CityWorks by Trimble is a commonly used GIS system. And, it is commonly either self-hosted, or, hosted by a set of individual partners, running as a virtual host within Microsoft IIS. A newly issued alert from CISA, and a note from Trimble, indicate that CVE-2025-0994 is being actively exploited (a Known Exploited Vulnerability) as an 8.6. How do you read an 8.6? Well, roughly the same way you would read an earthquake. Versions prior to January 29th, 2025 are vulnerable.
Trimble has released some preliminary “how can I tell if I’ve been breached”, notable in here is the Rust loader.
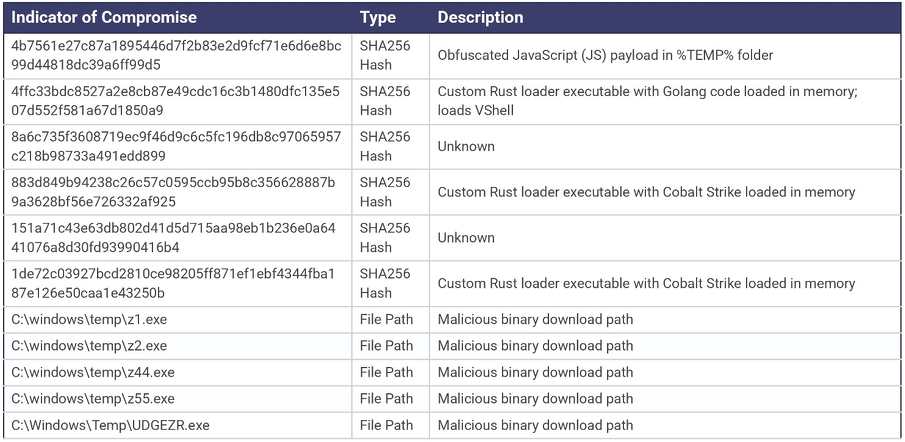
The vulnerability is up-levelled if you either a) run CityWorks or IIS with elevated privileges, or b) run other web applications on the same host (in other vhosts), or c) run other applications on the same host, or d), the web host is on the same network as other servers.
How can you protect? The simplest is to put an identity-aware-proxy in front like Agilicus AnyX. This maintains a seamless experience to the end-user, but prevents any connectivity except for users with valid accounts via single-sign-on and multi-factor authentication.
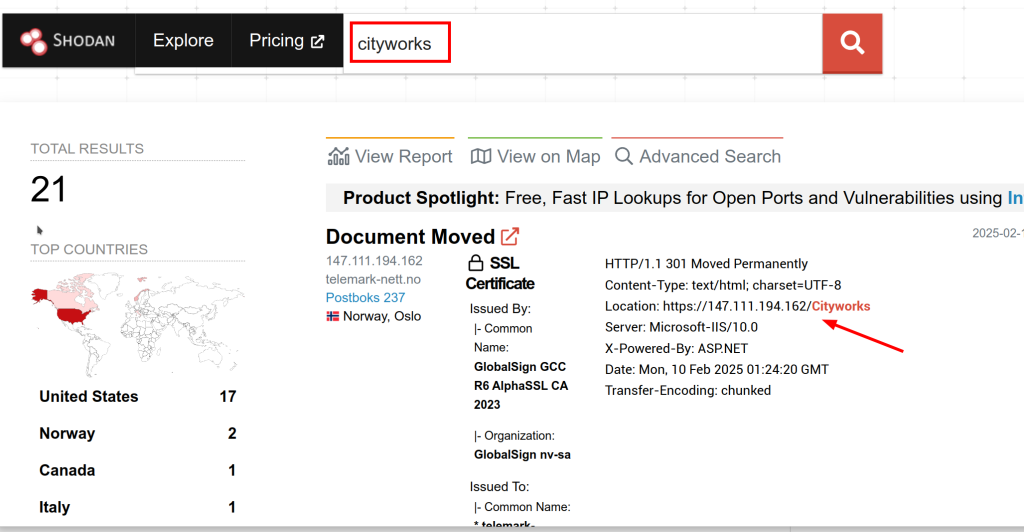
A quick search with everyone’s favourite search engine, shodan.io, shows no shortage of CityWorks sites without protection.
The good news? If you are not yet exploited, Agilicus can help while you work on the upgrade, with a simple deployment in minutes without disrupting anything. Contact us and learn how Agilicus AnyX can provide a Zero-Trust Identity-Aware Proxy for CityWorks and other web applications today.