Overview
There are 3-phases in the life cycle of usage: Authentication, Authorisation, Access. People commonly refer to ‘multi-factor authentication’, which enriches the information a user must know/have/be in order to properly authenticate themselves.
However, some security policies cannot be modelled simple as “do I know who this person is” in the authentication phase. These must be evaluated continually, rather than once when the user provides credentials. Below are a few example security policies that cannot be modelled solely with authentication.
Multi-Factor Required on Time-Interval or Based on Location
Imagine a user signs in on a device, and gets an ID Token, an Access Token, and, a Refresh Token. They can now present the access token until it expires, and, refresh it with the refresh token. This could be good for 1 week as an example, and be appropriate for usage of the corporate wiki or email.
Now imagine there is an application of significant importance to the company. A breach of it would be have a larger downside than a breach of the wiki. The company has decided on a security policy such that the user must prove they are still in possession of the multi-factor device each 8-hour shift. This cannot be expressed with Authentication Rules.
GeoIP Restricted Access By Resource
Using Authentication Policies, we can control where a user is at sign-in time, but not where they are at time of use. Imagine a singular resource which requires a tighter knowledge of the user’s location proxied by IP. It might require allowing only from a specific IP range, or, only from certain countries, or, from everywhere except certain countries.
Configuration
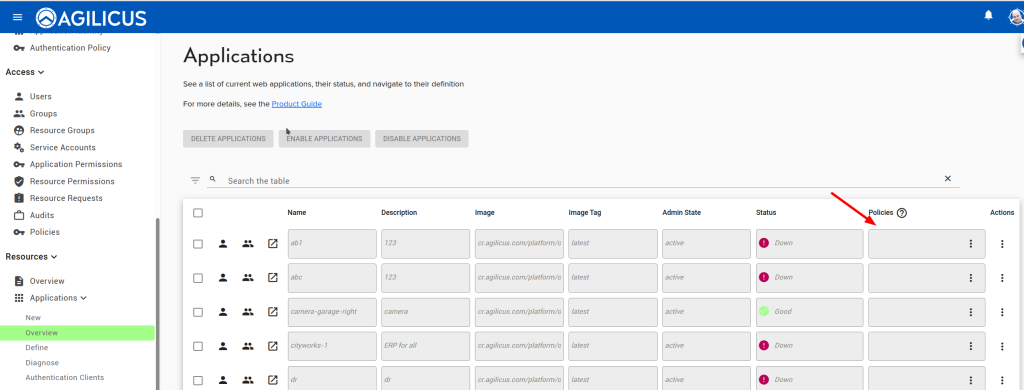
Policies are created in isolation, and then attached to resources via labels. A policy can apply to multiple resources.
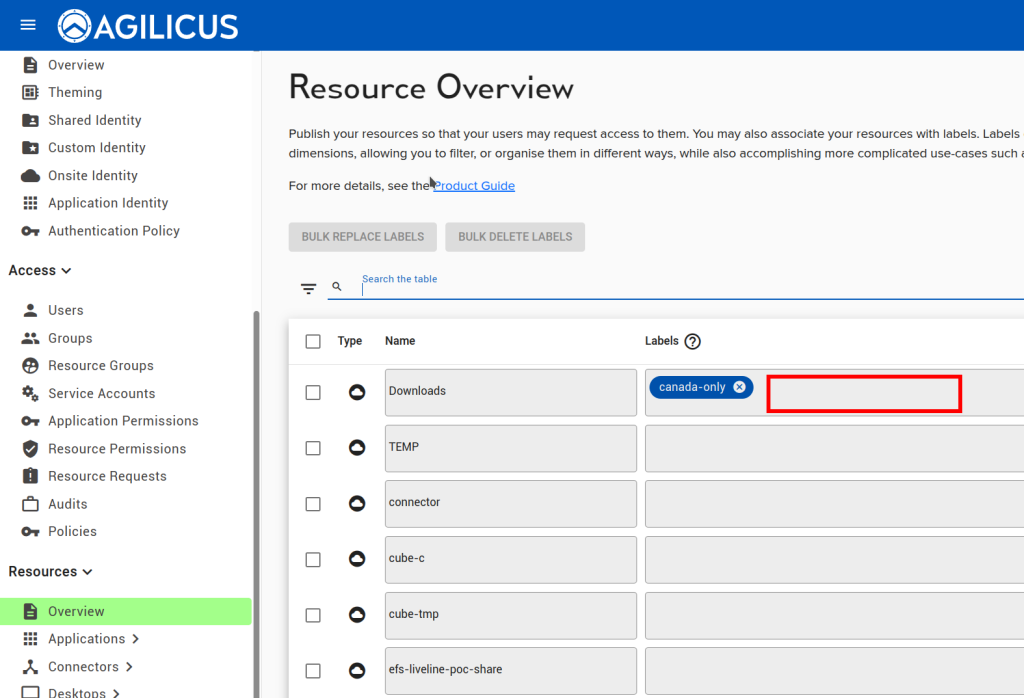
Step 1: Create Label To Attach Policy
Navigate to Resources/Overview. On the first resource you intend the policy to affect, type a name for it on the right (e.g. ‘canada-only’).
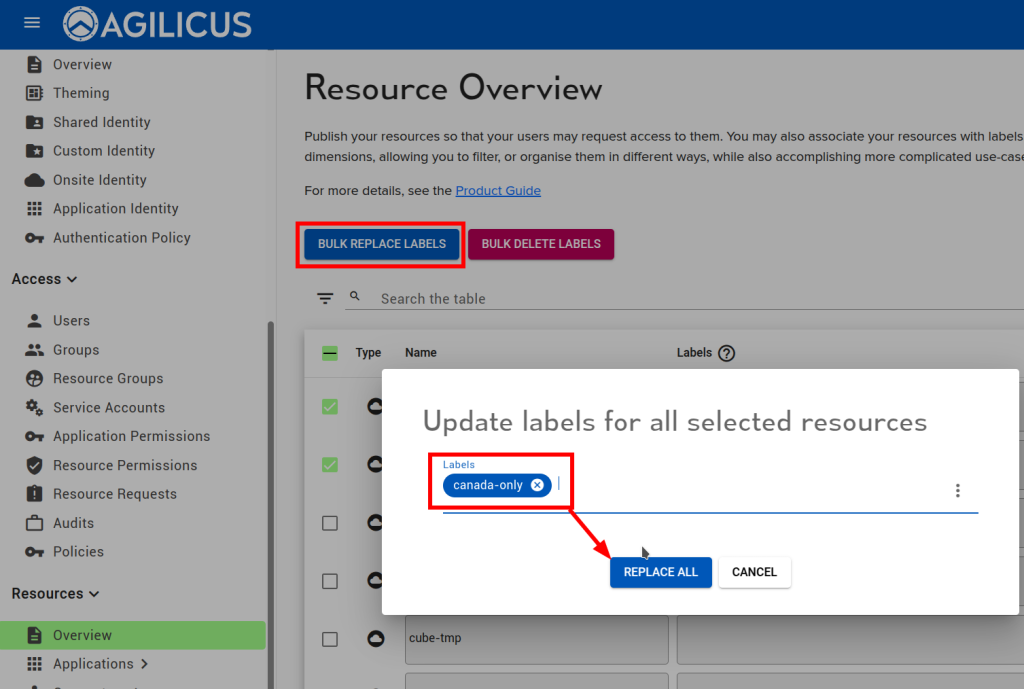
Now, select all resources to which it should apply, and then select ‘BULK REPLACE LABELS’, enter the name of your new label.
Step 2: Create Policy (Geo-IP / IP Restriction)
From Access/Policies, select NEW. Select ‘Device Information’, indicating that we will be using information relating to the user’s device for the policy.
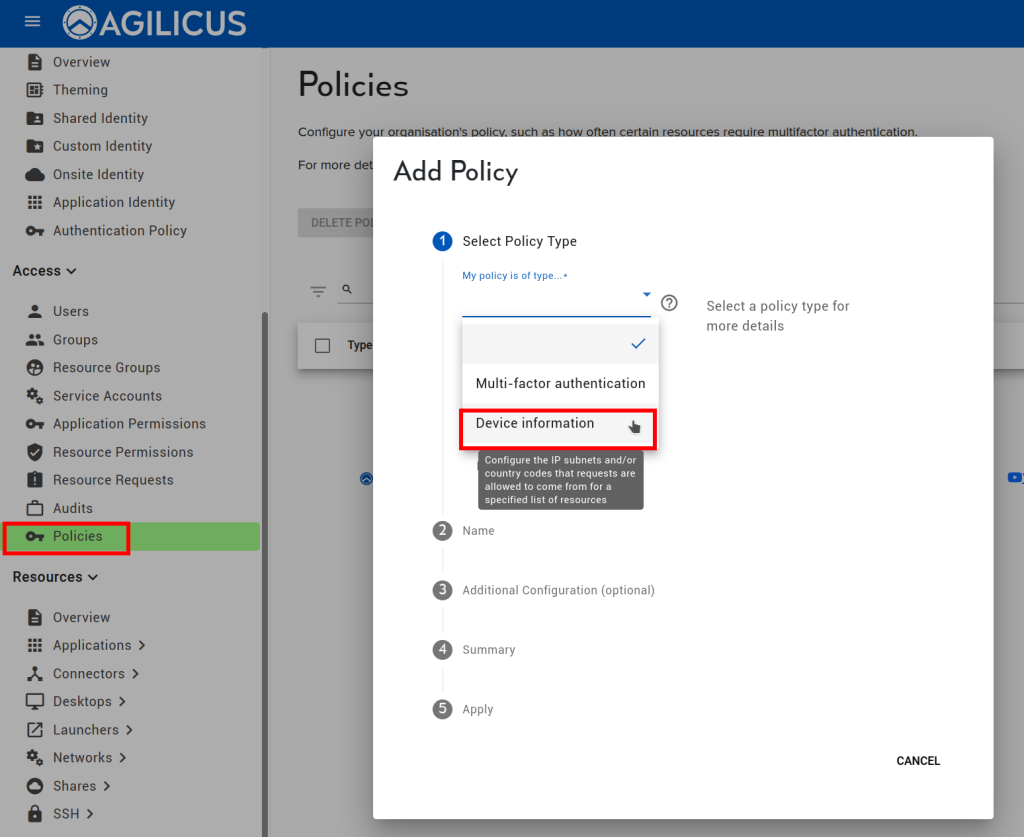
Give the policy a name. Here we have used the same name as the label, but you can use any.
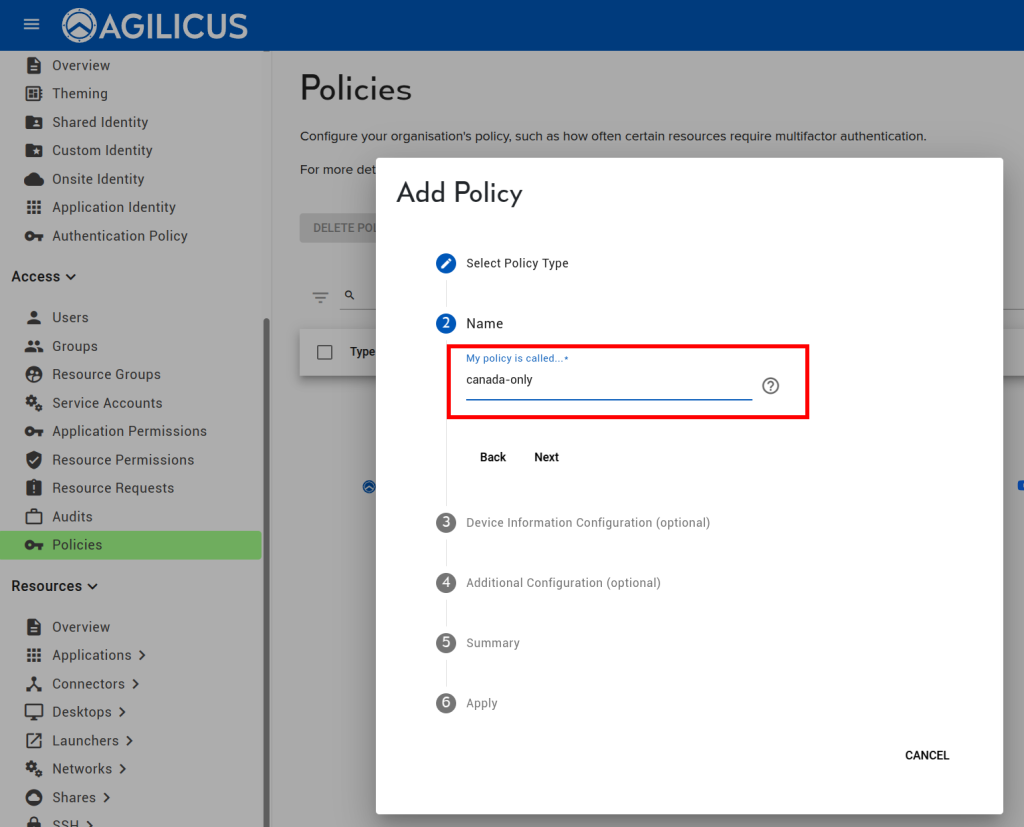
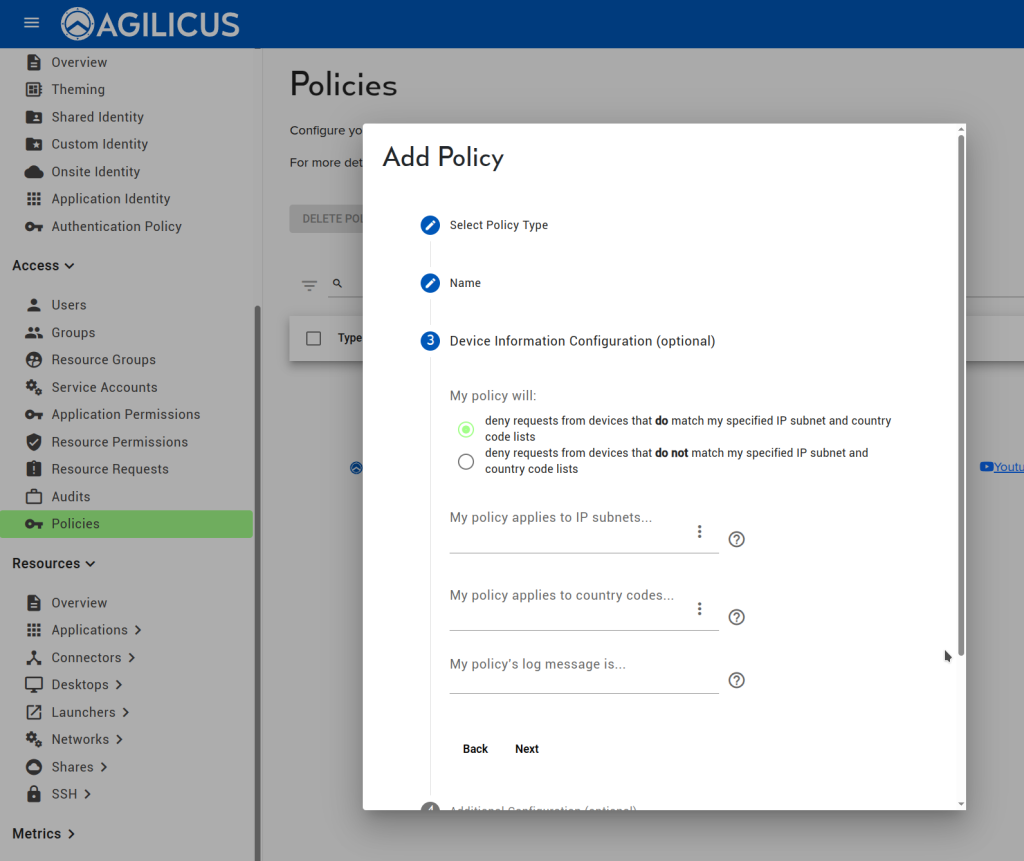
Configure the policy. Here as an example we will select the ‘country codes’, and, select CA for Canada.
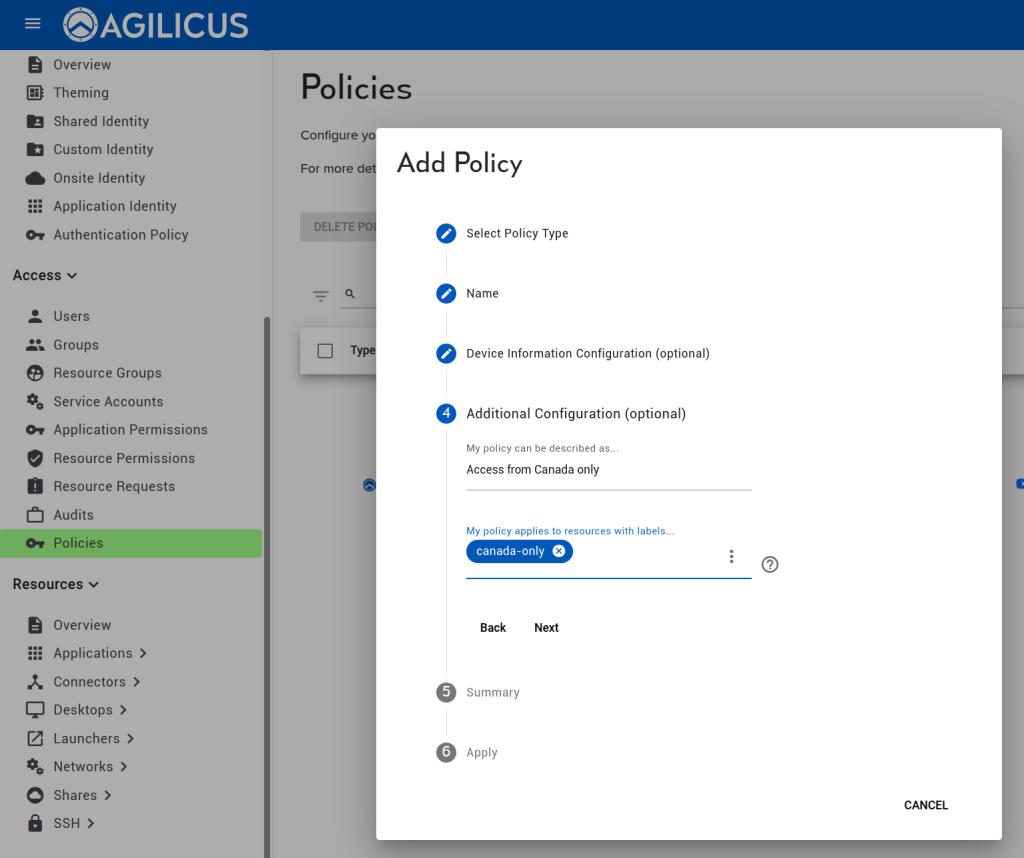
Enter some information describing this policy (e.g. why you created it), and, the label from above. This policy will now apply to all resources with that label (you can later navigate to Resources/Overview to apply it to more new resources).
We can now see the policy in the table, and it should be active within a few seconds.
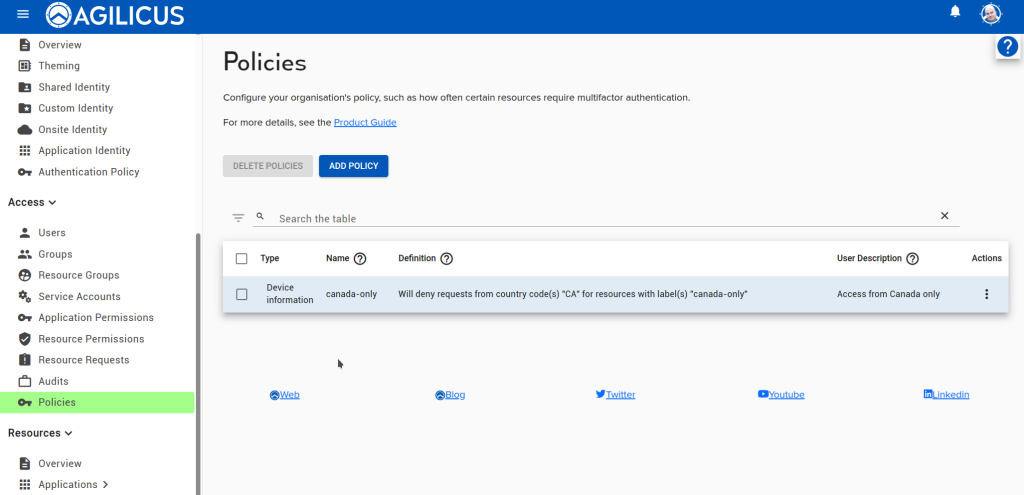
If you wish, you may manually apply policies