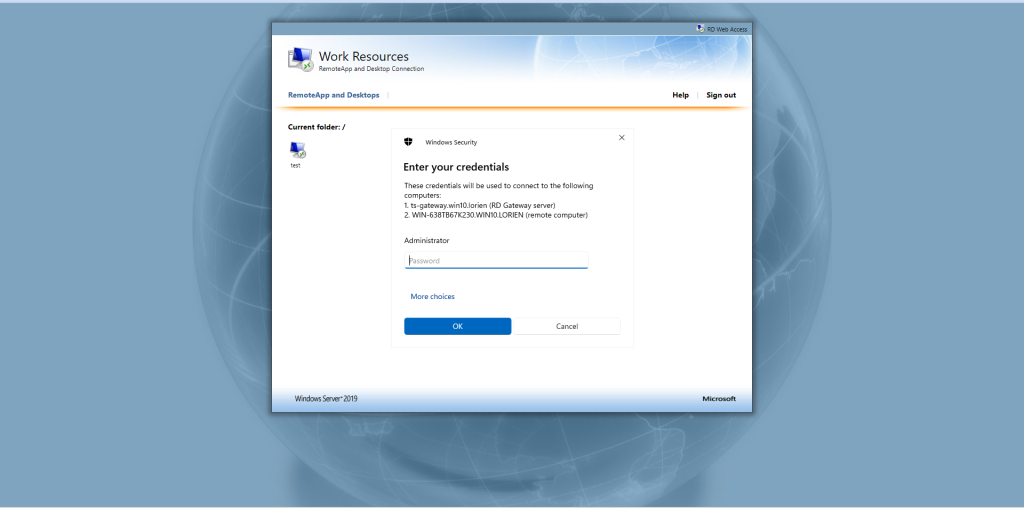
Exposing a Remote Desktop Gateway through a Launcher
This guide will walk you through configuring your machine to access desktops using a Remote Desktop gateway via an Agilicus Connector.
NOTE: This is an unusual setup, normally you use the Desktop feature of Agilicus directly without Microsoft RD Web.
Overview
This guide will walk you through configuring your machine to access desktops using a Remote Desktop gateway via an Agilicus Connector. This allows you to use Microsoft Remote Desktop Gateway on a hidden internal network without opening a firewall rule or port-forward or VPN.
This technique involves creating a network to represent Remote Desktop Services then creating a launcher which will open mstsc.exe such that it will proxy all requests to the Remote Desktop gateway through Agilicus. Only users with permission to the launcher will have access to the Remote Desktop gateway. The .rdp extension will be associated with the launcher so that opening the file after downloading it from the RD Web portal will invoke the launcher, allowing it to properly access the Remote Desktop gateway. Users can download the RDP files from the normal RD Web portal, protected by Agilicus, using an Application you configure.
Configuring the Launcher
Create a resource group called ts-gateways. Then create a network called ts-gateway-1. Add it to the
ts-gateways resource group.
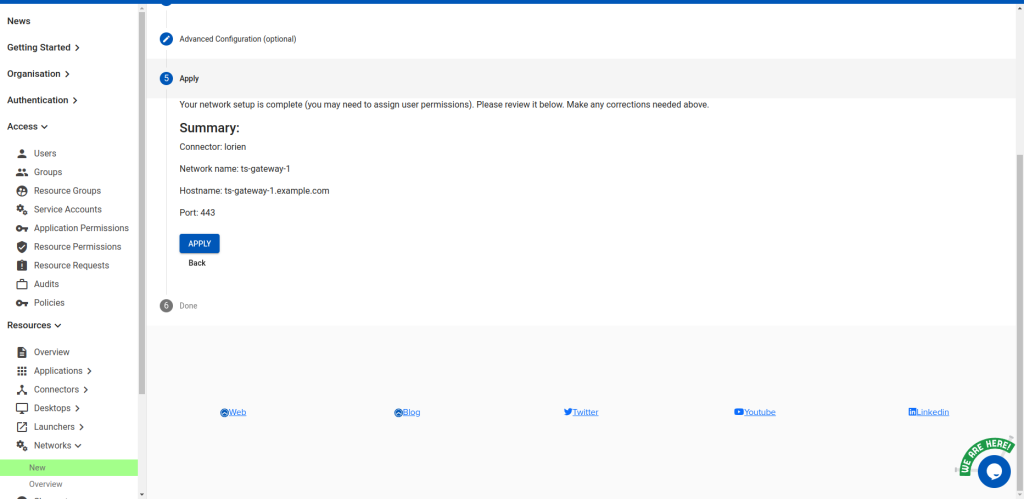
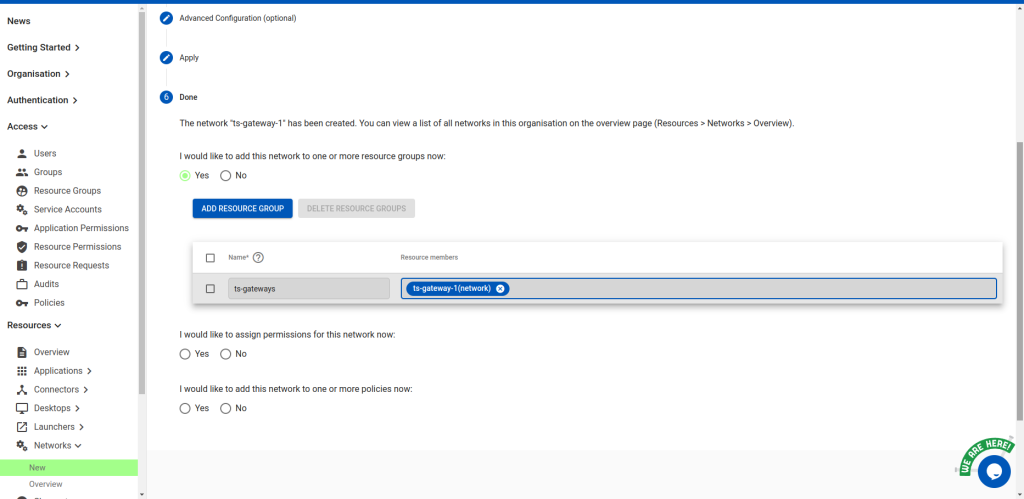
Note: if you have multiple gateways, repeat this process for each. Increment the -1 (e.g. ts-gateway-2,
ts-gateway-3). This naming scheme is just an example; you can use your own to match your
organisation’s naming scheme.
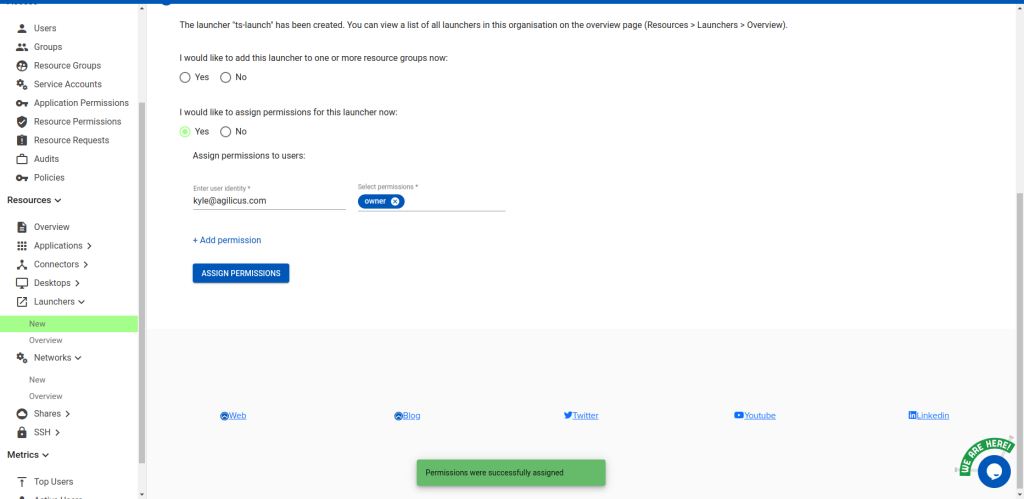
Next, create a launcher called ts-launch, pointing to C:\Windows\system32\mstsc.exe, containing the ts-gateways resource
group. Give yourself and any others you want ‘owner’ permission to it.
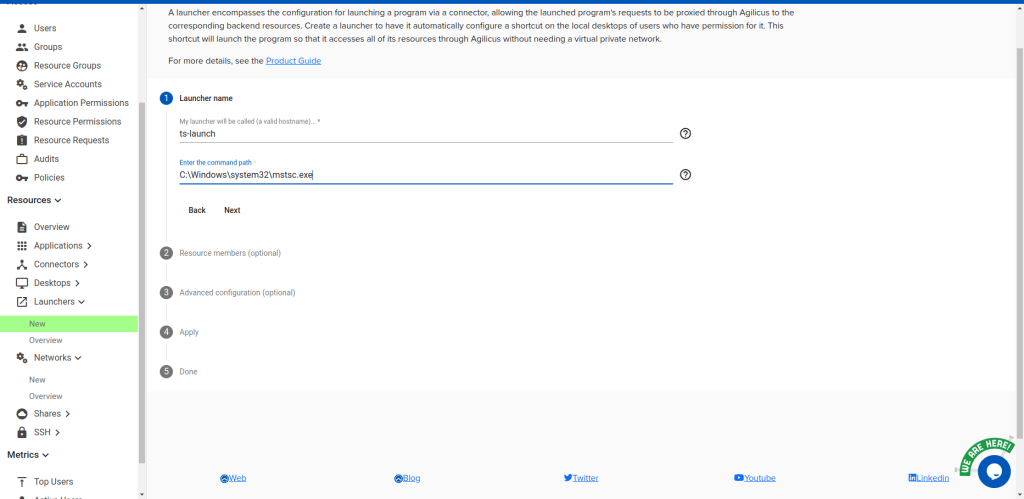
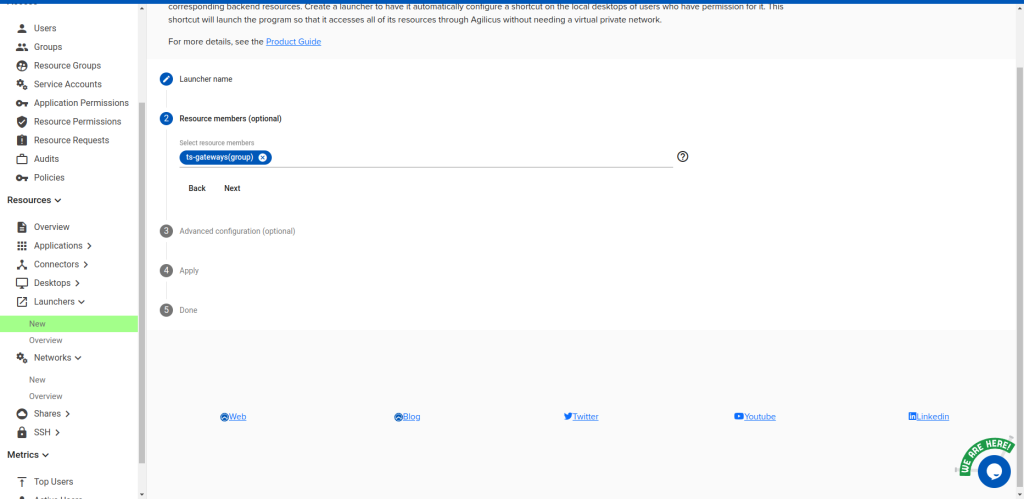
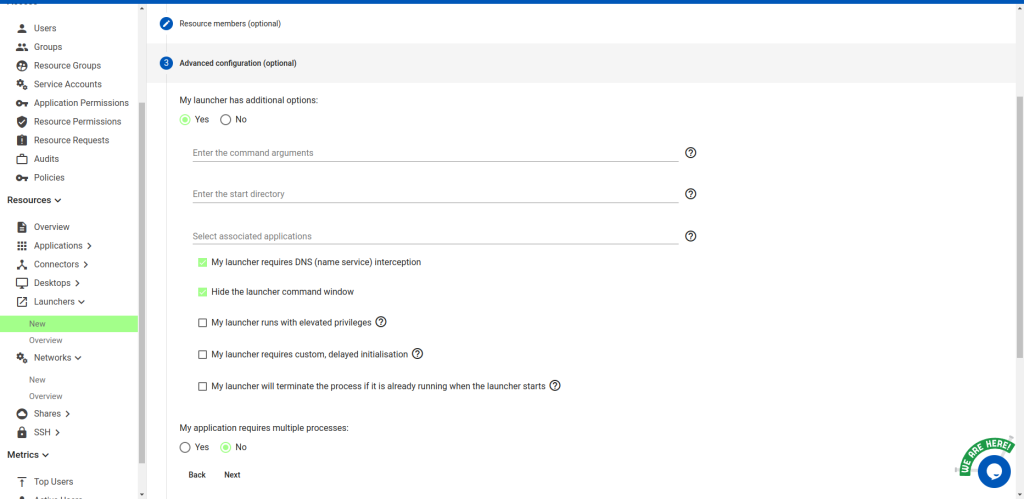
Under “Advanced configuration”, select “My launcher has additional options” and then check “My
launcher requires DNS (name service) interception” and “Hide the launcher command window”. Select
“No” for “My application requires multiple processes”
Configuring the Client Desktop
Here we ensure the launcher is present on the desktop, and configure the desktop via the registry to point RDP files to the launcher.
If the launcher is not installed, do so now. Otherwise, run the Agilicus Refresh tool to install the new launcher shortcut. From that we’ll find two pieces of information needed to populate some registry entries. Navigate to the Agilicus\Launchers Start Menu entry and edit the properties of the shortcut. We’re interested in the “Target” field.
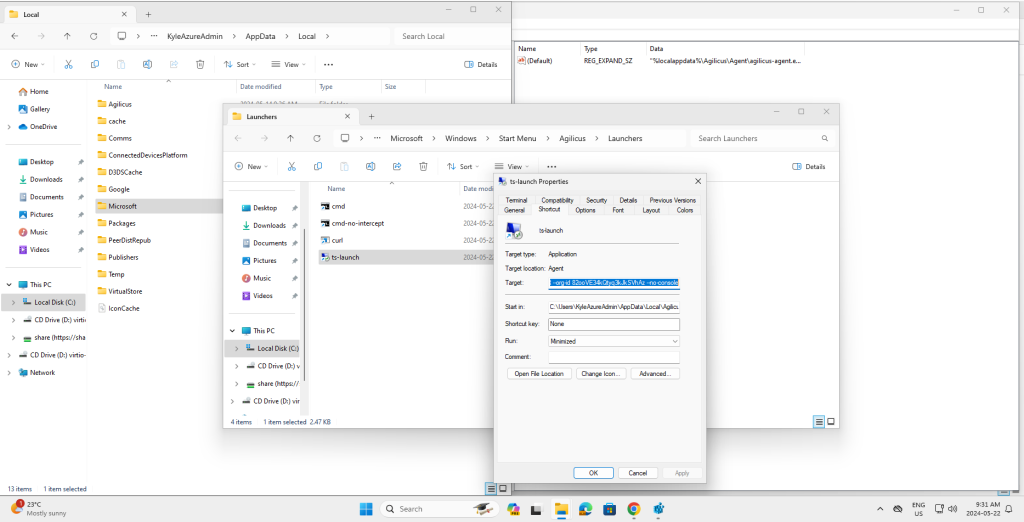
Note down the strings after –launcher id and –org-id. In my case:
C:\Users\Kyle\AppData\Local\Agilicus\Agent\agilicus-agent.exe proxify --cfg-file
C:\Users\Kyle\AppData\Local\Agilicus\Agent\agent.conf.enc.yaml --launcher-id
epQEX8vj9wdo8B4iYcCTPT --org-id 82ooVE34kQtyq3kJkSVhAz --no-consoleFrom which I extract:
- launcher-id: epQEX8vj9wdo8B4iYcCTPT
- org-id: 82ooVE34kQtyq3kJkSVhAz
Next, import the registry template by loading the following rdp-launcher-template.rdp file and answering
yes. This will insert registry entries controlling the default assocation for rdp files. You will then modify
the added entries to point to the launcher you configured earlier.
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Classes\RDP.File]
@="Remote Desktop Connection"
"AppUserModelId"="Microsoft.Windows.RemoteDesktop"
"EditFlags"=dword:00100000
"FriendlyTypeName"=hex(2):40,00,25,00,73,00,79,00,73,00,74,00,65,00,6d,00,72
,\
00,6f,00,6f,00,74,00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,\
32,00,5c,00,6d,00,73,00,74,00,73,00,63,00,2e,00,65,00,78,00,65,00,2c,00,2d,\
00,34,00,30,00,30,00,34,00,00,00
[HKEY_CURRENT_USER\Software\Classes\RDP.File\DefaultIcon]
@=hex(2):25,00,73,00,79,00,73,00,74,00,65,00,6d,00,72,00,6f,00,6f,00,74,00,2
5,\
00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,6d,00,73,00,\
74,00,73,00,63,00,2e,00,65,00,78,00,65,00,00,00
[HKEY_CURRENT_USER\Software\Classes\RDP.File\shell]
@="Connect"
[HKEY_CURRENT_USER\Software\Classes\RDP.File\shell\Connect]
@="Connect"
"MUIVerb"=hex(2):40,00,25,00,73,00,79,00,73,00,74,00,65,00,6d,00,72,00,6f,00
,\
6f,00,74,00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,\
00,6d,00,73,00,74,00,73,00,63,00,2e,00,65,00,78,00,65,00,2c,00,2d,00,34,00,\
30,00,30,00,32,00,00,00
[HKEY_CURRENT_USER\Software\Classes\RDP.File\shell\Connect\command]@=hex(2):22,00,25,00,6c,00,6f,00,63,00,61,00,6c,00,61,00,70,00,70,00,64,00,6
1,\
00,74,00,61,00,25,00,5c,00,41,00,67,00,69,00,6c,00,69,00,63,00,75,00,73,00,\
5c,00,41,00,67,00,65,00,6e,00,74,00,5c,00,61,00,67,00,69,00,6c,00,69,00,63,\
00,75,00,73,00,2d,00,61,00,67,00,65,00,6e,00,74,00,2e,00,65,00,78,00,65,00,\
22,00,20,00,70,00,72,00,6f,00,78,00,69,00,66,00,79,00,20,00,2d,00,2d,00,63,\
00,66,00,67,00,2d,00,66,00,69,00,6c,00,65,00,20,00,22,00,25,00,6c,00,6f,00,\
63,00,61,00,6c,00,61,00,70,00,70,00,64,00,61,00,74,00,61,00,25,00,5c,00,41,\
00,67,00,69,00,6c,00,69,00,63,00,75,00,73,00,5c,00,41,00,67,00,65,00,6e,00,\
74,00,5c,00,61,00,67,00,65,00,6e,00,74,00,2e,00,63,00,6f,00,6e,00,66,00,2e,\
00,65,00,6e,00,63,00,2e,00,79,00,61,00,6d,00,6c,00,22,00,20,00,2d,00,2d,00,\
6c,00,61,00,75,00,6e,00,63,00,68,00,65,00,72,00,2d,00,69,00,64,00,20,00,3c,\
00,79,00,6f,00,75,00,72,00,5f,00,6c,00,61,00,75,00,6e,00,63,00,68,00,65,00,\
72,00,5f,00,69,00,64,00,3e,00,20,00,2d,00,2d,00,6f,00,72,00,67,00,2d,00,69,\
00,64,00,20,00,3c,00,79,00,6f,00,75,00,72,00,5f,00,6f,00,72,00,67,00,5f,00,\
69,00,64,00,3e,00,20,00,2d,00,2d,00,6e,00,6f,00,2d,00,63,00,6f,00,6e,00,73,\
00,6f,00,6c,00,65,00,20,00,2d,00,2d,00,20,00,22,00,25,00,31,00,22,00,00,00
[HKEY_CURRENT_USER\Software\Classes\RDP.File\shell\Edit]
@="Edit"
"MUIVerb"=hex(2):40,00,25,00,73,00,79,00,73,00,74,00,65,00,6d,00,72,00,6f,00
,\
6f,00,74,00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,\
00,6d,00,73,00,74,00,73,00,63,00,2e,00,65,00,78,00,65,00,2c,00,2d,00,34,00,\
30,00,30,00,33,00,00,00
[HKEY_CURRENT_USER\Software\Classes\RDP.File\shell\Edit\command]@=hex(2):22,00,25,00,6c,00,6f,00,63,00,61,00,6c,00,61,00,70,00,70,00,64,00,6
1,\
00,74,00,61,00,25,00,5c,00,41,00,67,00,69,00,6c,00,69,00,63,00,75,00,73,00,\
5c,00,41,00,67,00,65,00,6e,00,74,00,5c,00,61,00,67,00,69,00,6c,00,69,00,63,\
00,75,00,73,00,2d,00,61,00,67,00,65,00,6e,00,74,00,2e,00,65,00,78,00,65,00,\
22,00,20,00,70,00,72,00,6f,00,78,00,69,00,66,00,79,00,20,00,2d,00,2d,00,63,\
00,66,00,67,00,2d,00,66,00,69,00,6c,00,65,00,20,00,22,00,25,00,6c,00,6f,00,\
63,00,61,00,6c,00,61,00,70,00,70,00,64,00,61,00,74,00,61,00,25,00,5c,00,41,\
00,67,00,69,00,6c,00,69,00,63,00,75,00,73,00,5c,00,41,00,67,00,65,00,6e,00,\
74,00,5c,00,61,00,67,00,65,00,6e,00,74,00,2e,00,63,00,6f,00,6e,00,66,00,2e,\
00,65,00,6e,00,63,00,2e,00,79,00,61,00,6d,00,6c,00,22,00,20,00,2d,00,2d,00,\
6c,00,61,00,75,00,6e,00,63,00,68,00,65,00,72,00,2d,00,69,00,64,00,20,00,3c,\
00,79,00,6f,00,75,00,72,00,5f,00,6c,00,61,00,75,00,6e,00,63,00,68,00,65,00,\
72,00,5f,00,69,00,64,00,3e,00,20,00,2d,00,2d,00,6f,00,72,00,67,00,2d,00,69,\
00,64,00,20,00,3c,00,79,00,6f,00,75,00,72,00,5f,00,6f,00,72,00,67,00,5f,00,\
69,00,64,00,3e,00,20,00,2d,00,2d,00,6e,00,6f,00,2d,00,63,00,6f,00,6e,00,73,\
00,6f,00,6c,00,65,00,20,00,2d,00,2d,00,20,00,2d,00,65,00,64,00,69,00,74,00,\
20,00,22,00,25,00,31,00,22,00,00,00
[HKEY_CURRENT_USER\Software\Classes\RDP.File\shell\Open]
"Extended"=""
[HKEY_CURRENT_USER\Software\Classes\RDP.File\shell\Open\command]
@=hex(2):22,00,25,00,6c,00,6f,00,63,00,61,00,6c,00,61,00,70,00,70,00,64,00,6
1,\
00,74,00,61,00,25,00,5c,00,41,00,67,00,69,00,6c,00,69,00,63,00,75,00,73,00,\5c,00,41,00,67,00,65,00,6e,00,74,00,5c,00,61,00,67,00,69,00,6c,00,69,00,63,\
00,75,00,73,00,2d,00,61,00,67,00,65,00,6e,00,74,00,2e,00,65,00,78,00,65,00,\
22,00,20,00,70,00,72,00,6f,00,78,00,69,00,66,00,79,00,20,00,2d,00,2d,00,63,\
00,66,00,67,00,2d,00,66,00,69,00,6c,00,65,00,20,00,22,00,25,00,6c,00,6f,00,\
63,00,61,00,6c,00,61,00,70,00,70,00,64,00,61,00,74,00,61,00,25,00,5c,00,41,\
00,67,00,69,00,6c,00,69,00,63,00,75,00,73,00,5c,00,41,00,67,00,65,00,6e,00,\
74,00,5c,00,61,00,67,00,65,00,6e,00,74,00,2e,00,63,00,6f,00,6e,00,66,00,2e,\
00,65,00,6e,00,63,00,2e,00,79,00,61,00,6d,00,6c,00,22,00,20,00,2d,00,2d,00,\
6c,00,61,00,75,00,6e,00,63,00,68,00,65,00,72,00,2d,00,69,00,64,00,20,00,3c,\
00,79,00,6f,00,75,00,72,00,5f,00,6c,00,61,00,75,00,6e,00,63,00,68,00,65,00,\
72,00,5f,00,69,00,64,00,3e,00,20,00,2d,00,2d,00,6f,00,72,00,67,00,2d,00,69,\
00,64,00,20,00,3c,00,79,00,6f,00,75,00,72,00,5f,00,6f,00,72,00,67,00,5f,00,\
69,00,64,00,3e,00,20,00,2d,00,2d,00,6e,00,6f,00,2d,00,63,00,6f,00,6e,00,73,\
00,6f,00,6c,00,65,00,20,00,2d,00,2d,00,20,00,22,00,25,00,31,00,22,00,00,00After importing the registry template, open regedit.exe. and navigate to
Computer\HKEY_CURRENT_USER\Software\Classes\RDP.File
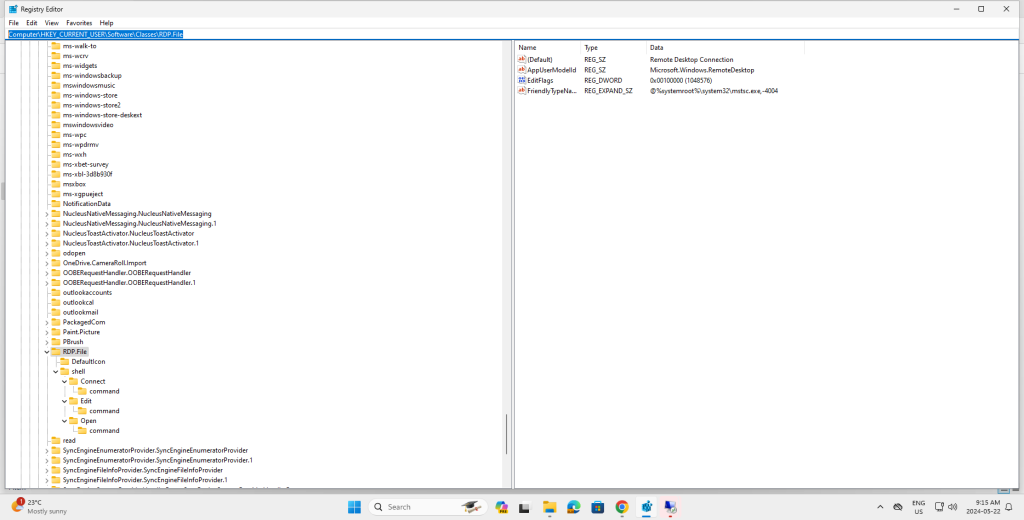
Proceed to edit the Default value in each of Connect\command, Edit\command and Open\command,
replacing <your_launcher_id> with the launcher-id you noted earlier, and <your_org_id> with the
org-id you noted earlier.
For example, consider the following Connect key:
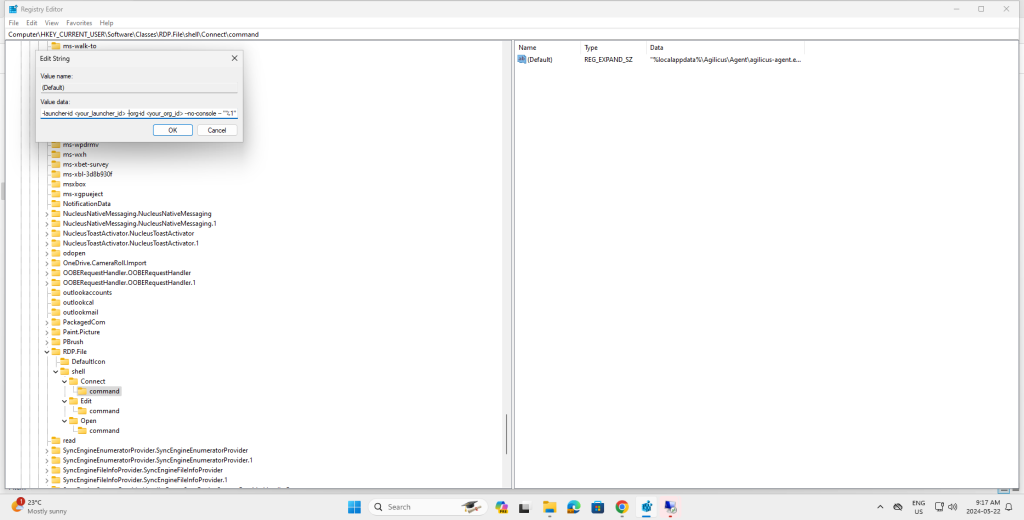
Turns into:
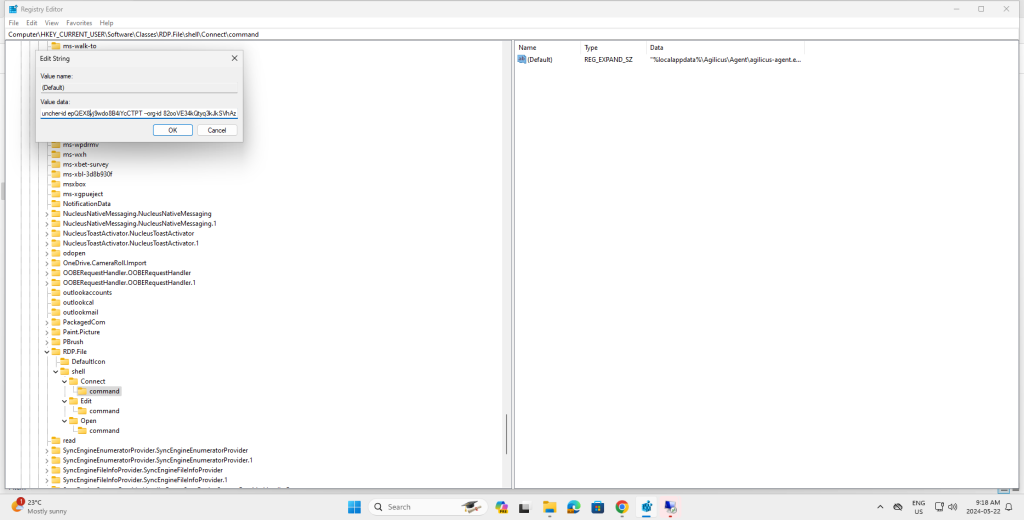
With this in place, RDP files will by default invoke the launcher, which will in turn invoke mstsc.exe.
Configuring the RD Web Access
In order to grant access to the RD Web Access portal, you will create an application in Agilicus. Create
an application called ts-gateway. Again, this name is just an example. You can call the application
something meaningful to your organisation.
Under access, point it at your Remote Desktop Services gateway’s web portal from a connector with access to it.
Select “Service is accessed via TLS and verify” for the TLS type.
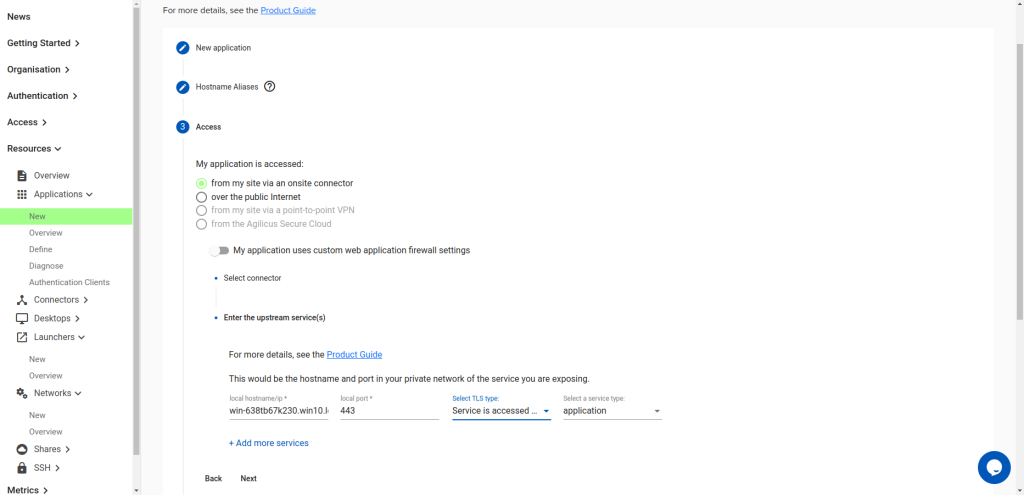
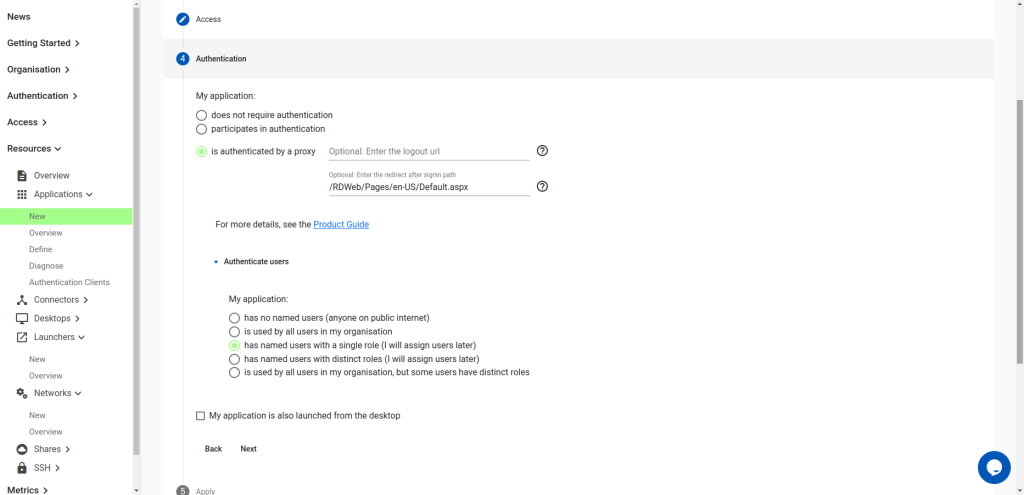
Under Authentication, choose:
- is authenticated by a proxy
- for redirect after signin path, enter the aboslute path of landing page of the gateway. E.g.
/RDWeb/Pages/en-US/Default.aspx - Do not choose “My application is also launched from the desktop”
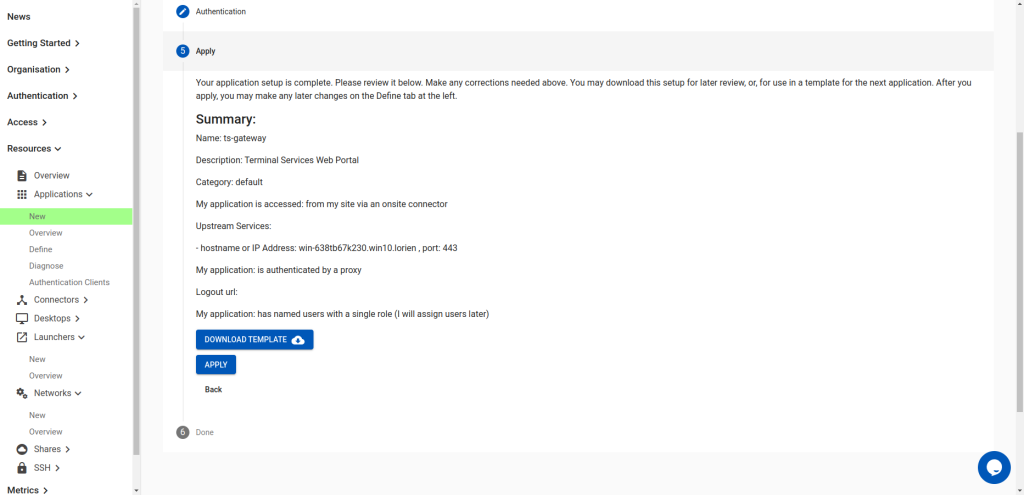
Now apply the application:
Navigate to the application’s definition. Under Security, scroll to “Firewall Rules”. Modify the / rule to be ^/RDWeb/
Then navigate to the Proxy Tab. Open up the HTTP Rewrites panel, and then the Rewrite Media Types
panel. In there, add two media types:
- application/json
- application/x-rdp
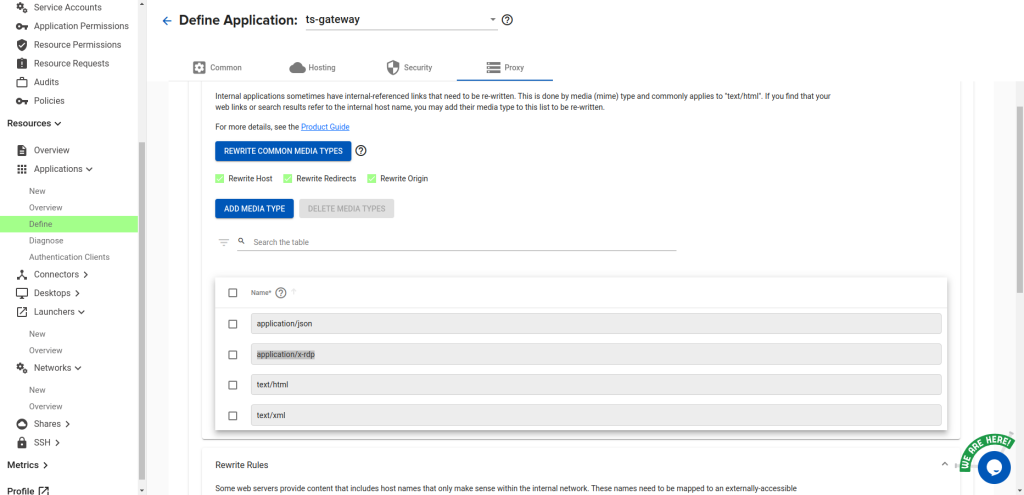
Set the “Common Path Prefix” to /RDWeb/Pages/en-US/Default.aspx
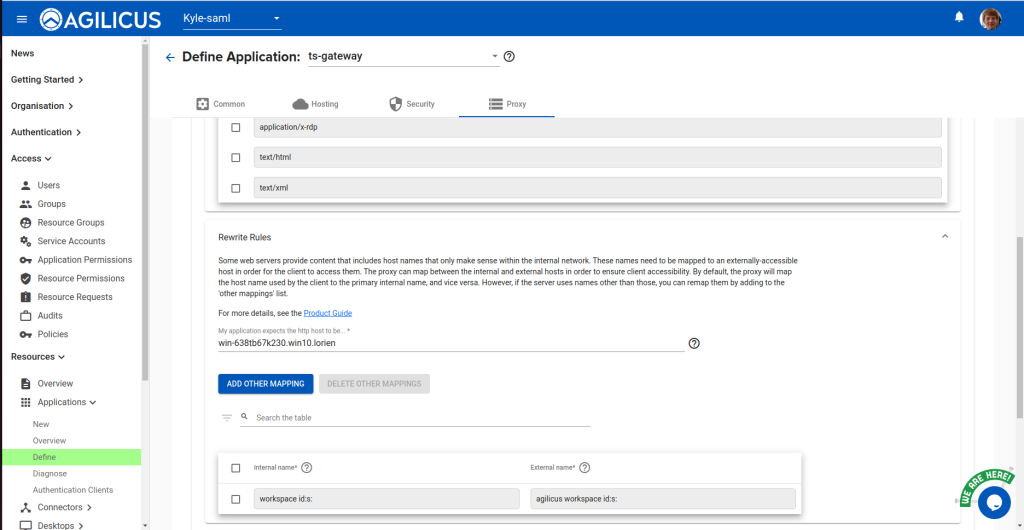
Then, scroll down to the Rewrite Rules. Add the following mapping:
- Internal Name:
workspace id:s: - External Name:
agilicus workspace id:s:
Next, create a group called “ts-gateway-users”, and add any users you would like to have access:
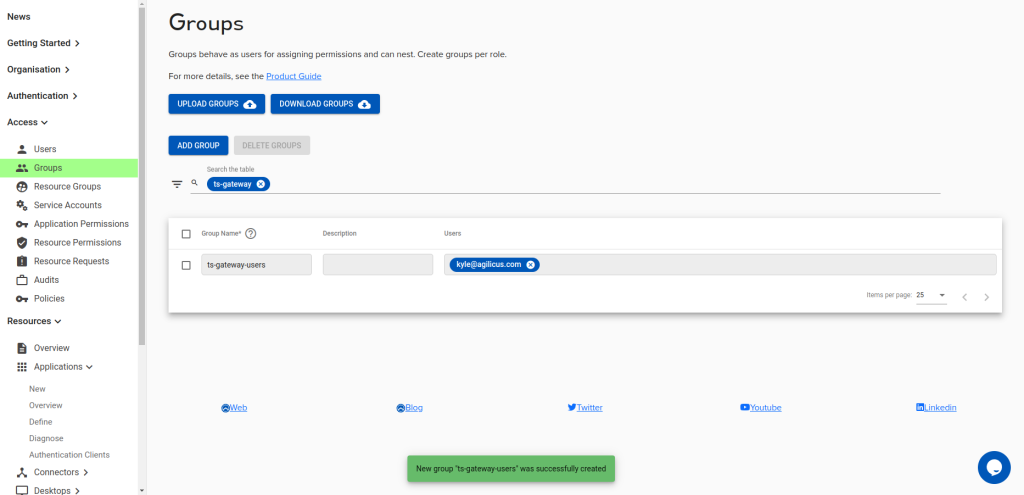
Under Application Permissions, assign the ‘self’ role to the ts-gateway-users group.
Using the RD Web Portal
You can now access the portal from the ts-gateway. URL. You can also launch this
from profile. E.g. If you have multiple gateways, repeat this process for each, giving them a unique and descriptive name
(so that your users can choose the correct one).
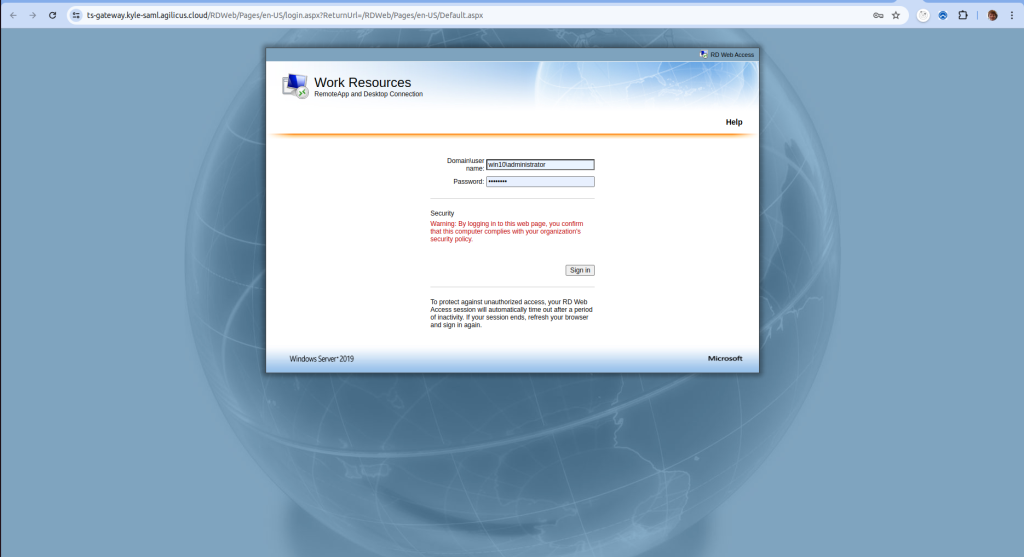
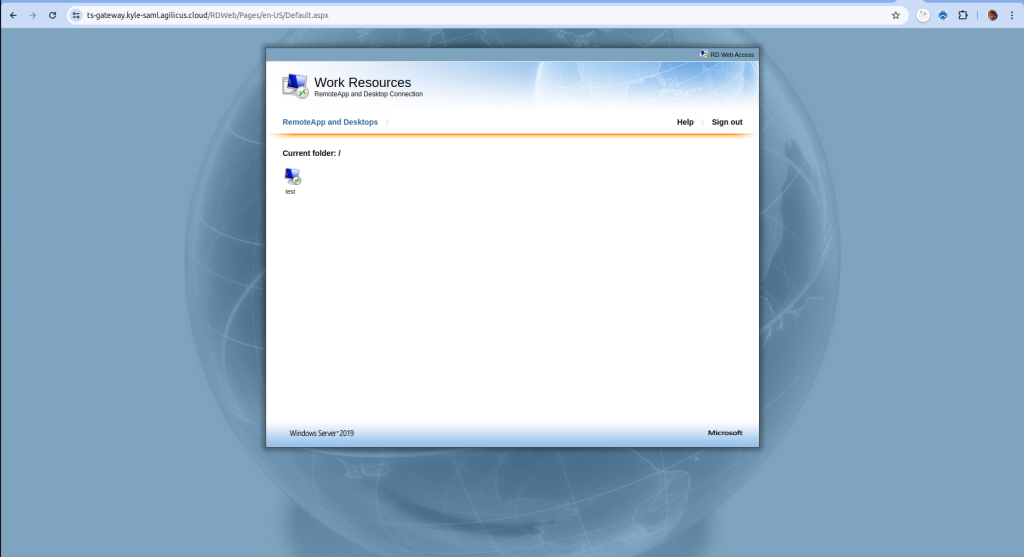
Prior to displaying the main page, you will be required to log in to Agilicus to gain access. Opening the downloaded RDP file will cause it to launch the Launcher you previously configured, which will then allow the user to access the otherwise inaccessible gateway.