WHITE PAPERS
Zero Trust with Agilicus AnyX
Learn how organisations are using Agilicus AnyX to adopt Zero Trust. Read more about industry best practices with our white papers, and learn why the platform stands out when it comes to enhancing security with our brochures.
White Papers
-

Agilicus AnyX Configuration Security
Cloud Configuration: What is the exposure? How is it protected? Learn how Agilicus AnyX is more secure than an on-premise system.
-

Secure Remote Updates For Air-Gapped Systems
Challenges with, and solutions for, Secure Remote Updates in modern complex control systems deployed in locked-down, air-gap-style networks. Agilicus AnyX enables and secures remote updates for air gaps.
-
High Availability Dual WAN Remote Industrial Connectivity
Industry cannot stop. Industry is also commonly located in remote areas with less network connectivity choices. Learn how Agilicus AnyX facilitates High Availability Dual WAN Remote Industrial Connectivity.
-
Subscription Model and Remote Access In Industrial Control
Subscription Model and Remote Access In Industrial Control. The quest for revenue creates risks for operation.
-
Merging Local Identity With Online Identity
Modern online Identity with Azure, Google, Okta. Manufacturing plants with Local Identity — onsite users Unify with Agilicus AnyX
-

NIST SP 800 53 Mapping To Zero Trust
NIST SP 800 53 Mapping To Zero Trust. NIST SP 800 53 is a comprehensive set of security controls. Zero Trust Network Architecture is a technology. Explore the intersection.
-
NIST SP 800-53 in Critical Infrastructure
NIST SP 800-53 is a core part of the NIST cybersecurity framework. It provides mappings of controls to various other standards. Zero Trust is a complementary architecutre supporting these controls.
-
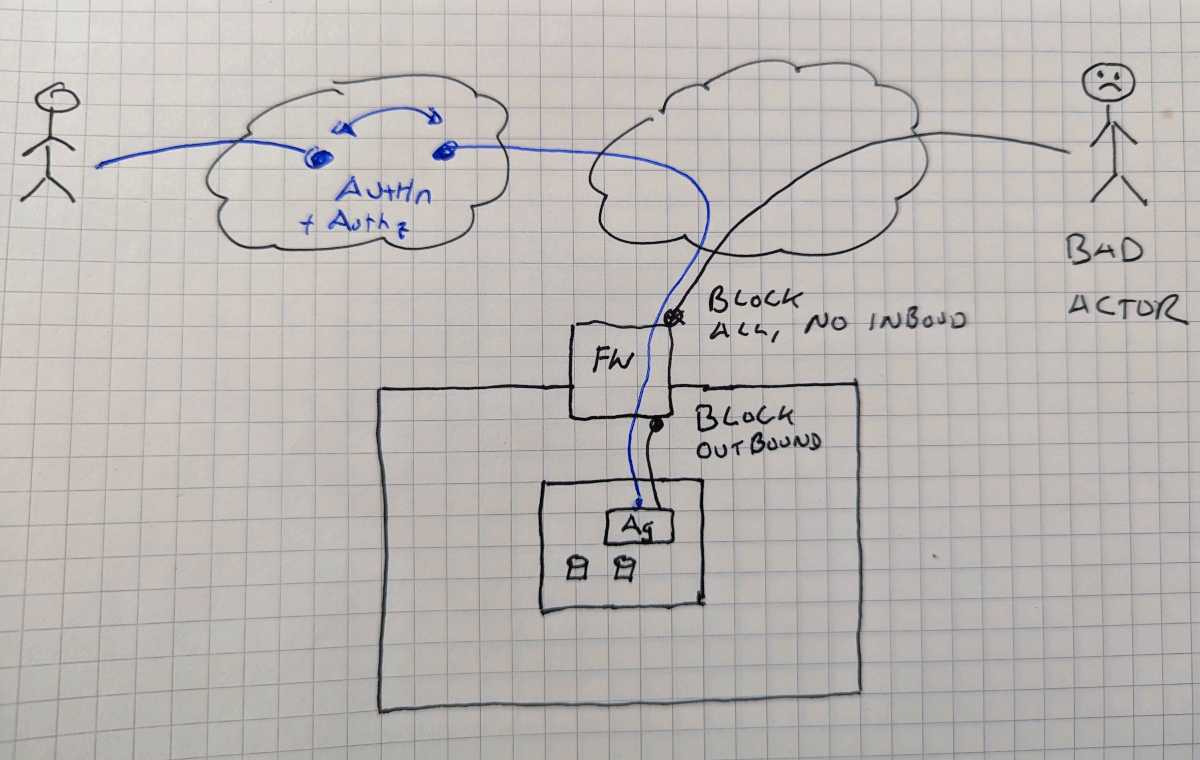
Zero Trust Air Gap Lock Down Inbound and Outbound
Air Gaps are a useful but inconvenient tactic as a part of a defense in depth strategy. Learn how a Zero Trust Air Gap Lockdown Inbound and Outbound can provide convenience and security together.
-
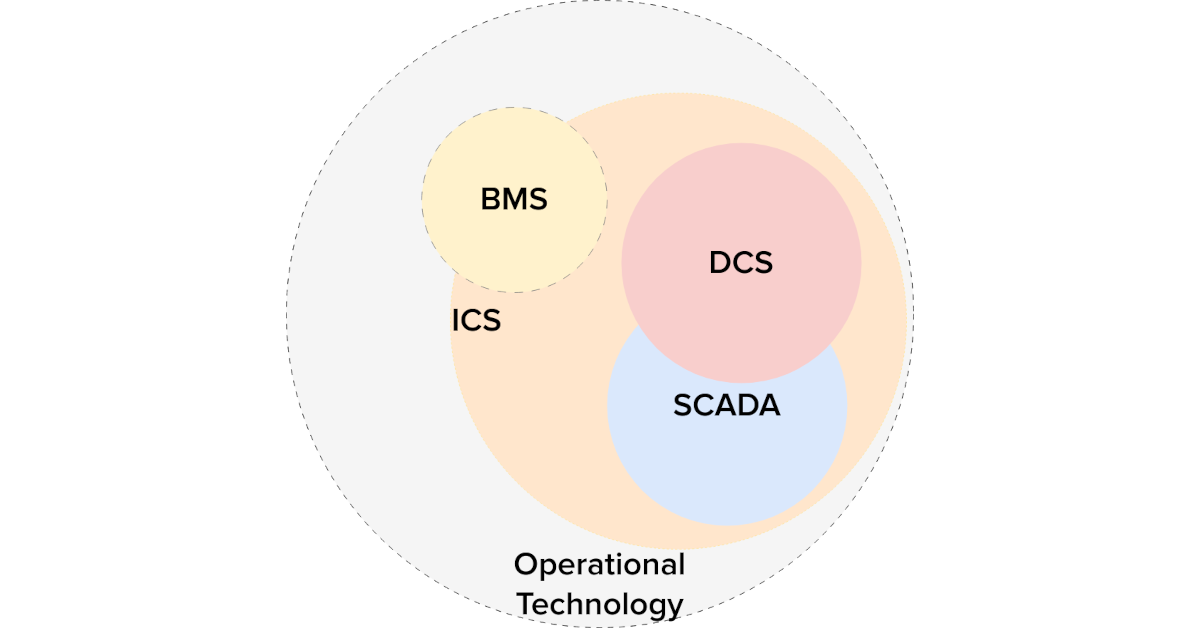
Piercing The Purdue Model: Zero-Trust In Operational Technology
Unravelling the interaction between the Purdue Model and Zero Trust: When married together in operational technology, the outcomes can be transformative.
-

Multi-Factor Authentication On The Internal Network
Cyber-Insurance compliance require multi-factor on internal network resources? Routers? Servers? Learn how to implement without a VPN, without changes.
-
Industrial Zero-Trust Micro-Segmentation
Micro-Segmentation Zones are a best practice for Industrial Control security. Simplify and increase effectivity with identity-based Zero-Trust. Industrial Zero-Trust Micro-Segmentation
-

Eliminate Attack Vectors and Stop Cyber Threats in Their Tracks with a Zero Trust Architecture
Eliminate Attack Vectors and Stop Cyber Threats in Their Tracks with a Zero Trust Architecture. Cyber threats come from all angles these days, yet most businesses are still ill equipped to properly keep the bad actors out.
-

Remote Desktop Access: Managing Cyber Risk with Zero Trust Network Access
Eliminate unmanaged cyber risk by securing remote desktop access through zero trust network access and improve your cybersecurity posture.
-

Azure Application Consent
The Agilicus AnyX platform uses external Identity Providers rather than creating ‘parallel’ identities for users to remember. What permissions are being granted on those upstream systems?
-

Starlink Port Forwarding
Starlink. Good enough except for starlink port forwarding. Reach your devices from remote with Agilicus, securely, simply, reliably.