Protect The Page
Web Application Security
Web Application Security
Articles
-
GoDaddy Got Got: Multi-Year Breach
A multi-year attack involving 1.2M customers, hosting, DNS. What could the miscreants have achieved? DKIM? SSL? Domain verification?
-

Protecting Against the OWASP Top 10 Web Application Vulnerabilities
The OWASP Top 10 is a standard awareness document that outlines the most critical web application security risks and vulnerabilities. Learn how Agilicus AnyX is designed to eliminate an attacker’s visibility into the potential OWASP Top 10 web application vulnerabilities.
-

Industrial Air Gap – A Tale Of 2 Users
Industrial devices are hard to secure. Commonly done only via direct local access. Teams, however, wish remote access to improve efficiency. A solution to this battle is Zero Trust.
-

Multi-Factor Authentication And The Supply Chain
A high(ish) profile nodejs library is compromised. No multi-factor authentication used by developer. The ripples are far and wide. Including you!
-
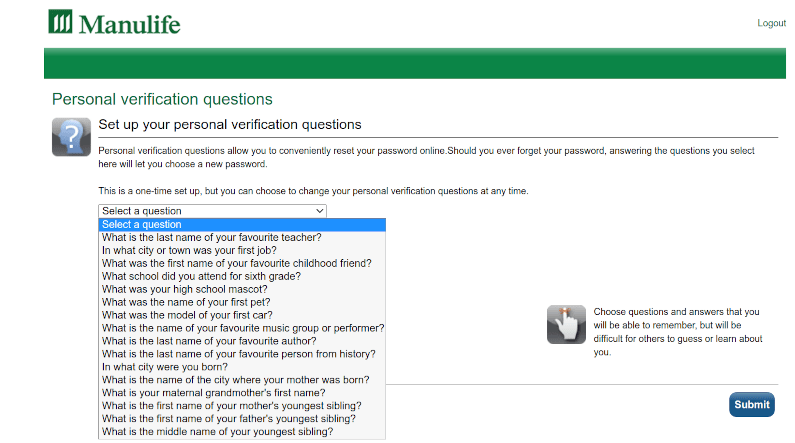
The Personal Verification Question: Password’s Dumb Cousin
The personal verification question. The dumb, slow cousin of the password. Stored in plaintext, findable in social media. Not multi-factor auth
-
Add multi-factor authentication to old applications
Your cyber insurance is up for review. IGet all applications authenticated with multi-factor, simply, quickly, compliantly.
-
Re-Using your Multi-Factor Authentication To Prove Humanity
Spam. The cat and mouse game of advertisers seeking to reach more people for less cost, and, people seeking to spend more to not be reached. The current state of the art in proving “I am not a spam-sending robot” is the captcha. Do you love the captcha? Me neither. Do you sometimes fail it? Me too!
-
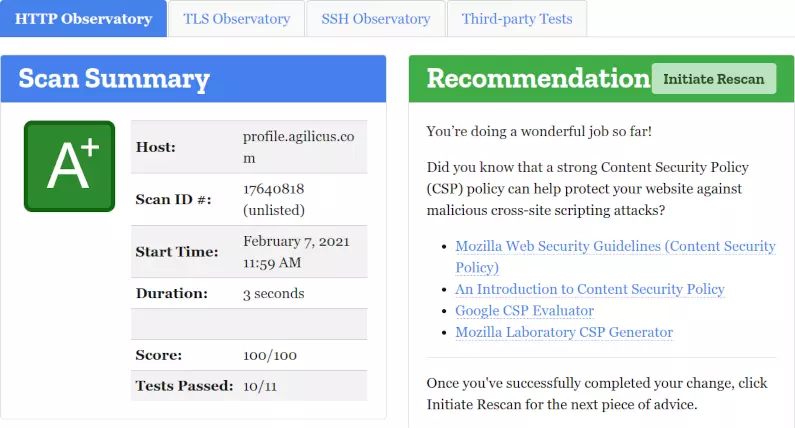
Angular Content-Security-Policy Complex Nonce: Google Tag Manager
Content-Security-Policy protects our application, but challenging with external scripts like Google Tag Manager. We show in Angular Single Page Application.
-
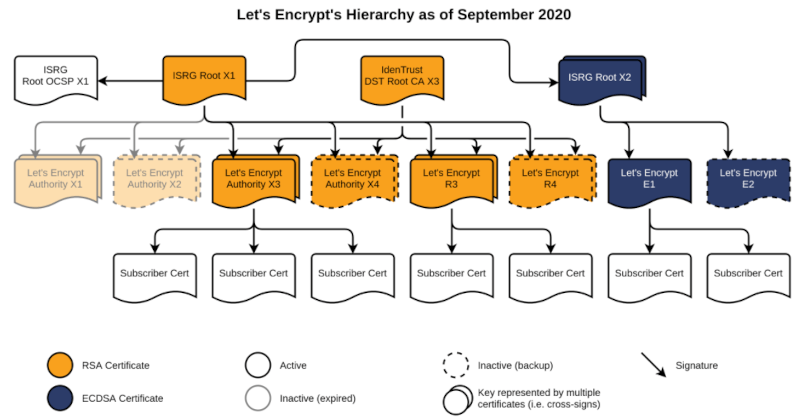
Let’s Encrypt X3 to R3 and Certificate Transparency Logs
Certificate Transparency Logs in SSL can be a useful diagnostic tool as well as a security forensic.
-

OAuth 2.0 Protected Resource Threats
The OAuth 2.0 protected resource. It takes the access token and uses it to grant access. Watch out for it becoming compromised.
-

OAuth 2.0 Refresh Token Threats
OAuth 2.0 refresh tokens are used to obtain new access tokens on the user’s behalf. If lost, they can allow an attacker to masquerade.
-

OAuth 2.0 Token Endpoint Threats
The OAuth 2.0 Token Endpoint. Its were authorisation becomes real. Secure it to prevent guessing
-

OAuth 2.0 Authorisation Endpoint Threats
OAuth 2.0 Authorisation Endpoints are the front-door skeleton-key creator of all your front-doors. So protect them carefully.
-

OAuth 2.0 Client Threats
OAuth 2.0 and the client. Use Defense In Depth. Secure the client, and then assume it can still be compromised. Zero Trust.
-

OAuth 2.0 Threat Model and Security Considerations
OAuth 2.0 has simplified authentication and authorisation for many applications, shifting from custom code to simple library import. However, as more applications come to rely on it, this makes its weaknesses more interesting. An attacker can gain access to a broader set of data via a smaller set of tactics and techniques. First lets understand the threat areas, and then, the best current practices for addressing them.
-

OAuth 2.0 Proof of Possession
OAuth 2.0 replaced Proof of Possession with Bearer Tokens for simplicity, a controlversial decision. A new draft brings them back.
-

OAuth 2.0 Access Token Demonstrate Proof of Possession
Theft of an Access Token need not be a complete loss. Learn how Demonstration of Proof Of Possession can reduce this risk.
-

Blurring the web and the app: web push
Web push. An important part of making web applications peer to native, and more secure, more accessible.
-
My team works outside, why can’t their Kronos Timesheet?
Access your on-premise Kronos from any user, from any device, from any network. Increased security, increased simplicity. Zero Trust Networking.
-

The JWT Bearer Token: You On The Wire
A bearer token is a cryptographic representation of who (you) and what (authorisation) that is used on a per-transaction basis. Learn and Use!
-

Take time to stop and sniff the mime type
Happy Eyeballs? Mime-Type-Sniffing? Security wins, don’t infer content type from file name.
-

WEB SECURITY 101
January 2020 Waterloo Technology Chautauqua, Web Security 101
-

USE OF POSTMAN WITH OPENID CONNECT PKCE AND API
Many API’s, Agilicus’ included, use OpenAPI to specify how they function. Authentication of these is usually left out of scope, but, provided as a bearer token. This means that if you write a web application, you want to directly use the RESTful API’s, and you do so by first authenticating via OpenID Connect PKCE flow and remembering the access token.
-
Zero Trust: Connecting The Digitally Disconnected
Digitally Disconnected. The 2nd class citizens of the 21st Century. Unable to access data due to identity or VPN. NO MORE! Zero Trust.
-

Static Application Scanning Angular: Resolving lodash npm audit
Static Application Scanning with Angular can sometimes block release with no solution. Learn about better-npm-audit.
-

Secure the Cookie!
The humble cookie. So controversial. So complex to secure. If your web app must have them, you must secure them.
-

Fixing the case of the Implicit Flow modification
Meet Hank. Hank is a web application with a dark secret. It trusts you the user to not change things in the browser. Bad Hank. Learn how to fix it!
-

Why should I use Content-Security-Policy?
The Content-Security-Policy headers exists to protect the users of your web site from the content they themselves might create.
-

The Web Application Firewall and You: Who Should Use, and When.
Should I use a Web Application Firewall? What is it ? What benefit will it give me? When would I use it? Read on to learn!
-

Fixing the case of the un-sanitised input web app
Web applications may not be inherently secure. But we want them Internet available anyway. How can we reconcile these two? Let’s see!.