Ubiquiti EdgeRouter X
Connector Install
The Ubiquiti EdgeRouter X (ER-X/ER-X SFP) is a small-form factor router. In addition to performing routing services, it is a good vantage point to run the Agilicus Connector if you already have it.
This is a low-performance device, we do not recommend purchasing new ones.
Connector Install: Ubiquiti EdgeRouter X
The Ubiquiti EdgeRouter X (ER-X/ER-X SFP) is a small-form factor router. In addition to performing routing services, it is a good vantage point to run the Agilicus Connector.
(Once you have completed these, you may wish to try accessing the EdgeRouter X web interface via the Agilicus Any-X platform, see example).
DEVICE WARNING
❗
Note: this device is a low-performance device with an older processor and low ram. If you have a need for more than a few services, or ones which need more than ~10Mbps of throughput, we recommend a newer device such as NanoPi, a Raspberry Pi, or a pfSense.
The below instructions were tested on an EdgeRouter X SFP with v2.0.9, specifically:
# cat /etc/version
EdgeRouter.ER-e50.v2.0.9-hotfix.2.5402463.210511.1317Installation
In the Agilicus Administrative Web interface, you will:
- Create Connector
- Copy the install command line
- Paste this into the ssh interface of the Ubiquiti EdgeRouter X
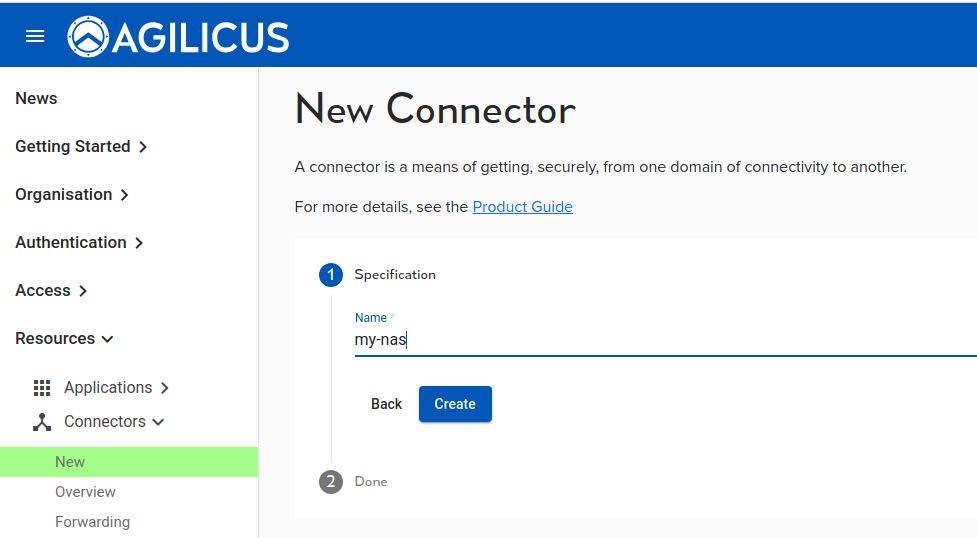
Step 1: Create Connector
Navigate (in the Agilicus admin web interface) to ‘Resources/Connectors/New’.
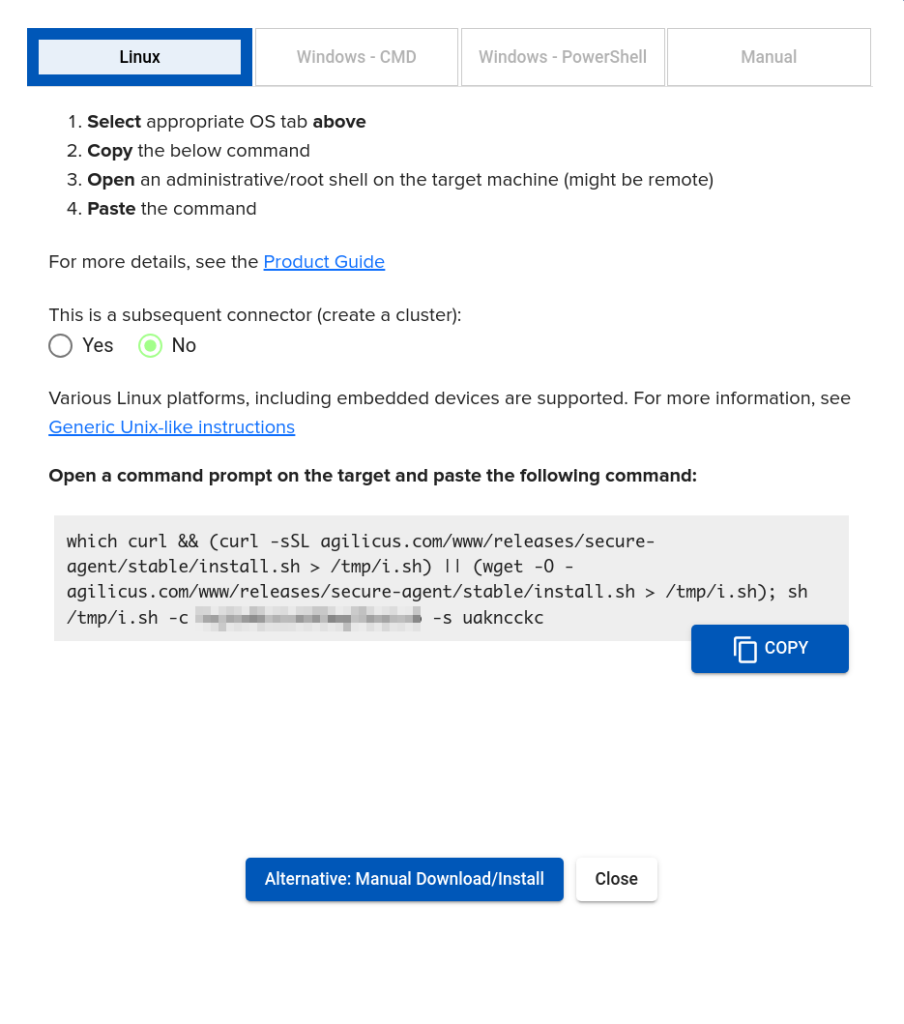
Step 2: Copy the install command line
Select “Linux”. Copy the command line to your clipboard. Run on the ssh interface to the ERX.
This command will fetch a script, and then run it with a time-limited challenge.
Note: the command line looks complex since it must run on multiple platforms, some of which have curl, some of which have wget, but it effictively fetchs a single install script and runs it with 2 arguments. You may feel free to fetch the script and inspect it, run it manually.
You should now be complete.
A complete log of a successful install is shown below for reference.
don@machine$ ssh ubnt@172.16.0.13
_____ _
| ____|__| | __ _ ___ (c) 2010-2020
| _| / _ |/ _ |/ _ \ Ubiquiti Networks, Inc.
| |__| (_| | (_| | __/
|_____\__._|\__. |\___| https://www.ubnt.com
|___/
Welcome to EdgeOS
By logging in, accessing, or using the Ubiquiti product, you
acknowledge that you have read and understood the Ubiquiti
License Agreement (available in the Web UI at, by default,
http://192.168.1.1) and agree to be bound by its terms.
ubnt@172.16.0.13's password:
Linux erx 4.14.54-UBNT #1 SMP Tue May 11 13:23:28 UTC 2021 mips
Welcome to EdgeOS
Last login: Sat May 28 18:11:43 2022 from 172.16.0.8
ubnt@erx:~$ sudo su -
root@erx:~# which curl && (curl -sL agilicus.com/www/releases/secure-agent/stable/install.sh > /tmp/i.sh) || (wget -O - agilicus.com/www/releases/secure-agent/stable/install.sh > /tmp/i.sh); sh /tmp/i.sh JX2EXXXXXXXXXXXXEU https://auth.MYDOMAIN
/usr/bin/curl
Starting install... <JX2EXXXXXXXXXXXXEU> <https://auth.MYDOMAIN>
OS: <Linux>, Machine: <mips>, END: <le>
INFO[2022-05-28T18:32:33.787560338Z] Starting client - version v0.119.0
INFO[2022-05-28T18:32:34.923316902Z] Logging in...
You may see a browser open, in which case you may sign in automatically.
Failing that, if this machine is headless, or remote, you will see a URL below.
Copy and paste that into a browser you are logged into. You will then see a code,
paste it in below.
Please go to the following link in your browser to retrieve the authentication
code:
https://auth.MYDOMAIN/auth?client_id=agilicus-builtin-agent-connector&code_challenge=XXXXX&code_challenge_method=S256&redirect_uri=urn%3Aietf%3Awg%3Aoauth%3A2.0%3Aoob&response_type=code&scope=openid+profile+email+offline_access+urn%3Aagilicus%3Aapi%3Aapplications%3Areader%3F+urn%3Aagilicus%3Aapi%3Aapplications%3Aowner%3F+urn%3Aagilicus%3Aapi%3Atraffic-tokens%3Aowner+urn%3Aagilicus%3Aapplication_service%3A%2A%3Aowner%3F&state=XXXXX
Enter verification code: scpfcXXXXXpim4qq5pl
checking code
INFO[2022-05-28T18:33:23.875526942Z] Check if the agilicus-agent is already running as a service. If so stop it
INFO[2022-05-28T18:33:23.932589295Z] Create a directory at /etc/agilicus/agent
INFO[2022-05-28T18:33:23.934868328Z] Download public key file to /etc/agilicus/agent/public_key.json
INFO[2022-05-28T18:33:24.265979606Z] Create file /usr/bin/agilicus-agent-wrapper.sh
INFO[2022-05-28T18:33:24.266562921Z] Create file /etc/systemd/system/agilicus-agent.service
INFO[2022-05-28T18:33:24.273604799Z] Will install to /agilicus-agent-wrapper.sh -> {/usr/bin/agilicus-agent-wrapper.sh -rwxr-xr-x}
INFO[2022-05-28T18:33:24.278649712Z] Will install to /agilicus-agent.service -> {/etc/systemd/system/agilicus-agent.service -r--r--r--}
INFO[2022-05-28T18:33:24.282177117Z] Create a directory at /opt/agilicus/agent/tufmetadata/latest
INFO[2022-05-28T18:33:24.282578531Z] Create a directory at /opt/agilicus/agent/tufmetadata/stable
INFO[2022-05-28T18:33:24.285506591Z] Setup Agilicus secure store
INFO[2022-05-28T18:33:24.285945878Z] Create secure keyring for storing communication credentials in /etc/agilicus/agent
INFO[2022-05-28T18:34:25.392134745Z] Fetch agent configuration
INFO[2022-05-28T18:34:25.392429467Z] Write agent configuration file in /etc/agilicus/agent/agent.conf.enc.yaml
INFO[2022-05-28T18:34:26.432424427Z] Create a user and group named Agilicus to run the agilicus-agent service
INFO[2022-05-28T18:34:26.432722016Z] Copy executable to /opt/agilicus/agent
INFO[2022-05-28T18:34:26.432866291Z] Set permissions to Agilicus on /opt/agilicus/agent
INFO[2022-05-28T18:34:26.433163321Z] Create symlink from /usr/bin/agilicus-agent to /opt/agilicus/agent/agilicus-agent-mipsle
INFO[2022-05-28T18:34:26.914492417Z] Start agilicus-agent service
INFO[2022-05-28T18:34:27.898994929Z] Installation Complete
root@erx:~# systemctl status agilicus-agent.service
* agilicus-agent.service - Agilicus Agent
Loaded: loaded (/etc/systemd/system/agilicus-agent.service; enabled; vendor preset: enabled)
Active: active (running) since Sat 2022-05-28 18:34:27 UTC; 9s ago
Main PID: 23147 (agilicus-agent)
CGroup: /system.slice/agilicus-agent.service
`-23147 /usr/bin/agilicus-agent client --cfg-file /etc/agilicus/agent/agent.conf.enc.yamlNote: Missing Let’s Encrypt Intermediary
curl -k https://letsencrypt.org/certs/lets-encrypt-r3.pem -o /etc/ssl/certs/lets-encrypt-r3.pem
sed -i ‘/^mozilla\/DST_Root_CA_X3/s/^/!/’ /etc/ca-certificates.conf
update-ca-certificates
Note: Time Synchronisation (NTP)
Before running the install steps, ensure NTP (time synchronisation) is running. If you do not have your own NTP server, use pool.ntp.org (specifically, use 0.pool.ntp.org as a server name). NTP can be enabled in the ‘system’ menu.
$ show ntp
remote refid st t when poll reach delay offset jitter
==============================================================================
-216.197.156.83 .PPS. 1 u 51 64 1 44.325 -2.774 3.691
+198.245.55.137 15.254.136.119 2 u 48 64 3 31.049 3.062 2.792
*2001:1600:4:1:: .GPS. 1 u 48 64 3 117.633 0.569 1.495
+207.34.48.31 205.206.70.42 3 u 48 64 3 61.305 3.715 3.977