Ransomware is one of the most successful cyber crimes of recent years. A criminal gains access to your network, encrypts your data, asks for money to return it. If you don’t pay, they threaten to release it publicly. Most organisations pay. The payments are large enough, and frequent enough, to be a motivator for the criiminals, and small enough to not be a motivator for the international police co-operation needed. Let’s fix this with Zero-Trust.
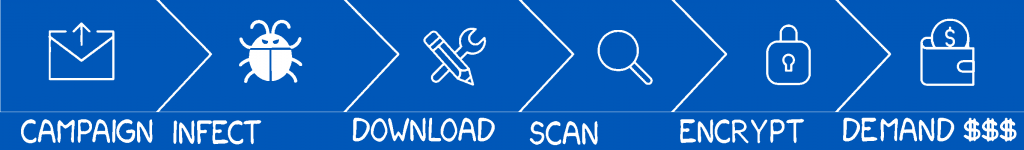
The most successful ransomware follows a simple pattern. A distribution campaign tricks one user into running something (through spear phishing, social engineering, etc.). This malicious code fetches the ransomware, which then scans the local machine, and all connected machines. It encrypts everything it finds and then generates a ransom note.
The most common means of sharing files in todays corporate world is the Microsoft SMB (CIFS) protocol. You see this as a ‘share’. And these shares are a fertile breeding ground for ransomware. In a typical small corporate environment all your desktops directly access a small number of servers. And, importantly, the servers can all access each other. This system is only as strong as its weakest link. And here, the weakest link, is you. And the route from you to your corporate world is the SMB protocol. Click a spearphishing link? It takes out your machine, and everything your machine can access, and everything those machines can access. You are 2 or 3 hops away from your entire company.
What can we do about this. Well, educate users, install endpoint security, that sort of thing. Nothing wrong there, certainly best practices. But it hasn’t worked. Bad ransomware happens to good people. So ransomware happens, people pay, the cycle continues. What can we do better?
First, we adopt a principle of Defense In Depth. Instead of a single (presumed) infinitely strong security point (the Firewall, the VPN), we assume each layer of our defense will be breached. We switch to a set of fallback positions, delay the attacker, shift the cost from us to them. Think trench warfare rather than a single combat line.
Zero-Trust is the principal of switching from a perimeter-based trust model (you -> VPN -> building) to a user -> resource model (you to application-1). In doing so, you end up with a set of point-to-point links rather than a point to “whatever” link. In adopting Zero Trust, we are adopting Defense in Depth. We assume one user might become compromised. From there, rather than them having access to everything directly, they only have access to what they need. And, those systems in turn only have access to what they need. We have limited the blast radius.
But we can go one step further. We can stop using the SMB protocol to share in a hub-and-spoke model everything to everything. We can instead use WebDav. Same affect for the user: a remote directory is shared locally. But, more importantly, we can apply fine grained role-based access control. Since WebDav is HTTP, it doesn’t suffer from the same complex-protocol weakness that has enabled SMB to become such a transmission route. Users are now more loosely coupled, they don’t need to have a direct link to the Domain Controller, to the File Servers.
Coming back to what the criminals do here. They encrypt your data and ask for money. But, did they merely encrypt it? Or did they also exfiltrate it? When you refuse to pay you find they suggest they’ll leak your private data to the web. When ransomware happens the first thing you will ask is: what data, where did it go, what accessed it? In a traditional ‘walled-garden’ approach, we cannot ascertain this. Once inside the firewall & VPN you have unfettered access to everything, without access control, without audit. Zero Trust fixes this two ways. First, removing the walled garden means we are authenticating to each resource, so we can see who accessed. But, the Zero Trust agent can also product audit logs of what was accessed.
Zero-Trust implemented means a dramatic reduction in the risk of ransomware. Both the risk of getting it, and, the risk of it spreading. It allows you to ascertain who got what, when while simultaneously reducing the amount of who, the amount of what.
Simple for the users, Secure for the company. Defense in Depth via Zero-Trust is better.
