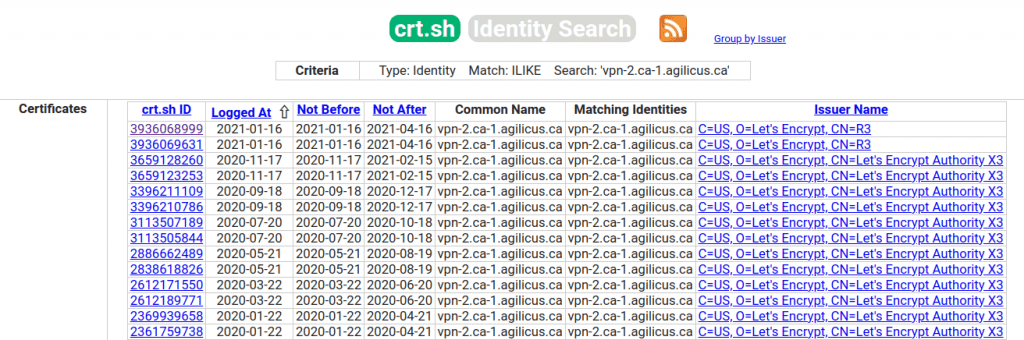
Recently Let’s Encrypt switched how they issue their intermediate certificates. You can read all about it. The main goals are reducing certificate size (moving from RSA to ECDA), speed, reliance.
As of September 2020, the Let’s Encrypt hierarchy looks like:
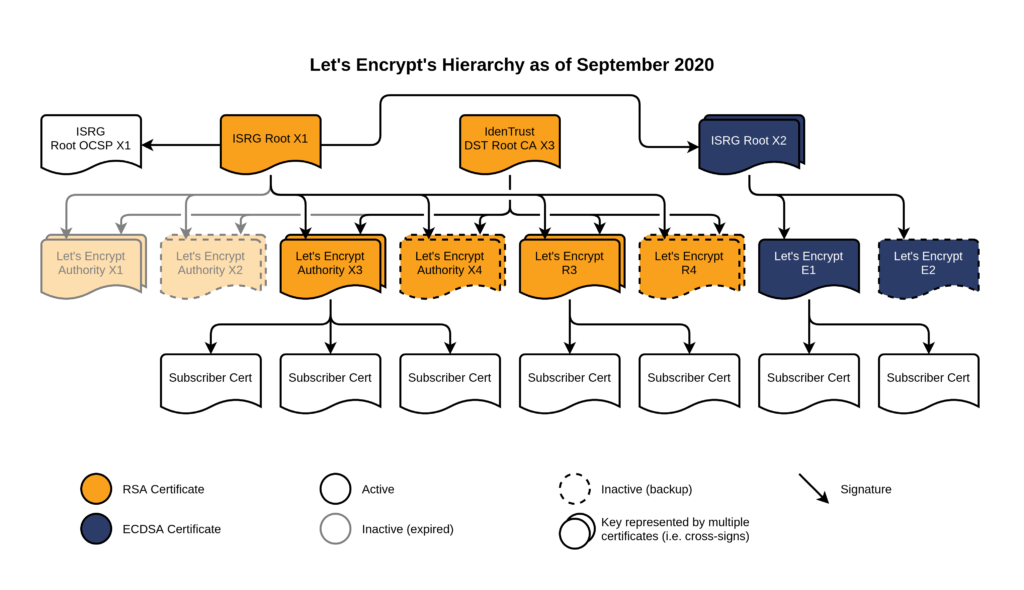
Recently Agilicus had a problem with one of our customers. Our IPSEC VPN dropped after rotating the Let’s Encrypt certificate from the X3 to the R3. And, we wanted to see when that happened, what was issued, etc.
Enter the Certificate Transparency Log. You can try this at https://crt.sh. You go to that site, enter a domain name, and it shows all the certificates issued (by any provider supporting transparency). This would be a key activity you would do:
- When obtaining a new domain name. Check if there are any outstanding certificates someone else is in possession of
- If you are worried about spearphishing of your domain via typosquatting, you could check for certificates being issued to doppleganger domains
- When wanting to understand when it was rotated. This is the case we used.
By looking at the report for our domain, we see that it started using the ‘R3’ issuer today. It would appear that the other end (Palo Alto) is having some trouble with it. I’m not clear why, since the change is to add a 2nd cross-signed root (X2), not removing X1.