Network Facilitator
Agilicus Connector
The Agilicus Connector facilitates connection from a bastion network and end-users. It installs on a device somewhere inside the protected network, making an outbound connection.
Agilicus Connector Overview
The Agilicus Connector facilitates connection from a bastion network and end-users. It installs on a device somewhere inside the protected network, making an outbound connection.
If you are new to the system, you may try a full ‘demo’ setup with your own connector in a virtual enviroment in our system, with no install. See “Agilicus AnyX Demo“. When you ‘create a connector’ it will offer you a ‘demo’ this will create a new virtual environment to test in with no isntall, no obligation.
The Connector is self-updating. Once installed it will stay up to date. The live Changelog shows the updates that have occurred.
Connectors facilitate:
- shares [must have local access to the files)
- Web Applications (must have onward connectivity)
- Local authentication
- Network resources (e.g. SSH, Remote Desktop, VNC)
Theory of Operation
The Agilicus Connector creates an outbound connection, using HTTPS, to the Agilicus AnyX Cloud. This persistent connection is then used to route individual user requests back in to the appropriate resource.
Each individual inbound request first has the user identity checked (authentication), then has the user’s role (authorisation) checked, prior to being routed inwards.
The net affect is that no traffic arrives at the protected resources unless it is for:
- An authenticated user (optionally with multifactor authentication)
- An authorised action (e.g. can the user edit the wiki)
- A valid resource
This is a very strong guarantee, and, achieved without complex (or any) firewall rules.
The use of industry-standard HTTPS and WebSocket means inspecting firewalls such as Zscaler or PaloAlto can be used in the path.
If we expand the data flow for a hypothetical SSH client with animation, we will see the WebSocket flows (blue) establish, and then the ssh flow. The SSH flow is delivered from User to SSH server encrypted end-to-end: the host key is maintained intact.
High Availability Option
The Agilicus Connector supports high availability (resiliency), either natively, or, via Windows Clustering. See High Availability installation for more information.
-

Agilicus Connector – Container/Docker
Install an Agilicus Connector in a container (e.g. Docker)
-

Agilicus Connector – Export Certificate
Have a local resource that should be properly TLS encrypted and publicly trusted certificate? The Agilicus Connector can facilitate this.
-

Agilicus Connector – GL-MT3000 (Beryl AX)
Install an Agilicus Connector on an OpenWRT-based GL-MT3000 Beryl AX
-

Agilicus Connector – Microsoft Windows
Install and diagnose the Agilicus Connector on Microsoft Windows
-

Agilicus Connector – NanoPI R2S
Agilicus Connector and NanoPI R2S. 2xGE, 1GiB RAM, 32GB eMMC, large passive heatsink. An excellent small embedded platform.
-

Agilicus Connector – NanoPI R5S
Install an Agilicus Connector on an OpenWRT-based NanoPi R5S.
-

Agilicus Connector – QNAP
Agilicus Connector – QNAP. Install the Agilicus connector on a QNAP NAS
-

Agilicus Connector – Snap
Install an Agilicus Connector on a Snap-based Ubuntu Core system. Agilicus Connector – Snap
-

Agilicus Connector Air Gap Machine With Containers
Setup a host firewall to create a virtual airgap on a Linux machine running containers with the Agilicus connector.
-

Agilicus Connector High Availability
Install and Operate the Agilicus Connector in a high-availability, high-resilience mode.
-
Agilicus Connector Kubernetes
The Agilicus Connector includes a standard container-runtime and automatic installation for Kubernetes. This allows exposing internal Kubernetes services with an OpenID Conect Identity Proxy. Agilicus Connector Kubernetes
-

Agilicus Connector Mikrotik Router
The MikroTik RB5009UG+S+IN is a small-form factor router. it is a good vantage point to run the Agilicus Connector. Agilicus Connector Mikrotik Router
-

Agilicus Connector Sign-In
The Agilicus Connector creates a service account on installation, bootstrapped via a browser from the Administrator who is installing it.
-

Agilicus Connector Windows Cluster
Install the Agilicus Connector to be high-availability in a Microsoft environment.
-
Agilicus Connector in Private VPC In AWS EC2
Private IP only in your VPC? Need to ssh or remote desktop or share some files? This example shows a setup.
-

Cisco IOx Zero Trust Connector Install
Cisco IOx Zero Trust . Configure a Cisco IR1101 IOx with Agilicus Connector. Zero Trust Remote Access to it, to IoT beyond it.
-

Connector Install: Netgate SG-1100 pfSense
The Netgate SG-1100 pfSense is a small-form factor router. it is a good vantage point to run the Agilicus Agent Connector.
-
Connector Install: Raspberry Pi
The Raspberry Pi makes an excellent platform to install the Agilicus Agent Connector. See the general instructions here.
-

Connector Install: Ubiquiti EdgeRouter X
The Ubiquiti EdgeRouter X (ER-X/ER-X SFP) is a small-form factor router. it is a good vantage point to run the Agilicus Agent Connector.
-

Linux, FreeBSD, Embedded Connector Install
The instructions to install the Agilicus Agent Connector are nearly identical on various Unix operating systems. This includes desktops, servers, and embedded devices.
Installation
Installation of the connector is very simple: 3 steps.
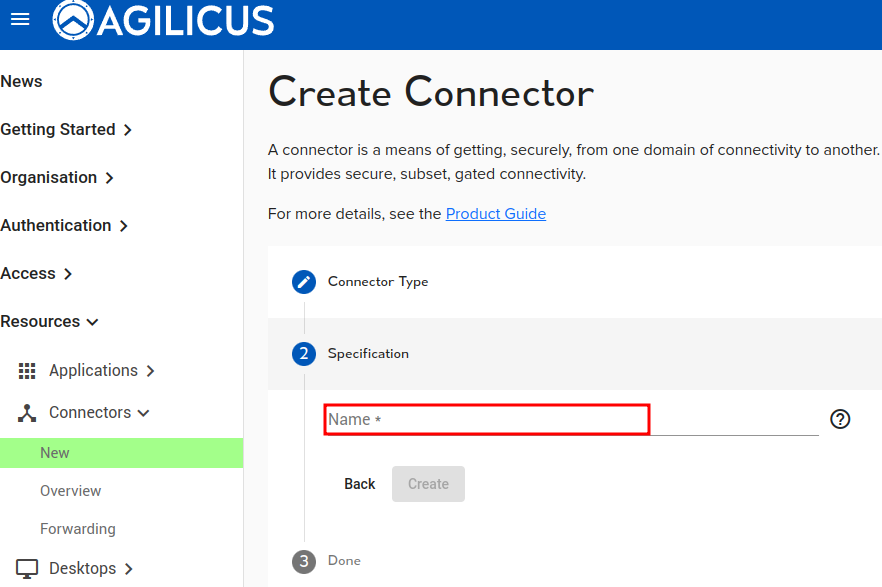
First, create (Admin console: Resources/Connectors/New)
Second, name (a name that means something, must be a valid hostname. E.g. the machine it is installed on, the site it connects, etc)
Third, install (paste the command on the target machine)
Once installed, the connector will keep itself up to date using The Update Framework.
During the creation of the Connector you will give it a name. This name should have some meaning for you, e.g. the site it is installed in, the host it is installed on, etc. We recommend it be the hostname that is running the Connector.
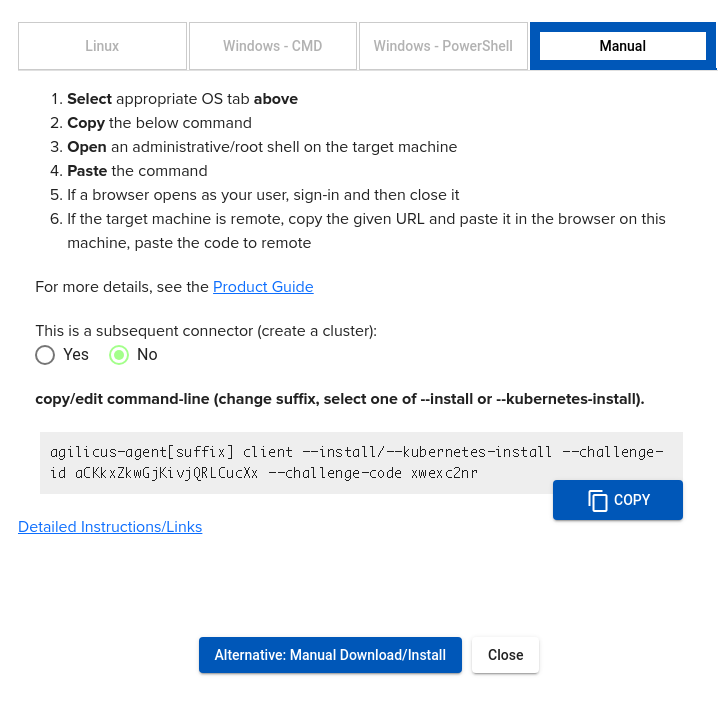
At this stage you will see a dialog giving installation instructions. At the top are 3 tabs (Linux, Windows-CMD, Windows-PowerShell).
The Linux tab should work on most Linux or FreeBSD-derived hosts, including pfSense, OpenWRT, Ubuntu, Debian, Synology, etc.
On a Windows host it does not matter which of the two instruction you follow, they will lead to the same result. Typically you will use the ‘cmd‘ instructions.
In all 3 cases, copy the text box (using the blue-button at the bottom right) and paste it into an administrative shell.
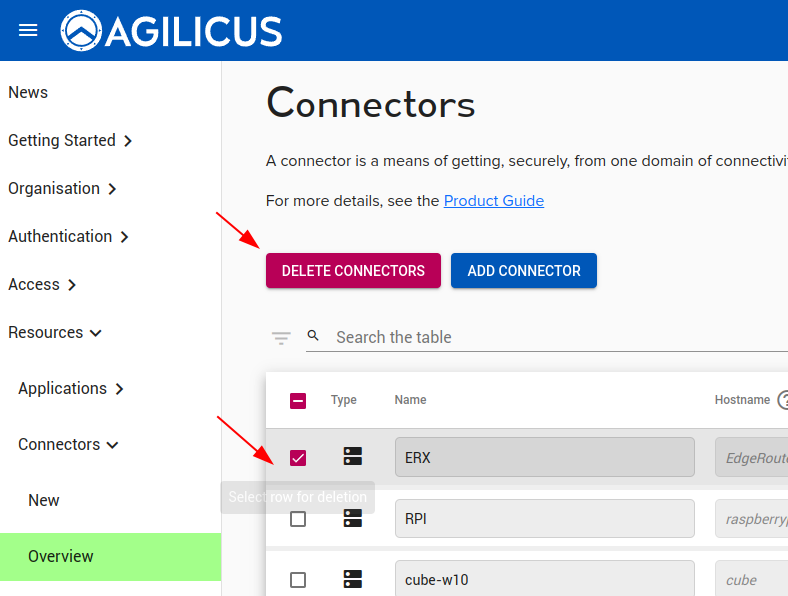
Uninstall / Delete
When you no longer need an Agilicus Connector, you should first uninstall it from the host it is on. Then you may delete it from the Admin portal.
Typically on Linux you will run:
sudo /usr/bin/agilicus-agent client --uninstallTypically on Windows you will run:
"%ProgramFiles%\Agilicus\agent\agilicus-agent client" --uninstallManual Download
Typically the installation is done from the Agilicus Admin portal. This will give you a link per platform. In rare cases you may wish to manually download, the linux are below for convenience. NOTE: you will need a ‘code’ from the admin web interface to install (under Resources/Connectors/New).
- Linux X86_64 (e.g. Ubuntu, Debian server)
- Linux ARM (e.g. Synology NAS, OpenWRT)
- FreeBSD ARM (e.g. pfSense SG-1100)
- Linux MIPS Big Endian (e.g. OpenWRT etc. router)
- Linux MIPS Little Endian (e.g. OpenWRT, Ubiquiti etc router)
- Linux PPC Big Endian (e.g. OpenWRT etc. router)
- Linux PPC Little Endian (e.g. OpenWRT, Ubiquiti etc router)
- Microsoft Windows
- MacOS Darwin (X86-64)
More Information
Below you will see cards for specific aspects of the connector (theory of operation, installation onto various platforms such as pfSense, Mikrotik, OpenWRT, Windows, etc.)