Agilicus AnyX Product Guide
Individual product guide pages are laid out below as cards. These are intended to be linked and navigated within the Agilicus AnyX administrative web interface, but are available here for reference.
For any product support needs, email support[@]agilicus.com, or use the Chat icon on the lower browser edge.
See system status.
See a set of worked-out application notes / examples, each showing a specific use case and how to achieve it.
See, follow, subscribe to a set of articles on tips, tricks, best practices on using Agilicus AnyX.
Below is a list of all product guide pages. These are directly accessible from the admin web interface (https://admin.__MYDOMAIN__/).
-
Administrative Users
Administrative users are assigned via System Groups (sysgroups). These allow you to control who can make changes, to what objects.
-
Agilicus AnyX Demo
Evaluate the Agilicus AnyX platform with a canned, built-in, fully functional demo environment. Nothing to install.
-
Agilicus Connector
The Agilicus Connector facilitates connectivity from a private site to external users.
-

Agilicus Connector – Container/Docker
Install an Agilicus Connector in a container (e.g. Docker)
-

Agilicus Connector – Export Certificate
Have a local resource that should be properly TLS encrypted and publicly trusted certificate? The Agilicus Connector can facilitate this.
-

Agilicus Connector – GL-MT3000 (Beryl AX)
Install an Agilicus Connector on an OpenWRT-based GL-MT3000 Beryl AX
-

Agilicus Connector – Microsoft Windows
Install and diagnose the Agilicus Connector on Microsoft Windows
-

Agilicus Connector – NanoPI R2S
Agilicus Connector and NanoPI R2S. 2xGE, 1GiB RAM, 32GB eMMC, large passive heatsink. An excellent small embedded platform.
-

Agilicus Connector – NanoPI R5S
Install an Agilicus Connector on an OpenWRT-based NanoPi R5S.
-

Agilicus Connector – QNAP
Agilicus Connector – QNAP. Install the Agilicus connector on a QNAP NAS
-

Agilicus Connector – Snap
Install an Agilicus Connector on a Snap-based Ubuntu Core system. Agilicus Connector – Snap
-

Agilicus Connector High Availability
Install and Operate the Agilicus Connector in a high-availability, high-resilience mode.
-
Agilicus Connector Kubernetes
The Agilicus Connector includes a standard container-runtime and automatic installation for Kubernetes. This allows exposing internal Kubernetes services with an OpenID Conect Identity Proxy. Agilicus Connector Kubernetes
-

Agilicus Connector Mikrotik Router
The MikroTik RB5009UG+S+IN is a small-form factor router. it is a good vantage point to run the Agilicus Connector. Agilicus Connector Mikrotik Router
-

Agilicus Connector Sign-In
The Agilicus Connector creates a service account on installation, bootstrapped via a browser from the Administrator who is installing it.
-

Agilicus Connector Windows Cluster
Install the Agilicus Connector to be high-availability in a Microsoft environment.
-
Agilicus Connector in Private VPC In AWS EC2
Private IP only in your VPC? Need to ssh or remote desktop or share some files? This example shows a setup.
-

Agilicus Launcher (Desktop)
Automatically mount a Share, launch a local application. With multi-factor authentication. Without a VPN. Automated rollout to all users.
-
Agilicus VAR and Supporting Companies
Create and operate your own customers under your Agilicus Organisation as a VAR or other supporting company.
-

Application Request Access
Your organisation has a dynamic workforce, and a dynamic list of applications that they use to be efficient. A self-discovery, self-request workflow is more efficient than a command-and-control model.
-

Applications
Agilicus Web Applications: any web page or API, any user, no VPN, full web-application-firewall authentication
-
Audit Destinations
Audit records are written for events ranging from authentication, authorisation, and API access. Configure how to receive these.
-
Authentication Audit
Authentication audit shows events related to user identity, each step, multi-factor, policies, locations, etc. E.g. ‘sign-in’ obtain id token.
-
Authentication Clients
The Authentication Clients implement OpenID Connect client id. This is an advanced setting, it is rarely required to configure. These are created automatically for each web application.
-

Authentication Issuer – Custom Identity
An Authentication Issuer holds and confirms Identity. Configure your own custom ones here.
-

Authentication Issuer – Onsite Identity
An Authentication Issuer holds and confirms Identity. Configure your own custom ones here.
-
Authentication Rules
Authentication rules allow providing conditional-access rulesets during the authentication process. IP range, device, multi-factor, etc.
-
Auto-Create Users From Specific Domain With Google Workplace
Create a customised Sign In With Google (for e.g. Workplace with auto-create users)
-
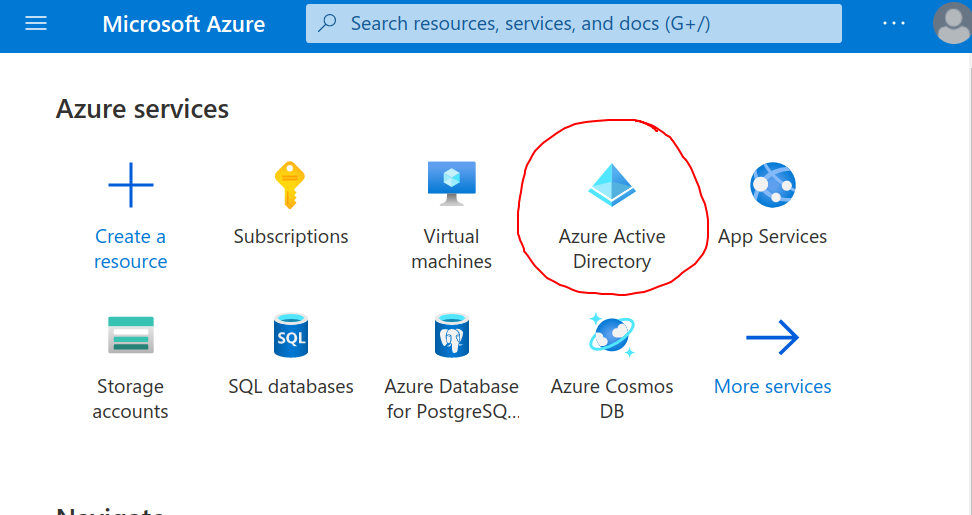
Azure Active Directory
Azure Active Directory provides an OpenID Connect Federated Identity Endpoint. Learn how to configure.
-
Billing
Update address, payment information, see previous invoices
-

Cisco IOx Zero Trust Connector Install
Cisco IOx Zero Trust . Configure a Cisco IR1101 IOx with Agilicus Connector. Zero Trust Remote Access to it, to IoT beyond it.
-
Command Line API Access
Your application also behaves as an API, used by a CLI or other non-browser-based application. Here you can see how to use via HTTP proxy or token.
-

Connector Install: GL-RM1 KVM
The GL.iNet GL-RM1 is a simple, economical, remote Keyboard/Video/Mouse (KVM) device. It offers an excellent platform to install the Agilicus Connector, giving yourself remote access to a server from anywhere.
-

Connector Install: Netgate SG-1100 pfSense
The Netgate SG-1100 pfSense is a small-form factor router. it is a good vantage point to run the Agilicus Agent Connector.
-
Connector Install: Raspberry Pi
The Raspberry Pi makes an excellent platform to install the Agilicus Agent Connector. See the general instructions here.
-

Connector Install: Ubiquiti EdgeRouter X
The Ubiquiti EdgeRouter X (ER-X/ER-X SFP) is a small-form factor router. it is a good vantage point to run the Agilicus Agent Connector.
-
Content Security Policy
Content-Security-Policy is a set of headers to protect your application from malicious content in objects, scripts, images, frames, etc.
-
Databases
Direct database application via a connection/template file for applications like QField.
-
Define Application: Proxy
An Identity-Aware Web Application operates as a proxy, bringing identity, authentication, authorisation on behalf of web applications.
-
Firewall rules
Firewall Rules Web (HTTP) Firewall Setup Firewall Rules Identity is “who” a user is. Authentication is how a user “proves” their Identity Authorisation is “what” a user is allowed to […]
-
Forwarding
Network Resources may be forwarded from site to site or user to site. This allows you to e.g. expose an ERP or database without a VPN.
-

Geo-Location-Based Access Control
It i possible to allow/deny access to individual resources based on the country their inbound IP is coming from.
-

Groups
Groups simplify assigning permissions. Assign users to one or more groups. Assign groups to groups Assign permissions to groups. Administrators, tech-support, etc.
-

Hosted Applications
An application manages web-based applications, API’s, anything which uses HTTP as a transport. It encompasses a Web Application Firewall, an Identity Proxy, and fine-grained Authorisation and Audit.
-
Identity & Authentication Methods
You can theme the authentication (sign-in) screen your users see. Learn how.
-
Identity Group Mapping
Map your local directory groups into Agilicus AnyX, simplify configuration and maintenance
-

Labels
Users, Resources may have an arbitrary set of text-based labels. These labels can be used for a variety of purposes, including showing alternate hierarchy in Profile, viewing filters in alarms, setting downtime, etc.
-

Launchers
Integration of Resources with the Desktop is achieved through the Launcher. – Mount a Share – Open an SSH – Open a Desktop – Launch an executable
-
Legacy Active Directory
On-premise legacy active directory with ADFS can act as an OpenID Connect Identity Provider. Learn how to configure.
-

Linux, FreeBSD, Embedded Connector Install
The instructions to install the Agilicus Agent Connector are nearly identical on various Unix operating systems. This includes desktops, servers, and embedded devices.
-

Microsoft ClickOnce
Deploy with Microsoft ClickOnce. Secure with Agilicus Zero Trust. Single-Sign-On, no VPN. Seamless end user experience.
-

Moxa UC-8200 Zero-Trust Connector Install
Moxa UC-8200 Zero-Trust. Configure a Moxa UC-8200 Industrial PC with the Agilicus Agent Connector.
-
Multi-Factor Authentication
Multi-factor authentiction. Configure how, when, how often, users are required to supply a 2nd factor to sign in.
-
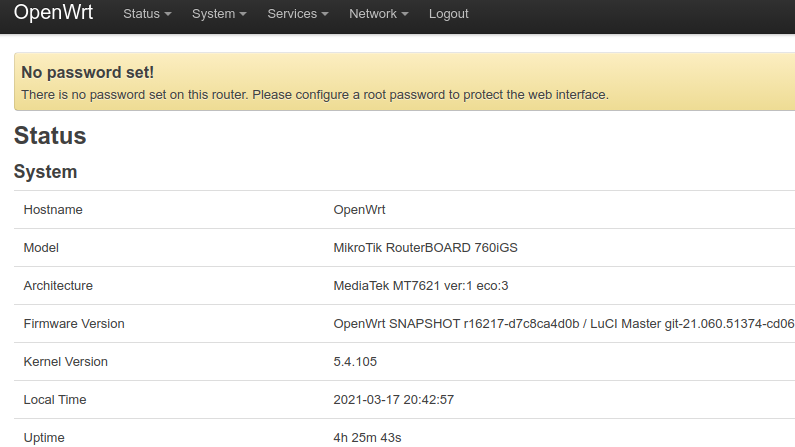
OpenWRT Connector Install
Configure an OpenWRT Router with the Agilicus Agent Connector.
-

Organisation
An organisation (tenant, project in some other systems) is a span of control, of permissions, of users.
-

Permissions
Permissions. Per user, per group, per application. Permissions can be by HTTP method, parameters. Fine-grained.
-

Phoenix Contact PLCnext AXC F 2152
Install the Agilicus connector directly on the Phoenix Contact PLCnext for highest security and simplest deployment.
-

Policies
There are 3-phases in the life cycle of usage: Authentication, Authorisation, Access. People commonly refer to ‘multi-factor authentication’, which enriches the information a user must know/have/be in order to properly authenticate themselves. However, some security policies cannot be modelled simple as “do I know who this person is” in the authentication phase. These must be evaluated continually, rather than once when the user provides credentials. Below are a few example security policies that cannot be modelled solely with authentication.
-
Pre-Setup Checklist
Pre-Setup Checklist Setup your DNS Setup your Firewall Make your Agilicus AnyX Signup & Setup go smoothly. Pre-Setup Checklist To reduce time during Agilicus AnyX signup, follow the below checklist […]
-

Profile
End user profile. Access applications, shares. Set up multi-factor authentication.
-

Resource Groups
Resource groups are a means of applying a common configuration across a set of resources (connectors, applications, shares, etc)
-

Resources – Overview, Concepts
Overview, Concepts Resources
-
Sample Ubiquiti EdgeRouter-X EdgeMax Web Interface
Sample Ubiquiti EdgeRouter-X EdgeMax Web Interface
-
Service Accounts
A service account is a specific subset of permissions assigned to a non-human user. The most common use is the Agilicus Agent Connector.
-
Services
A ‘service’ is a global resource (usually TCP) available from your domain of control to web applications running in the platform.
-
Shares
Shares are a means of taking a directory on a local server and making the contents available to any user, without a VPN and with out a client.
-

Sign Up
Agilicus Platform provides Zero-Trust hosting and access, simply, securely. Any user, any device, any network. Strong identity.
-
Sign in With Apple
Sign in with Apple allows you to use resources through the Agilicus platform authenticated by an Apple ID.
-

Sign in With Microsoft
Sign in with Microsoft to the Agilicus Platform. Ramificatiosn of Shared vs your own Azure Active Directory Application.
-

Sign-In Errors
Explain the various errors a user might see on sign-in
-
Sign-In Theming
You can theme the authentication (sign-in) screen your users see. Learn how.
-

Signup: Firewall Configuration
Restrictive firewalls (e.g. Palo Alto SSL) may filter by SNI (hostname) in outbound direction and break Signup. See how to configure.
-

Site Firewall Configuration
Restrictive firewalls (e.g. Palo Alto SSL) may filter by SNI (hostname) in outbound direction and break Signup. See how to configure.
-

Sub Organisation Issuer
You can now create an issuer for a suborganisation from a parent organisation. Doing so will bring up a new admin/profile endpoint for the suborganisation, at the suborganisation’s subdomain. E.g. admin.suborg.myorg.cloud.
-

Support
Interacting with Agilicus Support
-
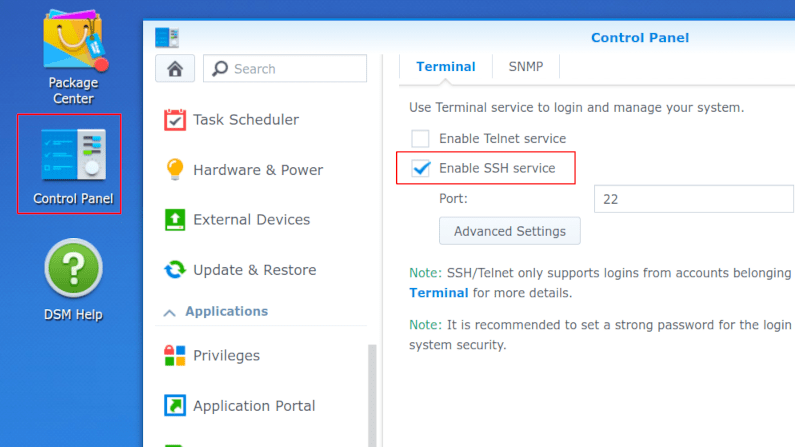
Synology Connector Install
Configure a Synology NAS with the Agilicus Agent Connector.
-
Theory of Operation: CNAME + DOMAIN
Theory of operation: initial setup, choose a domain name, set the CNAME wildcard.
-

Time Synchronisation
Proper time synchronisation is important for encryption and access control. Access tokens have a not-before/expiry date that must be understood.
-

Usage Metrics
Platform usage metrics are available showing top-users and overall active counts.
-
Users
Users. Individual human or system accounts that can be granted permission. Typically users are people, and, are tied to Agilicus AnyX via single-sign-on to an existing identity provider.
-
Using RemoteApp With Windows 2012R2
A visual guide to configuring Microsoft RemoteApp on Windows Server 2012 R2. This walkthrough provides screenshots detailing the necessary steps to publish and manage remote applications, enabling seamless and secure access for users.
-
VNC Desktop
The VNC Desktop feature allows browser-based use of remote graphical-oriented resources. This can include traditional operating systems like Windows, Linux, MacOS, but, also, includes embedded devices such as HMI.
-

Variable Expansion
Variable expansion in strings can make mounting shares, or configuring desktops simpler
-

WAGO Edge Controller
The WAGO Edge Controller is a flexible and open control platform for many embedded and industrial applications. It provides an excellent vantage point to run the Agilicus Connector.
-

Web Application Password Injection
Learn to configure automatic login for web apps by mapping authenticated Agilicus AnyX users to a weak internal user with a hidden password.
-

Web Application Security
The Agilicus AnyX Web Application Firewall can be used to apply a set of Content-Security, XSS, CSRF rules to a proxied web application.
-

Zero-Trust Desktop Access
Simplify and secure your Desktop Access. Fine-grained authorisation per Desktop. Any user, from any identity provider. No public IP needed.
-

Zero-Trust SSH Access
Simplify your SSH access with Zero Trust. Direct access to any internal server, cloud VPC or VLAN without changing firewall.