
VTScada Single-Sign-On
OpenID Connect Setup
Multi-Factor
Single-Sign-On
Agilicus AnyX – VTScada Single-Sign-On
Agilicus AnyX and VTScada are an ideal complementary match. Agilicus AnyX provides on-demand access, from anywhere, to any user, to the VTScada Anywhere client. This provides high-security and high simplicity usage for remote support and diagnostics.
A minor usability issue can arise, a ‘double login’ experience. The user signs in via Agilicus AnyX with their corporate single-sign-on credentials, but, then the VTScada system doesn’t trust them. This happens with external support and contractors as well as direct staff. Fortunately there is a simple solution: Configure VTScada to ‘participate’ in the sign-in and use Agilicus AnyX as the OpenID Connect Provider. Once this simple configuration is completed the user will sign-in once, using their native corporate account, without local configuration on VTScada.
First, we configure the Application in Agilicus AnyX. The only change from a typical application is to use the ‘My Application Participates in Authentication’. Otherwise configure as usual for VTScada.
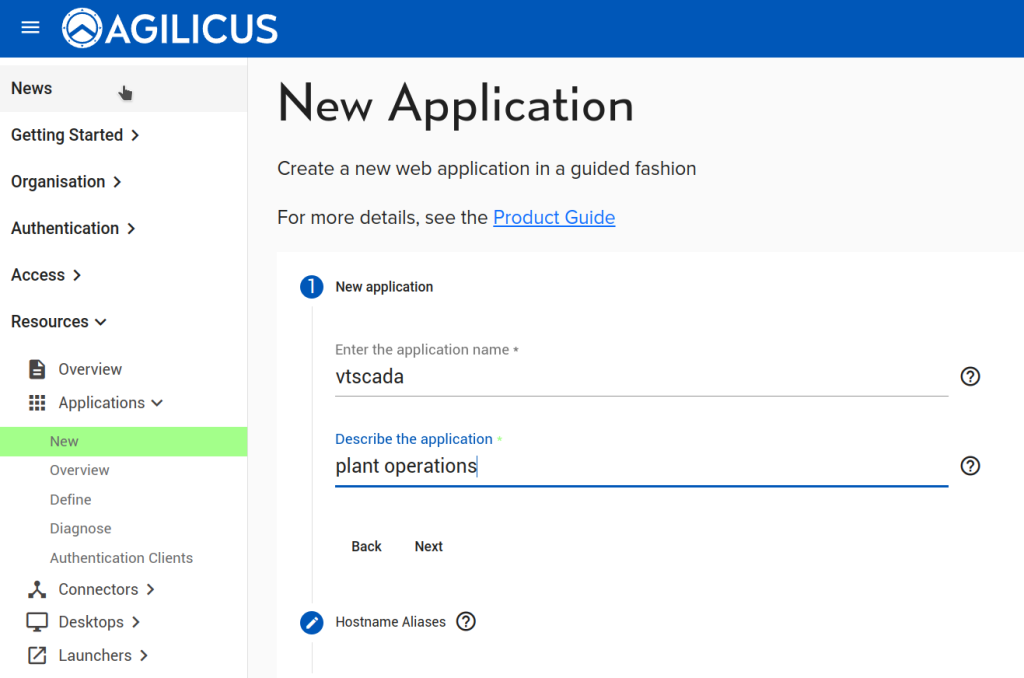
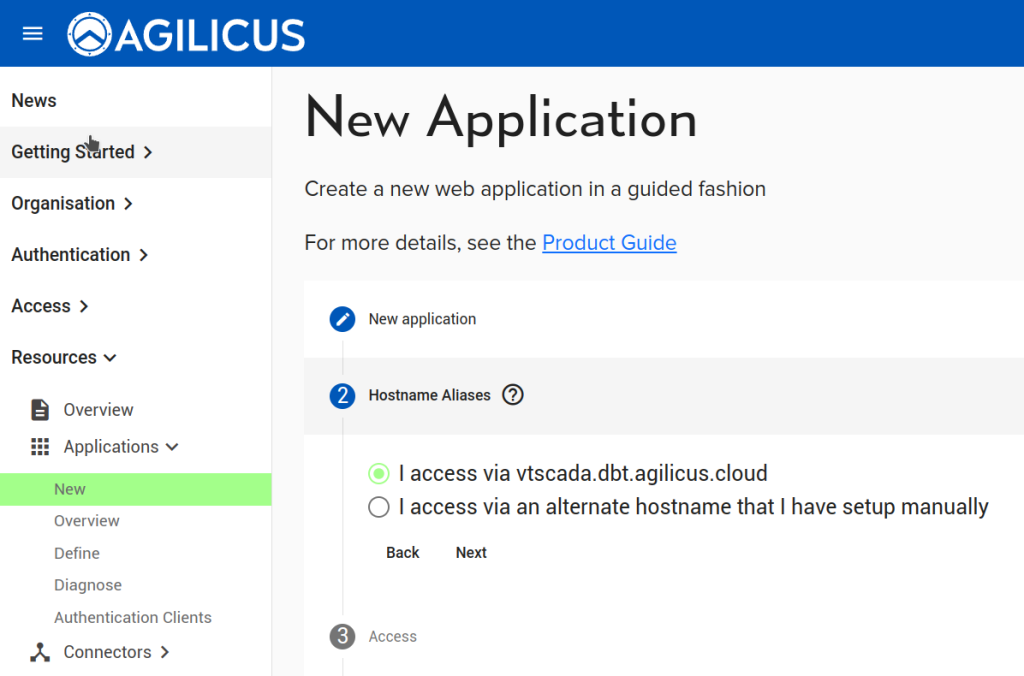
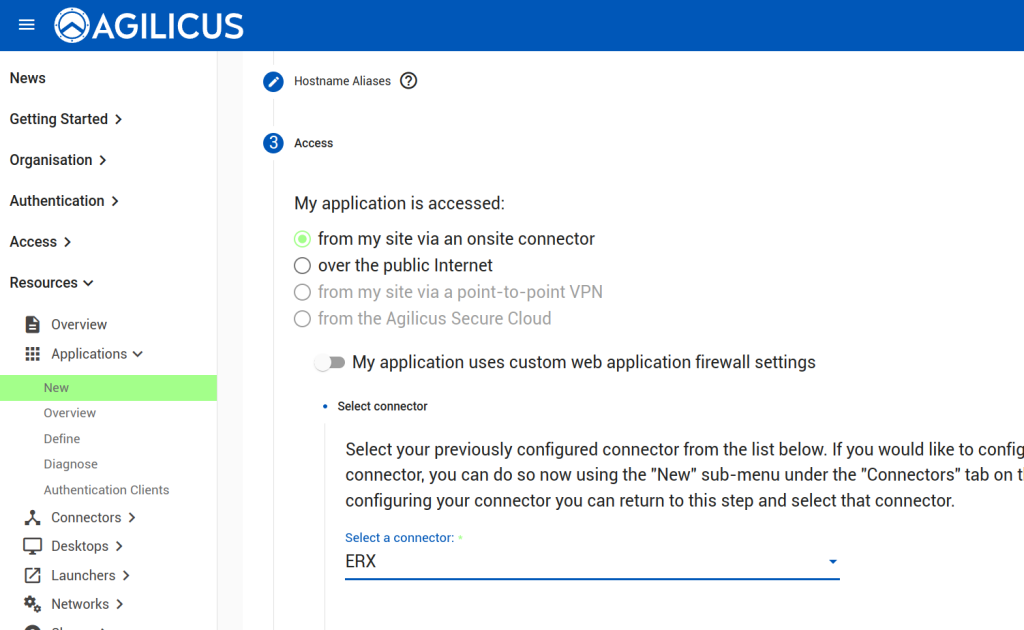
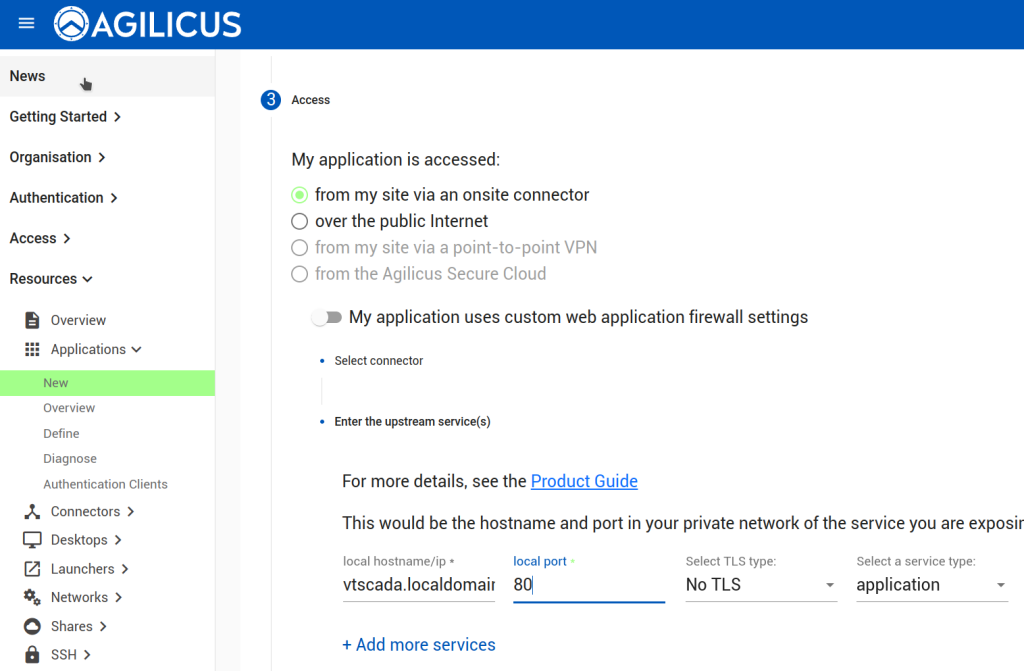
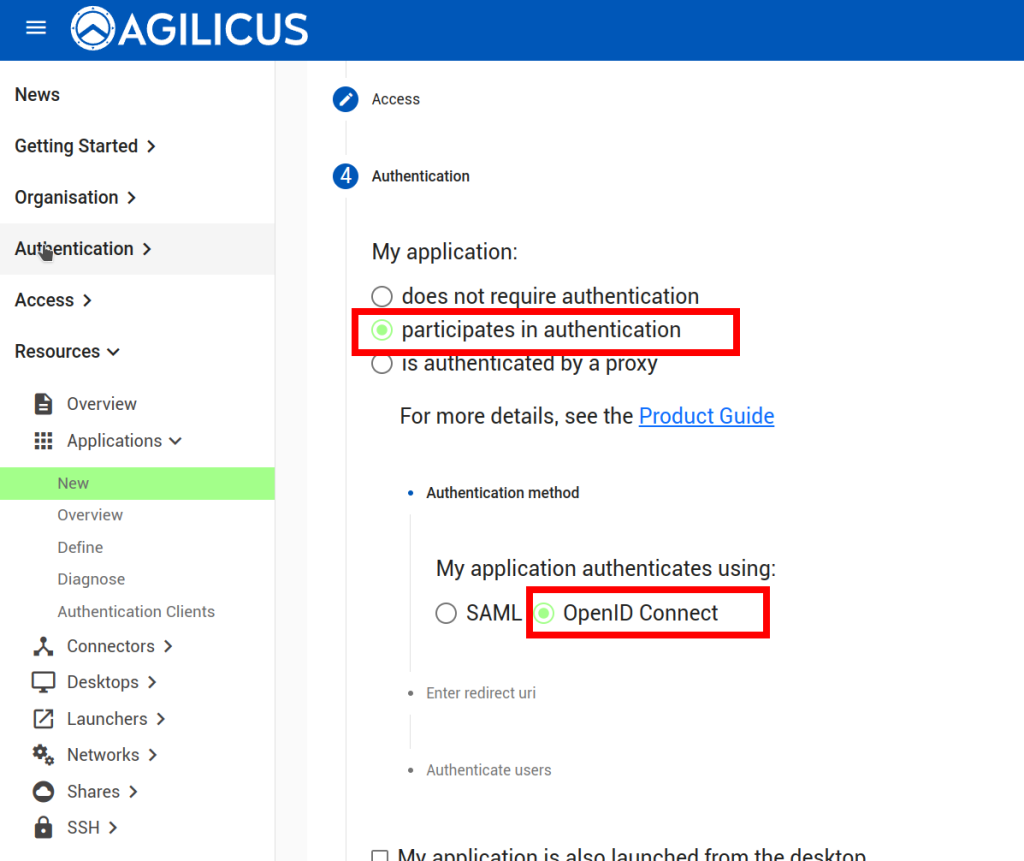
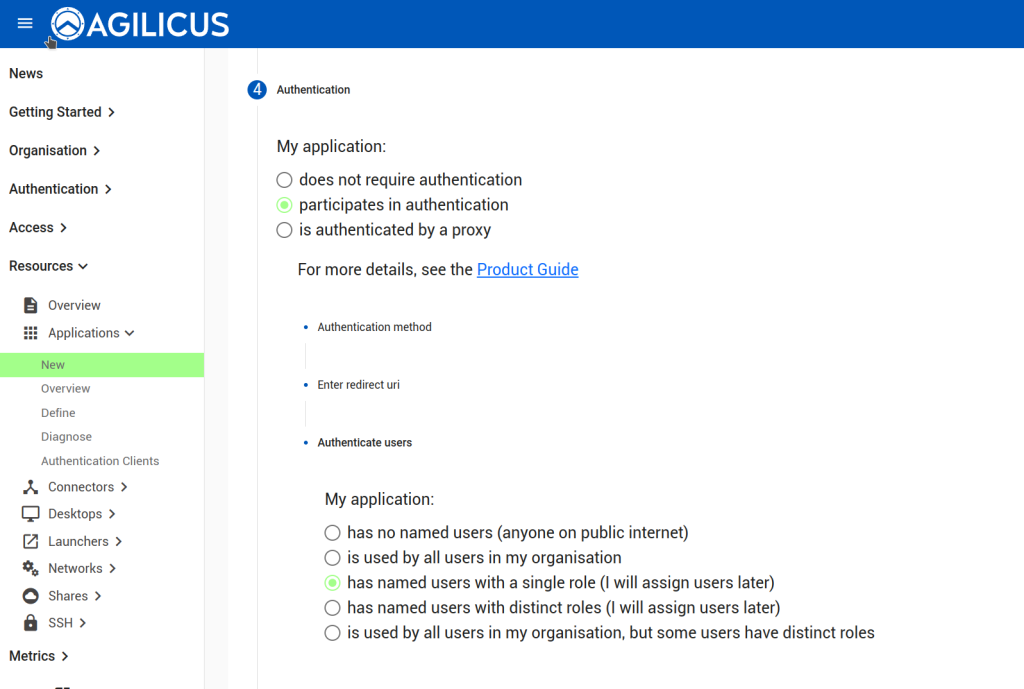
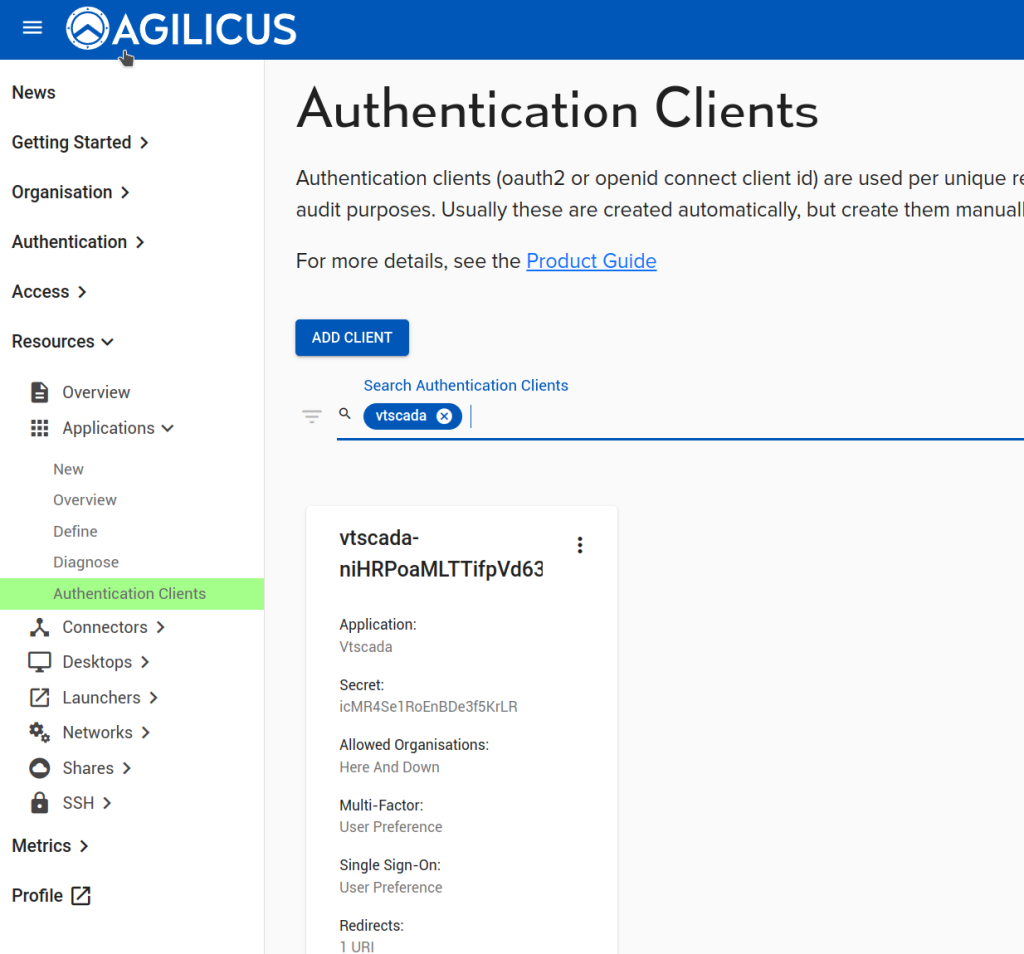
Now that we have configured the Application, we can observe that a OpenID Connect ‘Client’ has been created (Resources/Applications/Authentication Clients). The name of it we will use in the VTScada configuration below. We will also configure a ‘remapping’ to cause the Agilicus User ‘External ID’ field to become available (see “VTScada – OpenID Connect Authentication“) for mapping to a different username if desired.
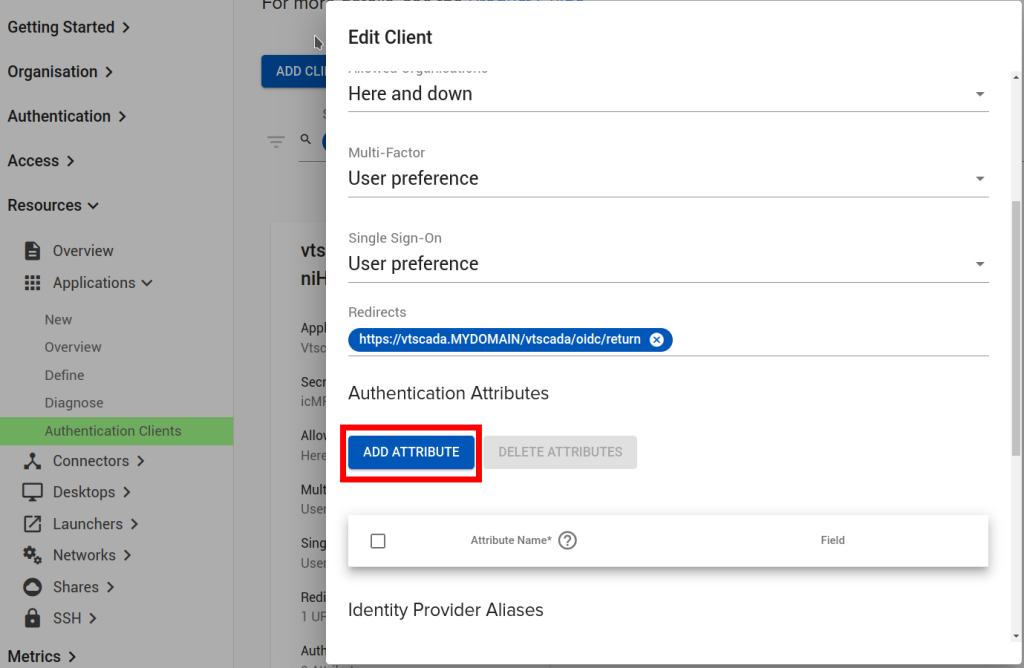
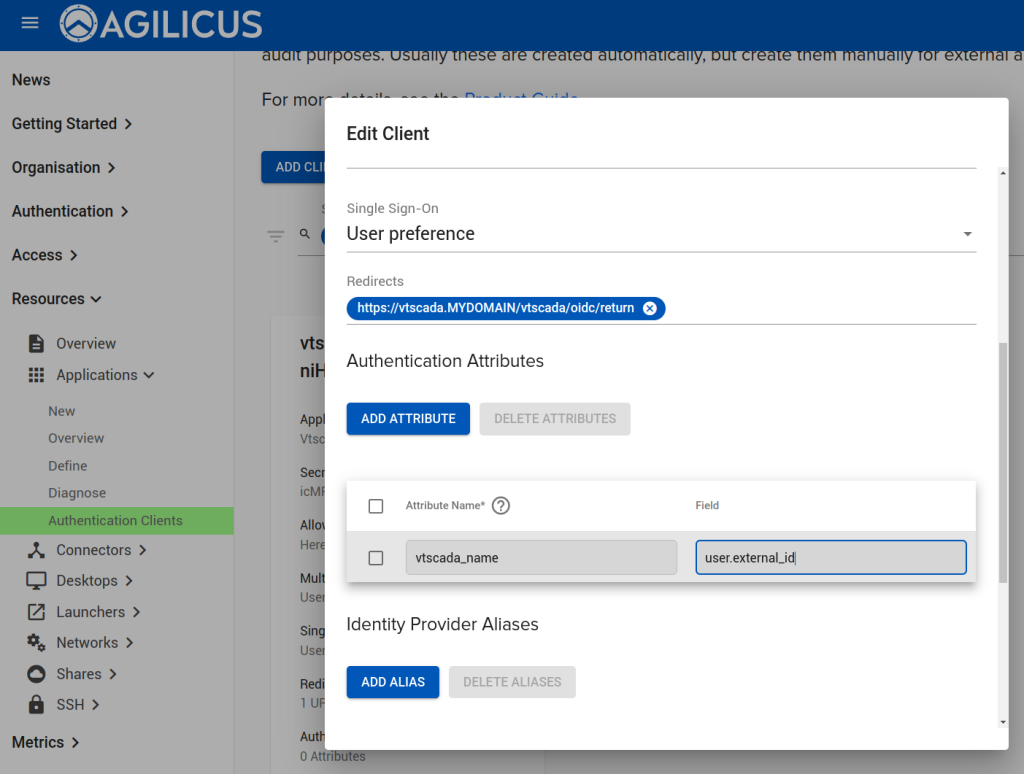
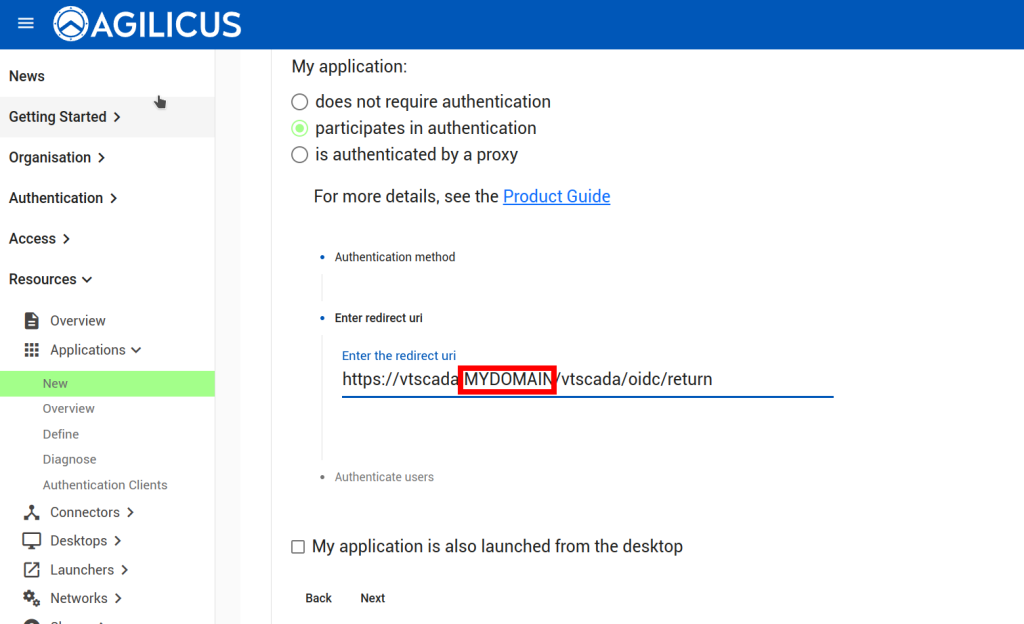
Add the ‘redirect uri’. The format will be “https://<vtscada-name.__MYDOMAIN__/vtscada/oidc/return”, matching vtscada-name and __MYDOMAIN__ to your environment.
At this stage we are complete in the Agilicus Admin and will switch to the VTScada configuration.
In the “OpenID Connect Provider” box, we will use the ‘discovery’ feature. The URL will be https://auth.__MYDOMAIN__/.well-known/openid-configuration. If you chose to use the remap feature above, enter that in the Account Name Field.
Enter the Client ID from above in the Client ID field of VTScada, as well as the Secret.
At this stage, test the login, it should function.
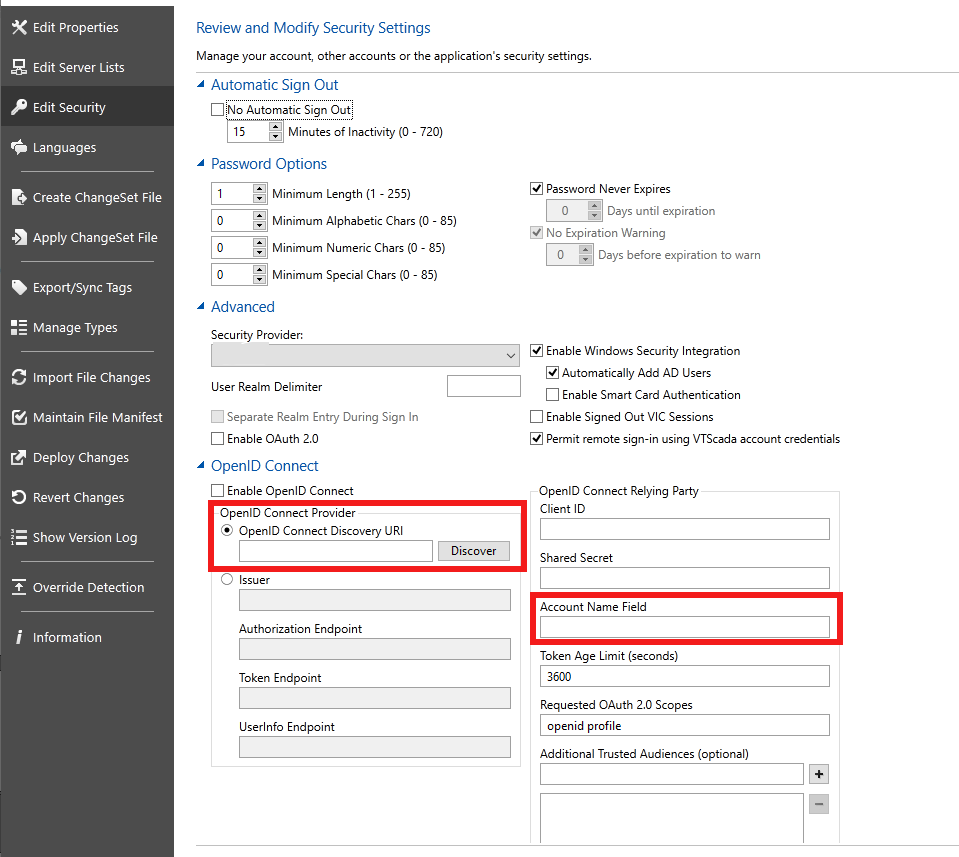
The key fields to use:
- Enable OpenID Connect
- OpenID Connect Discovery URL (https://auth.__MYDOMAIN__/.well-known/openid-configuration). Press the ‘Discover’ button, it will fill in the fields below
- Permit remote sign-in using VTScada account credentials
- Client ID (match to the field from Agilicus Authentication Client)
- Shared Secret (match to the field from the Agilicus Authentication Client)
- Account Name Field (match to the remapping above)
- scopes (openid email groups profile offline_access)
https://www.vtscada.com/help/Content/D_Customize/Dev_OpenIDConfig.htm
NOTE: VTScada will require an outbound firewall connection to auth.__MYDOMAIN__. The user authenticates in their browser and passes a token to VTScada, which will in turn use that to lookup the user information remotely.
Mapping Multiple External Users To A Single VTScada User, With Multi-Factor
In some environments its desirable to have a single VTScada user (e.g. Operator) shared by multiple external users (e.g. joe@mycompany, jane@mycompany). Normally this would not be safe, but, with Agilicus AnyX the authentication is not shared and can include individual user multi-factor authentication.
Using the remapping above, use the ‘external-id’ field on a per-user in the Agilicus web admin, assign the VTScada user name per person.
For example, if you use these settings in the Agilicus admin users:
| Agilicus (External) Username | External-ID |
|---|---|
| jane@mycompany | operator |
| joe@mycompany | operator |
| jerry@mypartner | admin |
And remap the External-ID as:
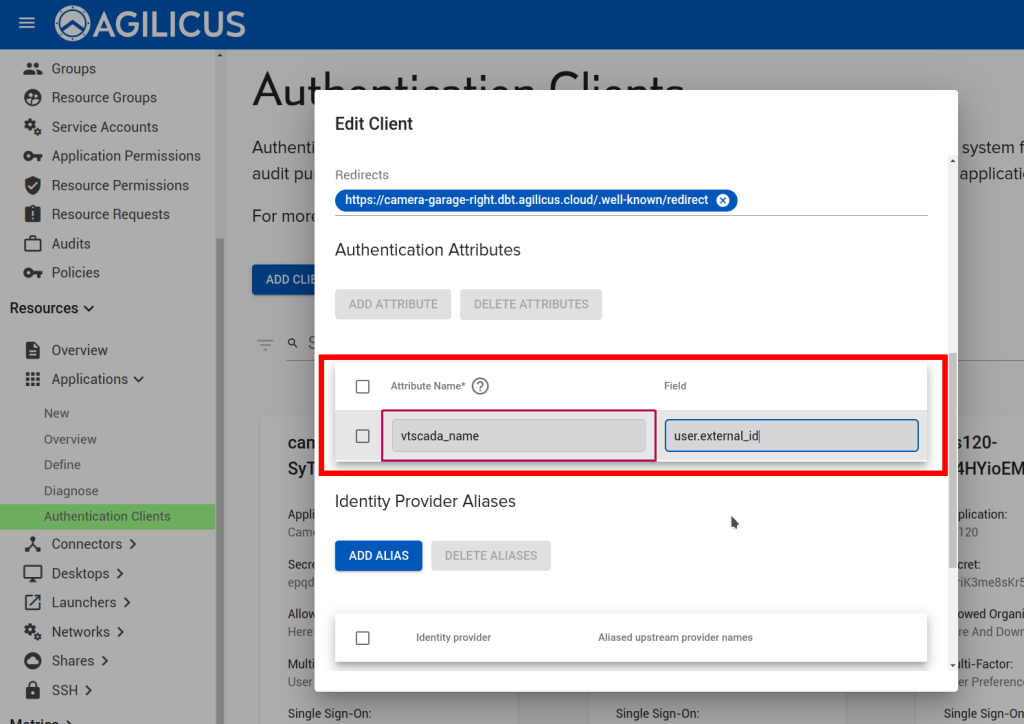
Then Jane and Joe can sign in using their @mycompany single-sign-on (e.g. via O365, Google Workplace), be challenged for a second factor, but then end up signed into VTScada as ‘operator’.