All-in-one Zero Trust Platform
Simple, Secure Access through Agilicus AnyX
Provide simple, secure access to critical information and operational technology systems through a Zero Trust Architecture.
Agilicus AnyX implements a “never trust, always verify” security framework that is easy to manage and scales with your organisation.
Secure Remote Access through Agilicus AnyX
With a foundation in Zero Trust, Agilicus is transforming the way modern workforces connect to corporate resources whether information systems or operational technology. Today’s mobile users, frontline workers, contractors, vendors and partners can be equipped with the secure access that was previously unattainable. Organisations can adopt cloud-native security while authorised users can get secure, frictionless access to applications, desktops, shares, and other corporate resources and services. Administrators and IT teams are empowered with the ability to pair users with only the resources they need to do their job.
Centralize Permissions
Fine-grained authorisation and privilege management paired with detailed auditing across resources delivers granular capabilities for assigning permissions across user groups.
Simplify Access
Reduce costs and improve security while enabling a frictionless experience across the value chain of users, administrators, and operators.
Onboard Any User
Embrace unique sources of identity and federate it into a single form of authentication for all internal and external users.
Modernise your organisation and streamline the way your users get access to shared resources with a secure alternative to VPNs and perimeter-based network access.
Any User, on Any Device, to Any Resource
Agilicus’ novel Zero Trust Network Access platform empowers any organization to provide single sign-on, with existing credentials, to any resource, using any device, without a VPN or client – simply, securely, and economically.
Unify Identity Across your Workforce with Federated Identity
A core principle of Zero Trust is identity-based access where every individual must prove who they are in a process known as authentication. This can be achieved through the use of corporate email addresses which allows a given user to verify their identity through something they know (their email credentials) and something they have (multi-factor authentication).
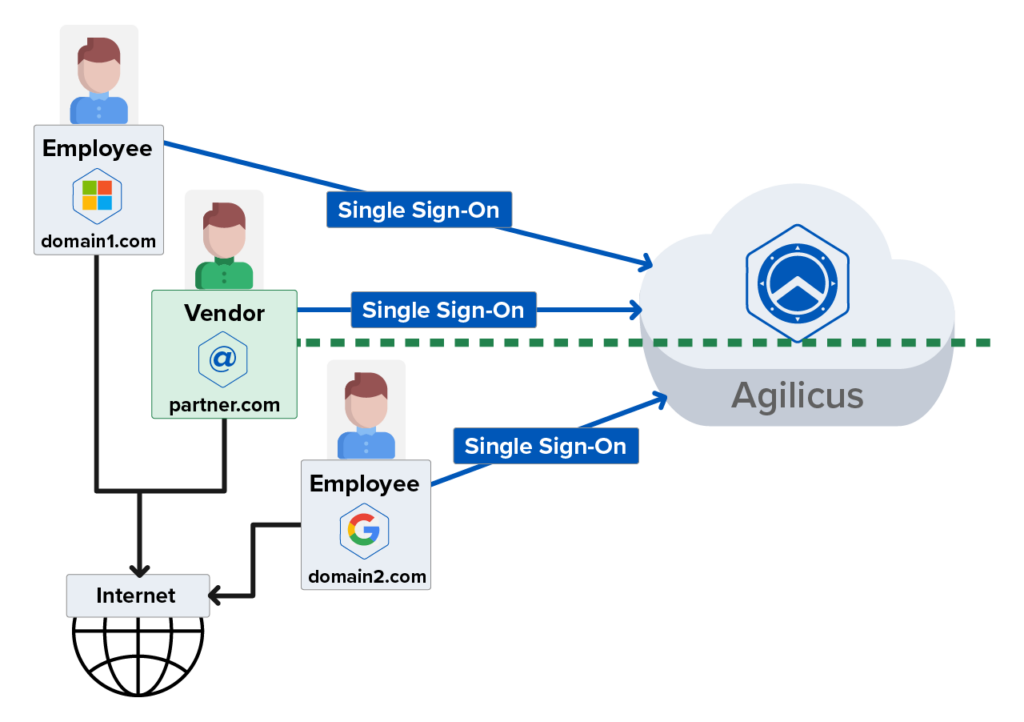
By federating identity, Agilicus AnyX allows an unlimited number of corporate email addresses, from different organisations, to work together as if they were part of the same organisation. The result is a streamlined and frictionless login process delivered through a familiar single sign-on process. Easily on board employees, contractors, vendors, and partners without requiring any new usernames, passwords, or active directory licences. Resources are only visible and available once a user’s identity is asserted by a trusted identity provider and their access level is confirmed.
No Client. No VPN. No Network Changes.
No need to roll-out user apps or deal with version issues
Access from Unmanaged devices
Flexible access for laptops, desktops, smartphones
Eliminate Shared Credentials
Use an individual’s existing credentials to enable access
Multi-Factor Authentication
Enable on Non-Participating Systems
No New User-IDs or Passwords
No passwords stored in system
Single Sign-On
One set of credentials for access
hat is Federated Identity?
Federated identity is a means of unifying user access across multiple domains, allowing each individual to gain access to multiple applications and resources using a single set of credentials.
Centrally Manage User Permissions and Adopt Least Privilege Access
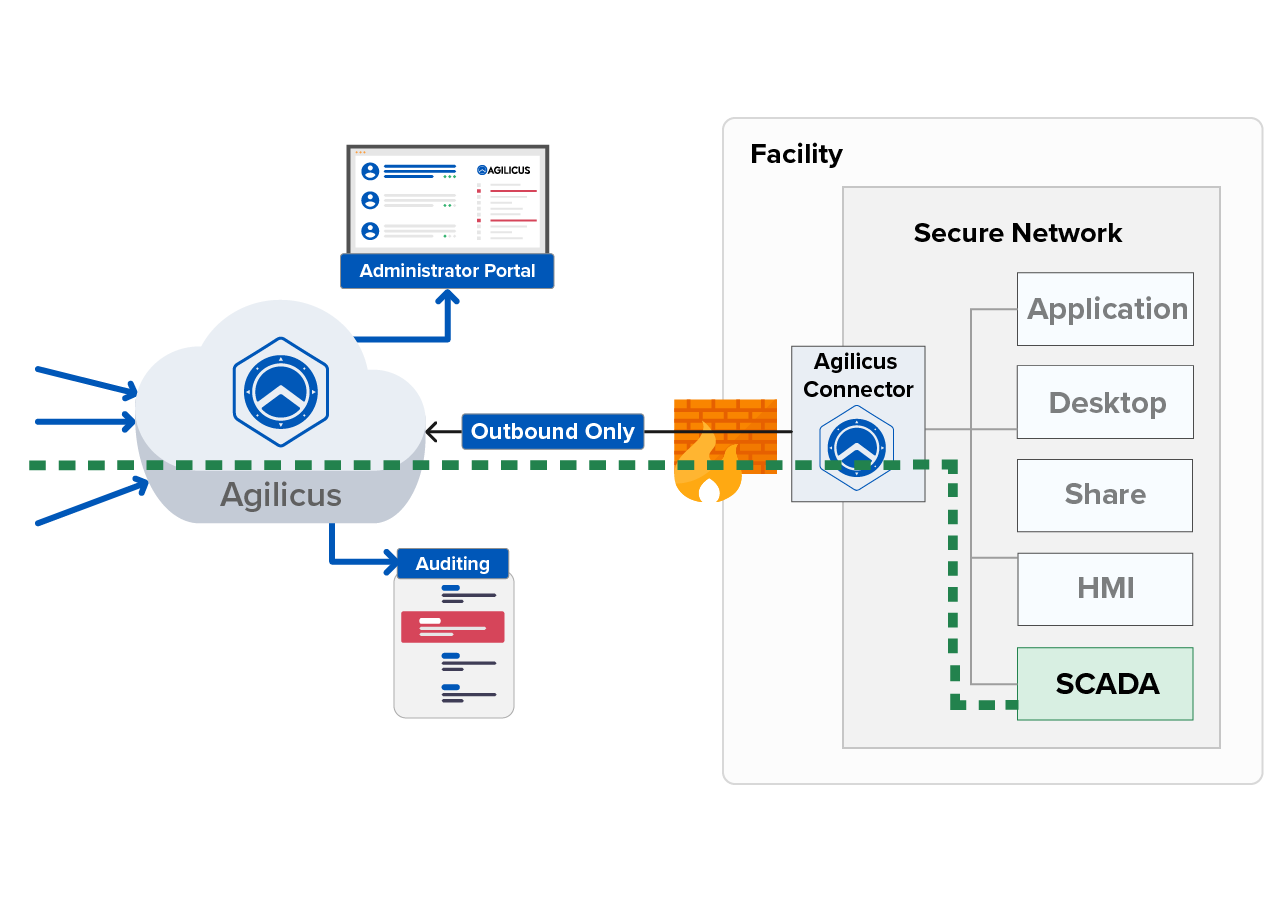
Authentication is all about your users attesting who they are by verifying their identity. Authorization is about what they can do with your resources. Agilicus AnyX leverages fine-grained authorisation and role-based access controls to ensure your organisation has precise control over every user and resource permission.
Every resource (network, server, application, etc.) has a set of permissions that are both role and resource specific – Owner, Editor, Viewer, Self. Whether you need to manage permissions for a single user or group of users, you can easily delegate, add, or revoke the necessary privileges across all of your users and resources through Agilicus AnyX.
Detailed Auditing
Complete visibility of who is doing what, when, and for how long
Off the Public Internet
Resources are hidden from discovery
Resource Segmentation
Segment resources down to the application level
Outbound Only Connection
No inbound access allowed
Enhanced Security
Protects OWASP Top 10, E2E Encryption, SSL/TLS
Fine-Grained Authorisation
Enforce least privilege access
Ensure users are paired with only the resources they need and restrict what they can do with that access through Agilicus AnyX. Get in touch with our team and learn how Agilicus works to enable least privilege access while micro segmenting users and resources down to the application level.
What is Fine-Grained Authorisation?
Typically permissions and authorisation have been handled in a coarse-grained fashion, per resource or application. With fine-grained authorisation, organisations have granular control over privileges and permissions with the ability to precisely define and enforce distinct rules and policies for each user or group of users. Gaining control of permissions through fine-grained authorisations with Agilicus AnyX means organisations can more effectively adopt and enforce least privilege access to enhance security and reduce cyber risk.
Simple Access for Frictionless Collaboration
Agilicus AnyX delivers cloud-native security that ensures authorised users get secure, frictionless access to applications, desktops, shares, and other corporate resources and services. The platform is designed to reduce complexity and drive greater collaboration across departments and between organisations.
End users, whether employee or non-employee, will always be greeted by a familiar login experience and don’t need to manage new accounts or credentials. Likewise, administrators and IT teams have greater visibility and control with the ability to create user resource pairings, keep key systems off the public internet, and leverage enhanced audit logging to enhance security organisation-wide.
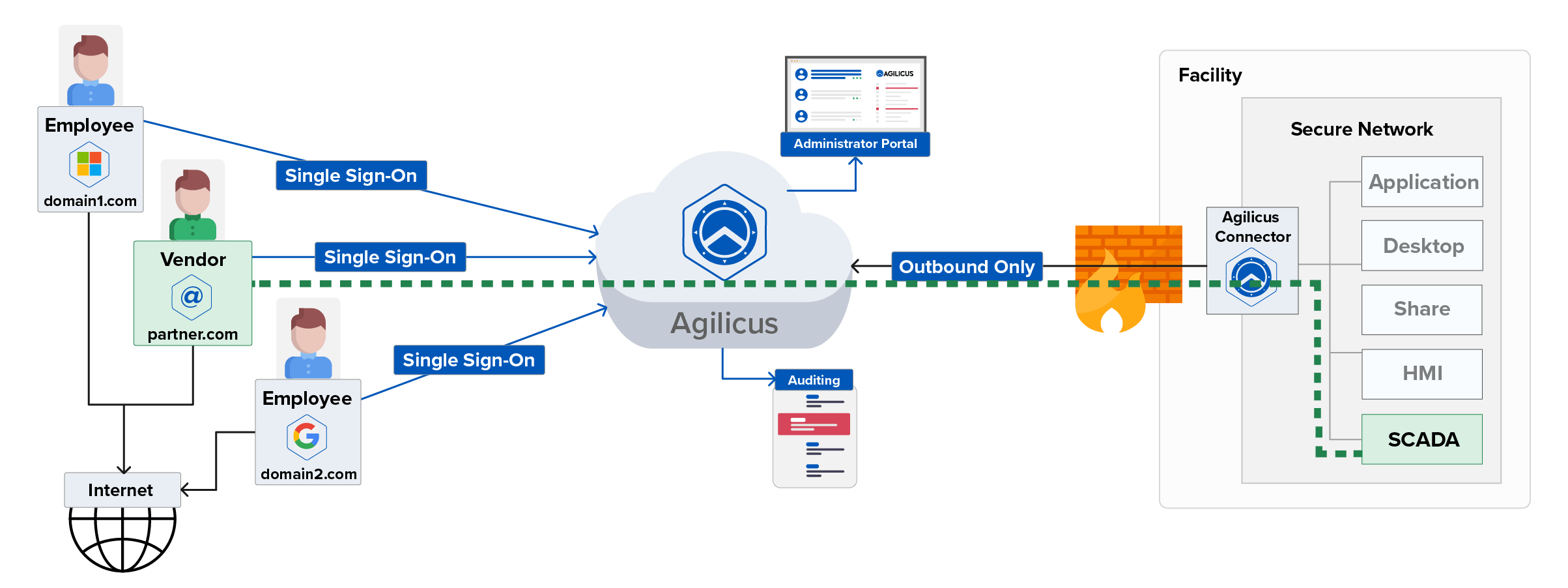
How Agilicus AnyX Secures Critical Systems
Information Technology Use Cases
Organisations need to achieve minimum security compliance objectives for industry specific or cyber insurance requirements. Conventional solutions, like the VPN, increase costs, do not satisfy requirements, are difficult to scale, and add unwanted operational overhead.
Operational Technology Use Cases
Vendors and employees need secure access to systems where uptime is critical to business: SCADA, HMIs, Industrial Control Systems, and other operational technologies.
Protect vulnerable systems and ensure safe operations
Avoid remote control systems solutions (TeamViewer) which give broad access
Provide secure, auditable remote connectivity to individual systems to ensure uptime
Meet multi-factor authentication and privilege access management requirements
Air-gap OT resources from IT and public networks
Eliminate inbound connections and avoid compromising air-gap with VPNs, Jumpbox, DMZ
Have a detailed audit of who does what, when, and what is the exposure
Deploy reliable access, not susceptible to network changes
Multi-factor authentication on non-participating systems and external users
Implement privilege access management
Enforce policies across third parties or vendors
Eliminate shared credentials
Eliminate perimeter based security approaches like VPNs
Enforce end-to-end encryption, TLS, and SSL on every connection
Detailed audit of who did what, when, and what is the exposure
Eliminate use of remote control systems (RDP, etc.)
Enhance Security and Reduce Cyber Risk with Agilicus AnyX
Enact strict, least privilege access for your employees with Agilicus AnyX. You can give users access to the applications they need with the ability to monitor and manage all activity through detailed audit logs. Behind the scenes all users and resources are segmented from each other and hidden from the public internet preventing an intruder’s ability to move east-west within a network. Without the ability to hop across resources, organisations benefit from a matured cyber posture and can very effectively limit the blast radius of any breach.
Get in touch with our team or read the white paper and learn how to enhance security with a Zero Trust Architecture through Agilicus AnyX.
Get In Touch
Ready To Learn More?
Agilicus AnyX Zero Trust enables any user, on any device, secure connectivity to any resource they need—without a client or VPN. Whether that resource is a web application, a programmable logic controller, or a building management system, Agilicus can secure it with multi-factor authentication while keeping the user experience simple with single sign-on.