Rockwell Automation has issued an urgent directive “IMPORTANT NOTICE: Rockwell Automation Reiterates Customer Guidance to Disconnect Devices from the Internet to Protect from Cyber Threats”.
Amongst the reasons given (other than the obvious, these devices have negligible security, control things which might be dangerous) are these CVE. But really, this is just a starting point, you need a firewall that confirms identity between the PLC and the net, in both directions.
| CVE ID | Advisory |
| CVE-2021-22681 | CISA | Rockwell Automation Logix Controllers (Update A) |
| CVE-2022-1159 | CISA | Rockwell Automation Studio 5000 Logix Designer |
| CVE-2023-3595 | CISA | Rockwell Automation Select Communication Modules |
| CVE-2023-46290 | CISA | Rockwell Automation FactoryTalk Services Platform |
| CVE-2024-21914 | CISA | Rockwell Automation FactoryTalk View ME |
| CVE-2024-21915 | CISA | Rockwell Automation FactoryTalk Service Platform |
| CVE-2024-21917 | CISA | Rockwell Automation FactoryTalk Service Platform |
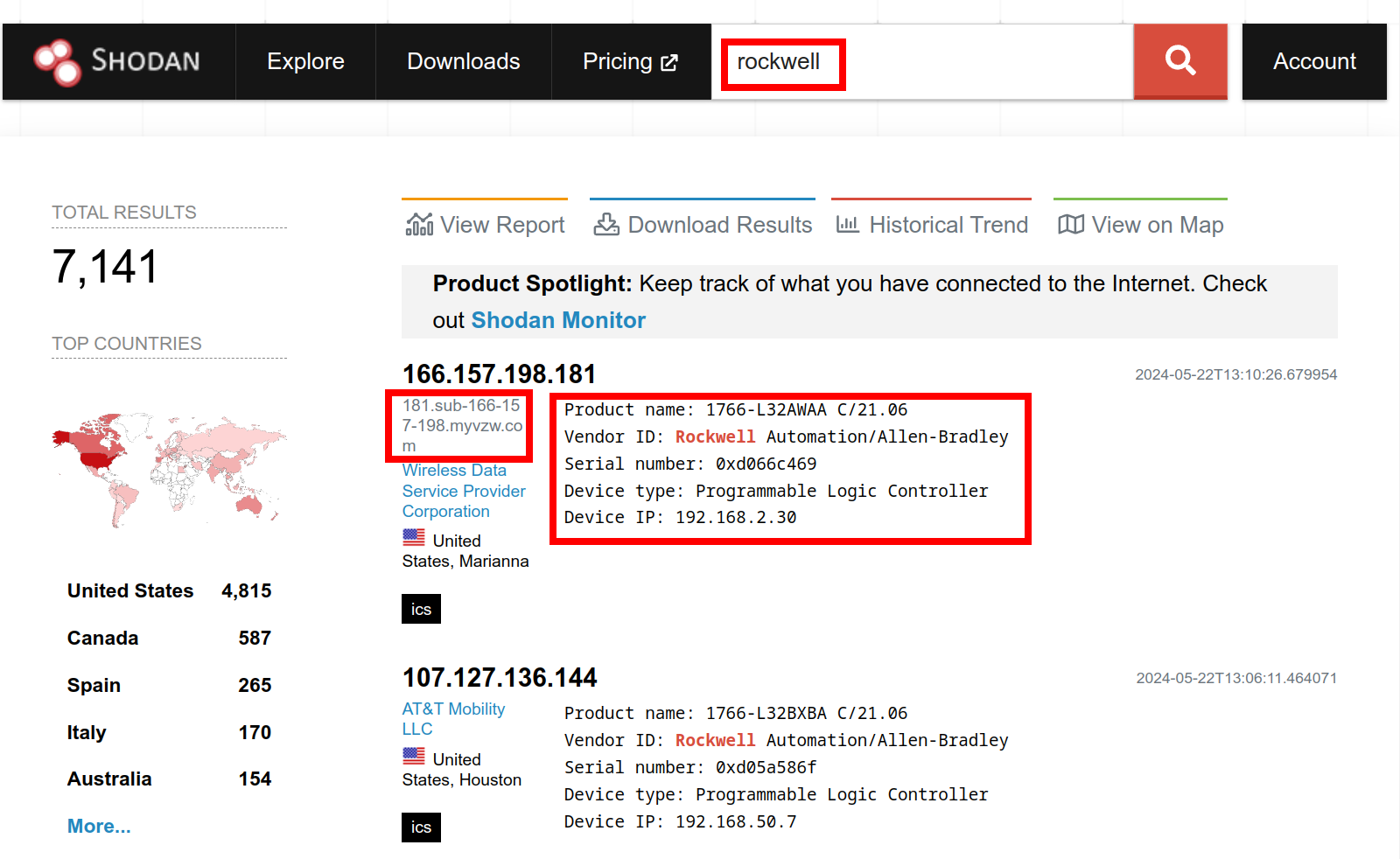
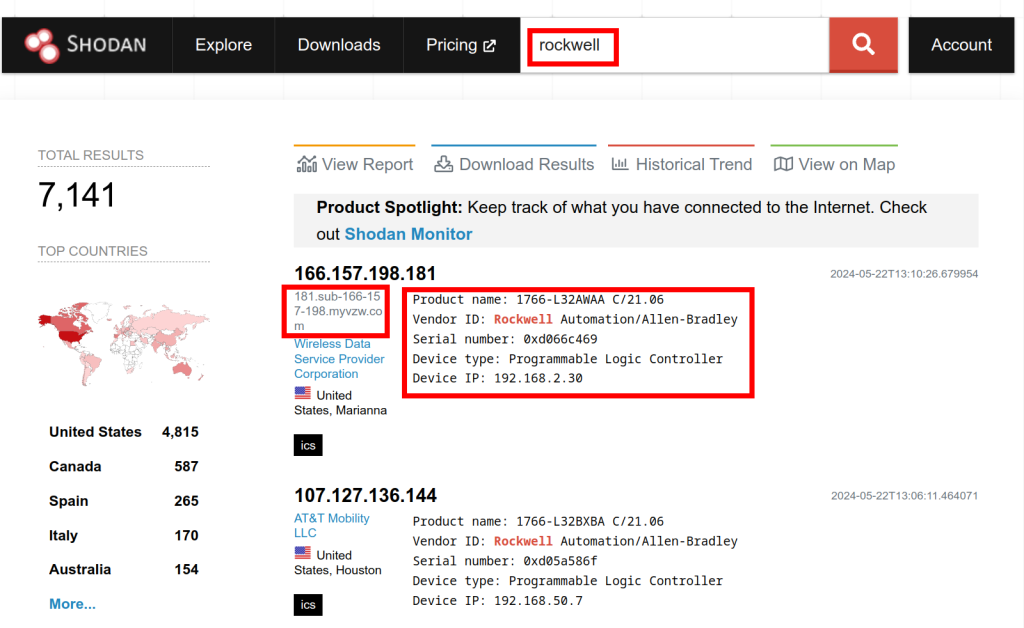
This got me thinking, surely no one would do that, right? One second, let me duck into Shodan.io and see. OK, people do. The ‘myvzw’ is a Verizon sim card or Mifi type device. The one below is same but for AT&T. Indeed you can directly operate these PLC’s from the public Internet without any security, any authentication, any authorisation.
In “Howto: Open Source Intelligence and your Digital Footprint” I show some of the techniques you can use.