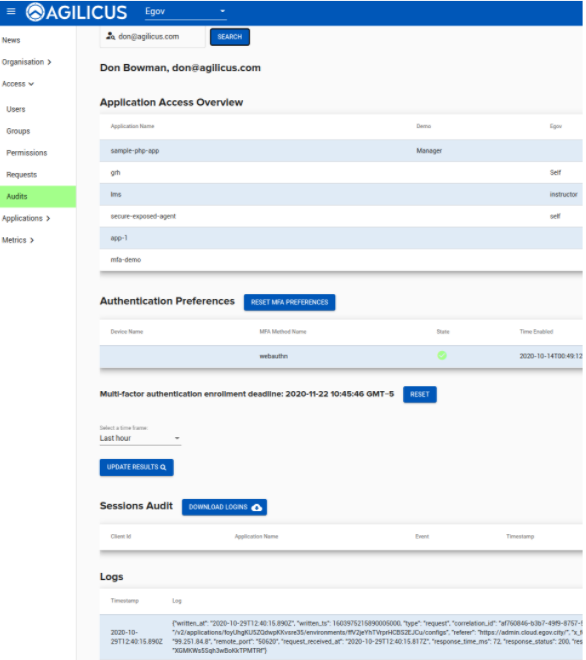
Many systems generate logs. These are often done with layer-3 coordinates (IP). But, when auditing, one finds the IP is not useful. Its dynamic. Its overlapping. Its private. Its shared. Coordination and correlation of logs becomes very complex and fuzy.
The Agilicus Secure Cloud provides audit
- of Each session (login) create, refresh, destroy, revoke
- of Each HTTP flow, per user, per application
This per flow, per user, per application audit is done using the same cryptographic identifiers that we use to identify the user. The Zero Trust assertions placed on each flow are used. This means, no correlation. No fuzziness. Perfect accuracy. Infinite audit.