Who are you? Identity involves knowing who you are, and then later proving it. NIST sp 800-63A enrollment is the first step, let’s talk about that!
NIST sp 800-63A covers “How do I become aware of who you are for the first time’, also known as enrollment. In NIST sp 800-63B: How Well Do I Know You I covered how we would authenticate you the 2nd and subsequent times, but here we talk about that first time, the unambiguous ‘who are you” setup, and the levels.
The NIST sp 800-63A covers 3 levels of “how well do I know your identity”. Quoting from the standard:
IAL1: There is no requirement to link the applicant to a specific real-life identity. Any attributes provided in conjunction with the subject’s activities are self-asserted or should be treated as self-asserted (including attributes a CSP asserts to an RP). Self-asserted attributes are neither validated nor verified.
IAL2: Evidence supports the real-world existence of the claimed identity and verifies that the applicant is appropriately associated with this real-world identity. IAL2 introduces the need for either remote or physically-present identity proofing. Attributes could be asserted by CSPs to RPs in support of pseudonymous identity with verified attributes. A CSP that supports IAL2 can support IAL1 transactions if the user consents.
IAL3: Physical presence is required for identity proofing. Identifying attributes must be verified by an authorized and trained CSP representative. As with IAL2, attributes could be asserted by CSPs to RPs in support of pseudonymous identity with verified attributes. A CSP that supports IAL3 can support IAL1 and IAL2 identity attributes if the user consents.
NIST sp 800-63A
Paraphrasing, in level-1, you can create sock-puppet accounts, as many as you like. In level-2 you exist (this is getting kind of existentialist sartre descartes, right)? In level-3 you exist and were there in person to prove it.
Now, there’s a brief segue into privacy. You can exist, prove you exist, and still not give all of your details each time. The attestor in level 3 might need your passport, birthdate, and a photocopy of that mole on your butt. But, the subsequent system that identifies you downstream might replace all this with its own trust “user42 is who they say they are” without more details. The more details the attestation of level 3, the more you might care (since, unlike a password, you cannot change your identity… your biometrics, your DNA, etc).
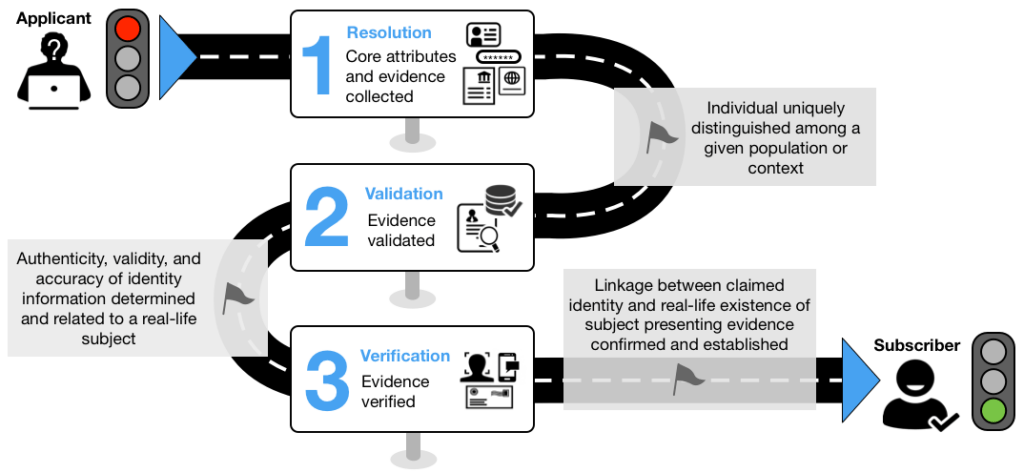
The NIST sp 800-63A relies on traditional real-world identity (name, date of birth, home address). The general idea is these are hard to fake, and presence of one or two is usually unambiguous.
The NIST sp 800-63A standard goes through three general stages: collect, validate, verify.
Since identity is intertwined with Personal Identifiable Information (PII), there is a lot of the NIST sp 800-63A standard dedicated to what to collect when.
- Identity proof is not related to entitlement to a service
- Limit to minimum necessary to validate claimed identity
- Indicate purpose at time of collection
- Provide redress mechanism for complaints
- Have a written policy
- Maintain audit log record of all steps taken, including PII examined
- Protect PII
- Perform transactions over secure (encrypted, authenticated) channel
- Use fraud detection (e.g. anomaly detection, geolocation, etc). This might involve checking against e.g. the US Social Security “Death Master File” (am I alive?)
- Delete data when you stop being an identity provider
- Do not collect (US Social Security Number)
In NIST sp 800-63A level 1, the user self-attests: there is no validation. Think your reddit account. I am since I say I am.
In NIST sp 800-63A level 2, you can be remote or in-person. PII is required, but minimised. At least one piece of ‘STRONG’ (‘SUPERIOR’) evidence is needed if the source had two. Note: this is sort of like the stratum-1/2/3 clocks in NTP. The place I check identity against needs to be stronger than I need. Also, interestingly, Knowledge-based is not used (e.g. I cannot use the fact I know you already). Physical address checks are done (e.g. sending a postcard). Interestingly, a PSTN number can be used here (I trust the phone company?). No word on the homeless or indigent.
In NIST sp 800-63A level 3 we get serious. Biometrics are a must. We check for duplicate enrollment. We have a method to re-adopt previous identity (no right to be forgotten here). And, we do it old school, face-to-face in person. With 2 pieces of strong evidence.
The NIST sp 800-63A standard provides a summary table:
| Requirement | IAL1 | IAL2 | IAL3 |
|---|---|---|---|
| Presence | No requirements | In-person and unsupervised remote. | In-person and supervised remote. |
| Resolution | No requirements | The minimum attributes necessary to accomplish identity resolution. KBV may be used for added confidence. | Same as IAL2. |
| Evidence | No identity evidence is collected | One piece of SUPERIOR or STRONG evidence depending on strength of original proof and validation occurs with issuing source, or Two pieces of STRONG evidence, or One piece of STRONG evidence plus two (2) pieces of FAIR evidence. | Two pieces of SUPERIOR evidence, or One piece of SUPERIOR evidence and one piece of STRONG evidence depending on strength of original proof and validation occurs with issuing source, or Two pieces of STRONG evidence plus one piece of FAIR evidence. |
| Validation | No validation | Each piece of evidence must be validated with a process that is able to achieve the same strength as the evidence presented. | Same as IAL2. |
| Verification | No verification | Verified by a process that is able to achieve a strength of STRONG. | Verified by a process that is able to achieve a strength of SUPERIOR. |
| Address Confirmation | No requirements for address confirmation | Required. Enrollment code sent to any address of record. Notification sent by means different from enrollment code. | Required. Notification of proofing to postal address. |
| Biometric Collection | No | Optional | Mandatory |
| Security Controls | N/A | SP 800-53 Moderate Baseline (or equivalent federal or industry standard). | SP 800-53 High Baseline (or equivalent federal or industry standard). |
Now, here’s where it gets interesting. Its one thing to say “I am X”, its another thing to say “let me figure out who you are”. Think the difference between a passport to let you in to the country vs dental records to prove who these beautiful ashes belong to. In the first case, the test is easier. “Identity XXX, lookup and match”. In the other, its “here is a set of factors we know, search all and find the one and only best match”.
The last section of NIST sp 800-63A is also quite interesting, the derived credentials. This is a way to go from e.g. stratum 1 (the source) to stratum 2 (a system) to stratum 3 (e.g. a smart card on your belt). In it you can restrict access to some of the facts and rely on the chain of trust.
So. We have now talked about “How do I know who you are” the first time, the levels (1/2/3), and some of the items to consider. Identity, and authentication against it, are a key aspect of any security system. Want to discuss more? Please feel free to reach out!
