Recently some Human Machine Interface (HMI) used in Public Water systems, specifically wastewater treatment plants, have come under attack. The first I read of it was in “Iranian hacker group CyberAv3ngers allegedly breach Municipal Water Authority of Aliquippa“, which was immediately followed by me heading to Google Maps and typing in “Aliquippa“. Reading through the various articles, I was able to piece it together, how this Exploitation of Unitronics PLCs used in Public Water Systems was happening:

- For political reasons, someone has chosen Unitronics PLC and HMI as a target
- These are commonly used in public water systems
- Simple weakness like default password were used
- Simple holes through firewalls, missing Zero Trust, were used
- Most people focused on the specific grafitti/damage, rather than on the lateral traversal (the onwards damage) that might have come
CISA advisory on Exploitation of Unitronics PLCs used in Public Water Systems
CISA issued an advisory on this Exploitation of Unitronics PLCs used in Public Water Systems with some good information and recommendations, specifically:
- Change the Unitronics PLC default password—validate that the default password “1111” is not in use.
- Require multifactor authentication for all remote access to the operational technology network, including from the corporate/IT network and external networks.
- Disconnect the PLC from the open internet. If remote access is necessary, implement a Firewall/VPN in front of the PLC to control network access to the remote PLC. A VPN or gateway device can enable multifactor authentication for remote access even if the PLC does not support multifactor authentication. Unitronics also has a secure cellular based longhaul transport device that is secure to their cloud services.
- Back up the logic and configurations on any Unitronics PLCs to enable fast recovery. Become familiar with the process for factory resetting and deploying configurations to a device in the event of being hit by ransomware.
- If possible, utilize a TCP port that is different than the default port TCP 20256. Cyber actors are actively targeting TCP 20256 after identifying it through network probing as a port associated to Unitronics PLC. Once identified, they leverage scripts specific to PCOM/TCP to query and validate the system, allowing for further probing and connection. If available, use PCOM/TCP filters to parse out the packets.
- Update PLC/HMI to the latest version provided by Unitronics. to avoid Exploitation of Unitronics PLCs used in Public Water Systems
The only think i really quibble with here is the Firewall/VPN. I strongly recommend a per-resource authentication + authorisation, as provided by a Zero Trust product, shamelessly plugging Agilicus AnyX here. You really need the comfort of strong authentication, single-sign-on, multi-factor, and, fine-grained audit. A VPN is just an Ethernet cable with more length, no specific controls on the lateral traversal.
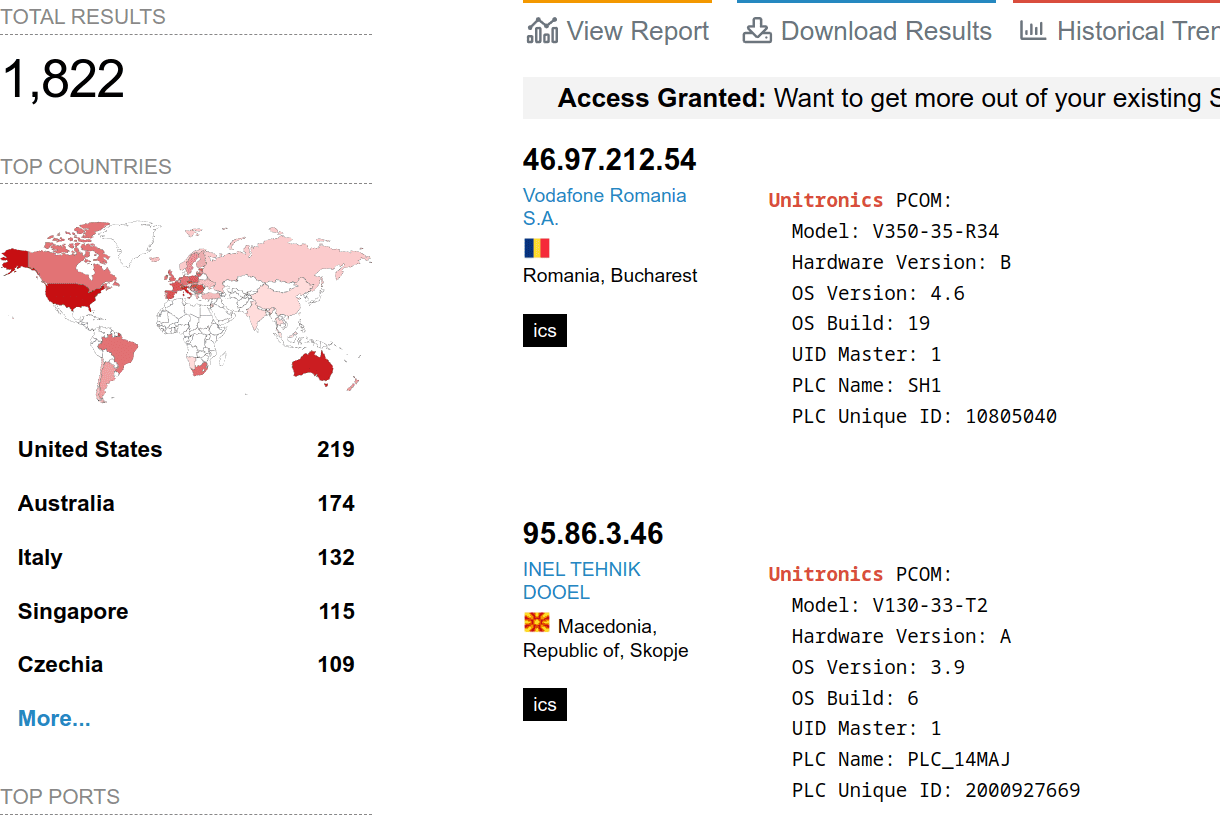
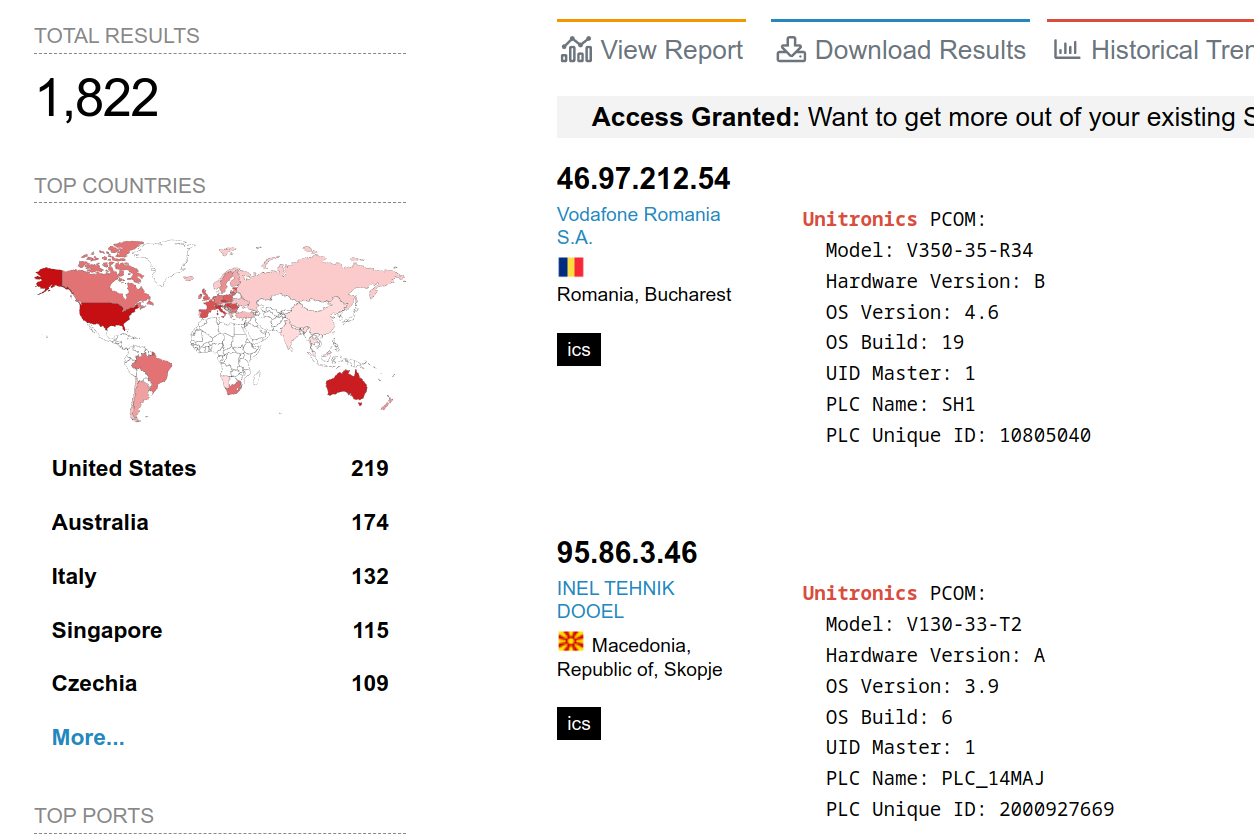
Using everyone’s favourite tool, shodan.io. we can see there are at least a few Unitronics HMI devices hanging out there for ease of access. And, all have the default ports open, leading me to suspect, maybe more.
So, if you are using these (or similar devices), and worried about the balance of removing team efficiency by removing access versus having some hacker waltz in, have I got a solution for you.
And, I would love to talk with you about it, using either the Chat icon on this page, email info @ agilicus,com, or Contact. If you would like to pick a specific time, Book a meeting.